Security Assertion Markup Language (SAML) is an XML-based markup language for exchanging authentication and authorization between an identity provider (IdP) and a Service Provider (SP). SAML is important to your organization as you move more towards relying on hosted services, as it provides a single point of authentication at IdP. The credentials are not stored on multiple untrusted devices, as SAML is used to assert the identity. Another benefit lies in the user experience, as users do not have to remember multiple credentials to access their apps. They can access multiple applications with a single set of credentials by logging in once.
Configuring the Authentication Profile using UI
Navigate to .
Click Create.
Enter the Name for the Auth profile.
Select SAML as the Type of Auth profile.
Select Use IDP Metadata or Use IDP Metadata URL as required and enter the metadata from your IdP.
Note:It is recommended to select Use IDP Metadata URL option. If you use both the options, the Use IDP Metadata URL option takes precedence.
Any node acting as a service provider must generate a metadata file for registration with the IdP. The file contains configuration and integration details for SAML single sign-on. Obtain the metadata file from your identity provider.
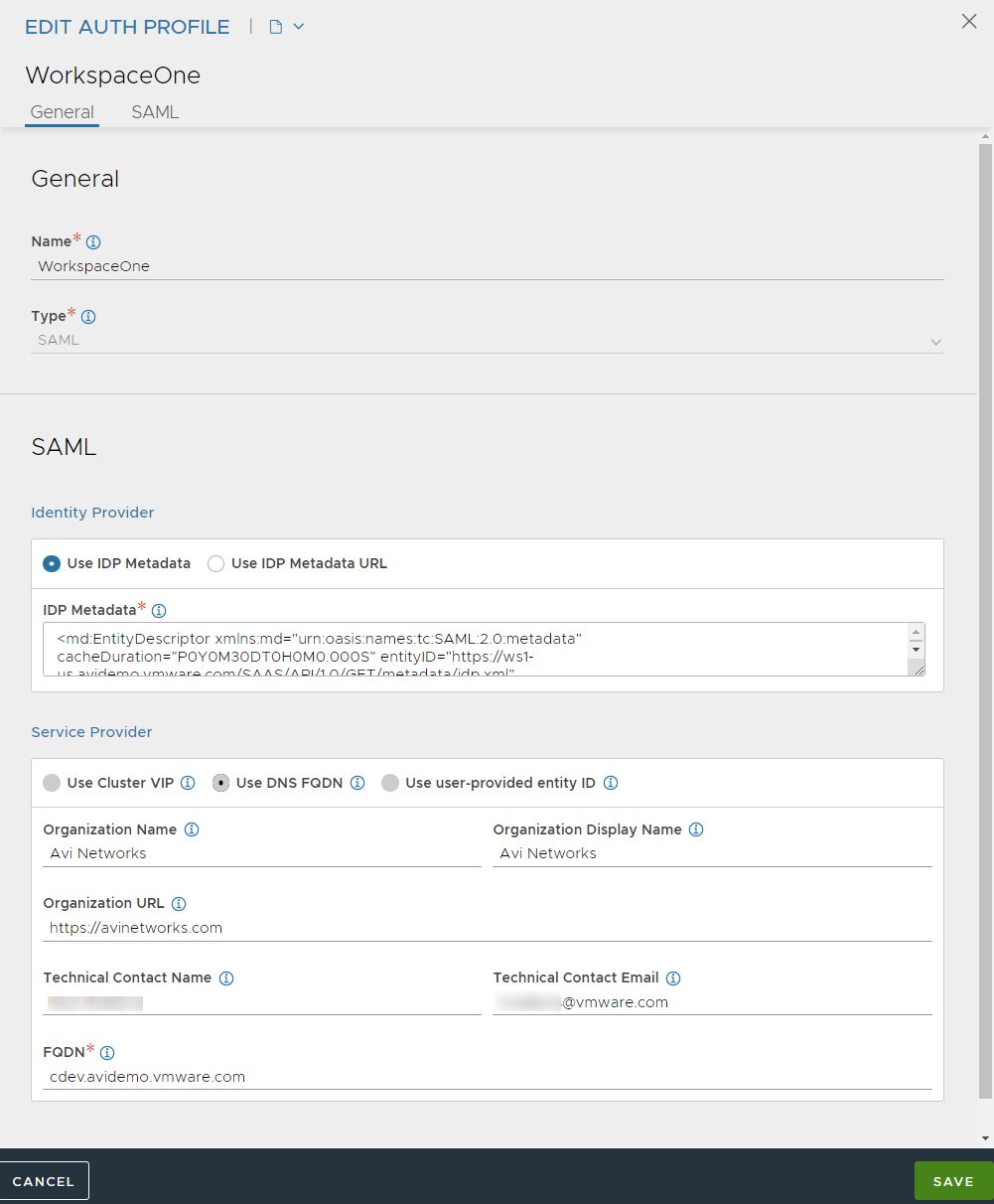
Under Service Provider, select Use Cluster VIP or Use DNS FQDN, as required and enter details.
Note:Service provider metadata contains keys, services, and URLs defining SAML endpoints of the Avi Load Balancer Controller. The Controller can be registered using its cluster VIP or a DNS-resolvable FQDN.
If Use Cluster VIP is selected, then the cluster VIP is picked up automatically. Cluster VIP is the virtual IP address of the Controller cluster.
If Use DNS FQDN is selected, Avi Load Balancer Controller prompts to provide an FQDN. DNS FQDN is the FQDN name of the Controller cluster.
Use user-provided entity ID option is not applicable for Controller Authentication. It is only used for Client Authentication (L7 Virtual Service Authentication).
Click Save.
Configuring the Authentication Profile using CLI
Configure the Auth Profile using the CLI commands shown below:
[admin:saml-ctrlr-1]: > configure authprofile Saml-auth-profile [admin:saml-ctrlr-1]: authprofile> type auth_profile_saml [admin:saml-ctrlr-1]: authprofile> saml [admin:saml-ctrlr-1]: authprofile:saml> sp [admin:saml-ctrlr-1]: authprofile:saml:sp> saml_entity_type auth_saml_app_vs [admin:saml-ctrlr-1]: authprofile:saml:sp> save [admin:saml-ctrlr-1]: authprofile:saml> save [admin:saml-ctrlr-1]: authprofile> saml [admin:saml-ctrlr-1]: authprofile:saml> new idp metadata : ‘metadata_string’
A sample configuration is shown below:
metadata: ‘<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.okta.com/exk2c02xxTcM9pIr0355"><md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate>MIIDtjCCAp6gAwIBAgIGAWPuJWSOMA0GCSqGSIb3DQEBCwUAMIGbMQswCQYDVQQGEwJVUzETMBEG A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU MBIGA1UECwwLU1NPUHJvdmlkZXIxHDAaBgNVBAMME2F2aW5ldHdvcmtzLWF1dGhsYWIxHDAaBgkq hkiG9w0BCQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwNjExMDkxOTE4WhcNMjgwNjExMDkyMDE3WjCB mzELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lz Y28xDTALBgNVBAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRwwGgYDVQQDDBNhdmluZXR3 b3Jrcy1hdXRobGFiMRwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0B AQEFAAOCAQ8AMIIBCgKCAQEAiFKBy70aa5G2I5JH+uUqXef9jrhUtx6CX1nmrg26FXtsKYdjRm5v otxbjfNdcXeXRXHu5scMwAgMy9EZM+AXehlm/qnahNWvEZ+YgPZS55UzkcSXJ30dl62kbUAyXxo3 CQQs+Hj5k7W0rcZAj405qxOZVgtkrs6cB3uS/pn02eV4EHA6ECReQLrEPFcy6zLZpIChbkzyz372 ZLbwMCSjF5DLh52MSGgWixwvs5Mq20WofBWMOnS0ofnZq6+TM6XK7P8VEQxJe37sWi0W+RrR6685 T+bnlM6GMg24wRHt/1fouUbZQuBgoc0/HNKywlO9BXLoJ9j02/VYn3Uex9bumQIDAQABMA0GCSqG SIb3DQEBCwUAA4IBAQAmAh0fXL7gU1ivV3hWdl0AlLPENREAzKbHwuthtTySBr6rmreo6j8SvOMW pKQzNznmzU3zyeLd96j6lfA7PIDGyBGmNB6z0Va0bPvOQe+a2f3/cmumVdrKFv7I5ZiR0UNbeBmG BIeWkJ+Rx+FcaIzP2IiFddmvpdh1nLae7FS9F1jvnioSIwq2PlFZuMMFb2TrMXrqqEMp9CeGfEag bjxQcWEW1ifNxeKrI/LcS5g5mTf4gx41bgo/w9x6MRsK+bIbYv680mdtb6LhWiT1lZU+ZAYJTKMr HHoIxYFPW8Zcs7DGirOOYMbSU97G0rljQzbv9gcS+FhwPffBaHi3spk9</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://avinetworks-authlab.okta.com/app/avinetworksorg108212_apmssotest_1/exk2c02xxTcM9pIr0355/sso/saml"/><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://avinetworks-authlab.okta.com/app/avinetworksorg108212_apmssotest_1/exk2c02xxTcM9pIr0355/sso/saml"/></md:IDPSSODescriptor></md:EntityDescriptor>’
Complete the CLI sequence with two save commands.
[admin:saml-ctrlr-1]: authprofile:saml> save [admin:saml-ctrlr-1]: authprofile> save +----------------------+----------------------------------------------------------------------------------+ | Field | Value | +----------------------+----------------------------------------------------------------------------------+ | uuid | authprofile-789ce4af-6b9d-4a73-bd26-d00f670a19c0 | | name | Saml-auth-profile | | type | AUTH_PROFILE_SAML | | saml | | | idp | | | metadata | <?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:n | | | ames:tc:SAML:2.0:metadata" entityID="http://www.okta.com/exk2c02xxTcM9pIr0355">< | | | md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration=" | | | urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInf | | | o xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate | | | >MIIDtjCCAp6gAwIBAgIGAWPuJWSOMA0GCSqGSIb3DQEBCwUAMIGbMQswCQYDVQQGEwJVUzETMBEG A1 | | | UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU MBIGA | | | 1UECwwLU1NPUHJvdmlkZXIxHDAaBgNVBAMME2F2aW5ldHdvcmtzLWF1dGhsYWIxHDAaBgkq hkiG9w0B | | | CQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwNjExMDkxOTE4WhcNMjgwNjExMDkyMDE3WjCB mzELMAkGA1U | | | EBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lz Y28xDTALBgNVBA | | | oMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRwwGgYDVQQDDBNhdmluZXR3 b3Jrcy1hdXRobGFiM | | | RwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0B AQEFAAOCAQ8AMIIBCgKC | | | AQEAiFKBy70aa5G2I5JH+uUqXef9jrhUtx6CX1nmrg26FXtsKYdjRm5v otxbjfNdcXeXRXHu5scMwAg | | | My9EZM+AXehlm/qnahNWvEZ+YgPZS55UzkcSXJ30dl62kbUAyXxo3 CQQs+Hj5k7W0rcZAj405qxOZVg | | | tkrs6cB3uS/pn02eV4EHA6ECReQLrEPFcy6zLZpIChbkzyz372 ZLbwMCSjF5DLh52MSGgWixwvs5Mq2 | | | 0WofBWMOnS0ofnZq6+TM6XK7P8VEQxJe37sWi0W+RrR6685 T+bnlM6GMg24wRHt/1fouUbZQuBgoc0/ | | | HNKywlO9BXLoJ9j02/VYn3Uex9bumQIDAQABMA0GCSqG SIb3DQEBCwUAA4IBAQAmAh0fXL7gU1ivV3h | | | Wdl0AlLPENREAzKbHwuthtTySBr6rmreo6j8SvOMW pKQzNznmzU3zyeLd96j6lfA7PIDGyBGmNB6z0V | | | a0bPvOQe+a2f3/cmumVdrKFv7I5ZiR0UNbeBmG BIeWkJ+Rx+FcaIzP2IiFddmvpdh1nLae7FS9F1jvn | | | ioSIwq2PlFZuMMFb2TrMXrqqEMp9CeGfEag bjxQcWEW1ifNxeKrI/LcS5g5mTf4gx41bgo/w9x6MRsK | | | +bIbYv680mdtb6LhWiT1lZU+ZAYJTKMr HHoIxYFPW8Zcs7DGirOOYMbSU97G0rljQzbv9gcS+FhwPff | | | BaHi3spk9</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md: | | | NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFor | | | mat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md: | | | NameIDFormat><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindin | | | gs:HTTP-POST" Location="https://avinetworks-authlab.okta.com/app/avinetworksorg1 | | | 08212_apmssotest_1/exk2c02xxTcM9pIr0355/sso/saml"/><md:SingleSignOnService Bindi | | | ng="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://avinet | | | works-authlab.okta.com/app/avinetworksorg108212_apmssotest_1/exk2c02xxTcM9pIr035 | | | 5/sso/saml"/></md:IDPSSODescriptor></md:EntityDescriptor> | | sp | | | saml_entity_type | AUTH_SAML_APP_VS | | tenant_ref | admin | +----------------------+----------------------------------------------------------------------------------+ [admin:saml-ctrlr-1]: >
Note:For more information on CLI access for SAML using Token authentication, see Token Authentication.
Verify Service Provider Settings for SAML Auth Profile
Avi Load Balancer supports single sign-on (SSO) to the Avi Load Balancer Controller’s UI using SAML.
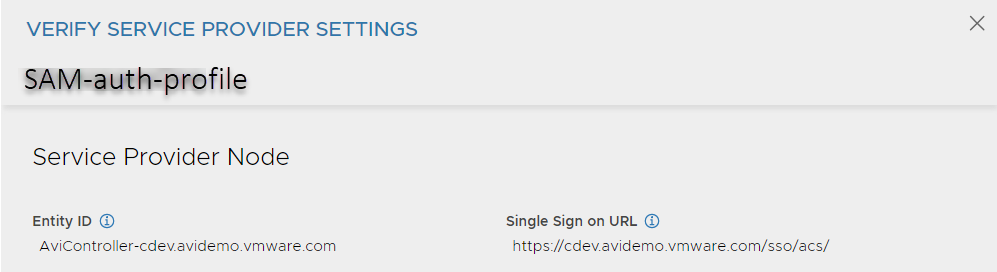
Service provider settings can be retrieved by clicking the verify button (Tick icon) on the Auth Profile list page. This page contains the service provider Entity ID and the Single Sign on URL generated by the Avi Load Balancer Controller.
Local Admin or User Logon
After SAML-based access is enabled, you can have the Avi Load Balancer web console display the logon UI without redirecting to the SAML authentication profile configured on the IdP logon page. To accomplish this, send a URL to the Controller or cluster IP address in one of the following two forms:
https://ControllerIP/#!/login?local=1
https://FQDN/#!/login?local=1