TCP SYN attack is a DDOS attack in which the attacker uses the three-way TCP handshake process to attack the server.
Many TCP SYN requests are sent, and when the server or the target device responds with SYN-ACK, there is no ACK response causing a vast number of half-opened TCP connections. By repeatedly sending connection request (SYN) packets, the attacker can overwhelm all available ports on a targeted server machine, causing the targeted device to respond to legitimate traffic sluggishly or not at all.
TCP SYN Flood Attack Mitigation on Avi Load Balancer
Avi Load Balancer supports TCP SYN flood detection and mitigation without any user intervention. Before the Avi Load Balancer release 20.1.3, the synseen_entries_thresh parameter is used to assign a threshold value for the SYN packets. Once the synseen_entries_thresh is exceeded, new SYN packets are dropped, resulting in a denial of service of legitimate connection requests. The calculation of synseen_entries_thresh is based on the number of cores. In the case of an extensive system, the synseen_entries_thresh is above 1 million.
If a SYN attack happens, Avi Load Balancer looks up the flow table or connection table before it starts dropping connection. Avi Load Balancer uses various metrics and events to detect TCY SYN attacks. This helps avoid rejection or closure of legitimate TCP connections or requests.
TCP SYN flood attack is mainly aimed at memory resource exhaustion. Each SYN packet will result in the allocation of memory to keep the state of the embryonic connections. Avi Load Balancer mitigates SYN flood using a solution based on SYN cookies. Once the number of embryonic connections exceeds a limit, the TCP/IP stack or other components stop allocating memory till a connection is fully established. The limit is available as a configurable flow_table_new_syn_max_entries under the SE group properties. The default value for the flow_table_new_syn_max_entries parameter is 40000.
Metrics and Events
When a TCP SYN Attack is detected, Avi Load Balancer generates logs related to the TCP SYN Attack for the same.
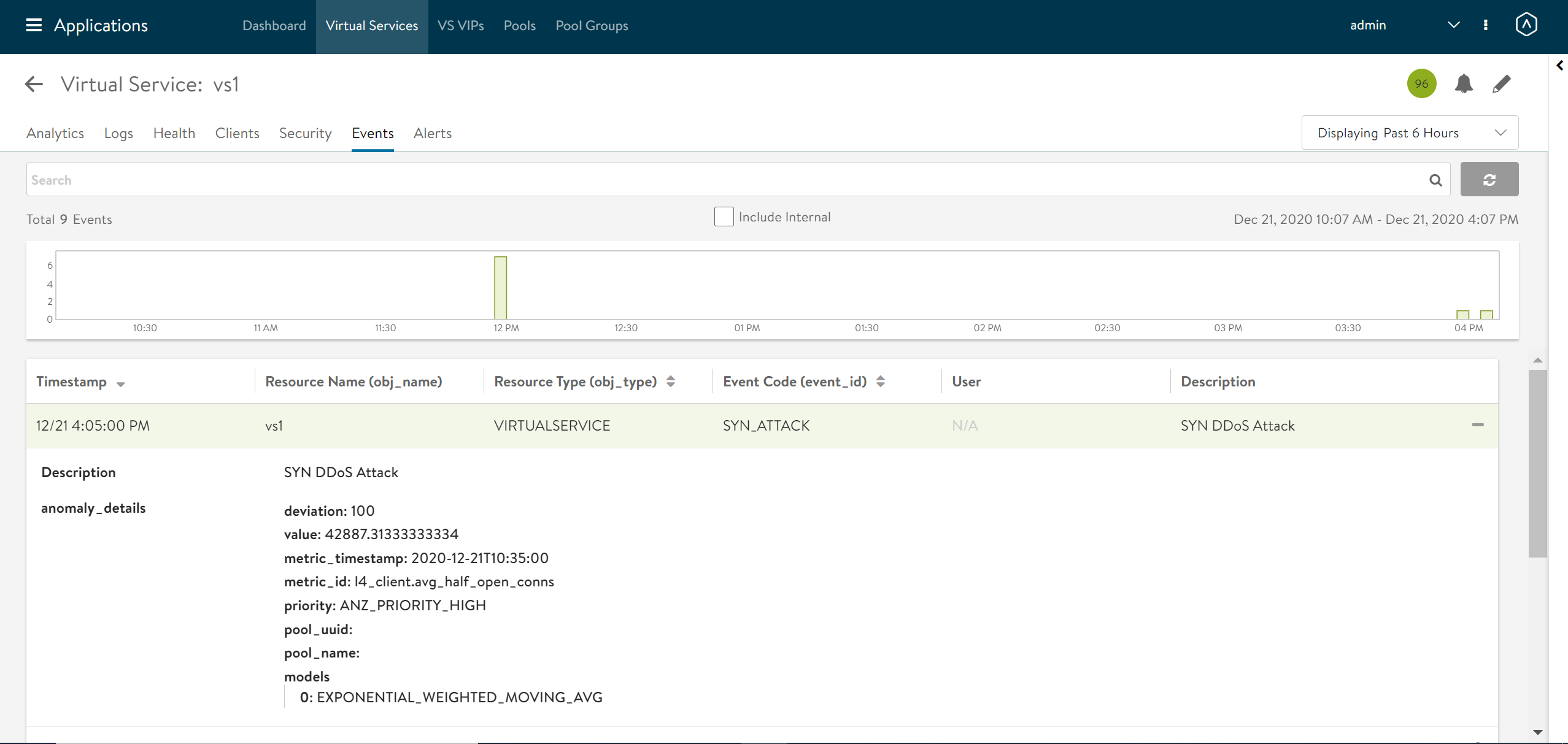
Navigate to , and select the Events tab to check the events associated with TCP SYN Attack for the specific virtual service. The following screenshot shows the virtual service vs1 is under TCP SYN Attack:
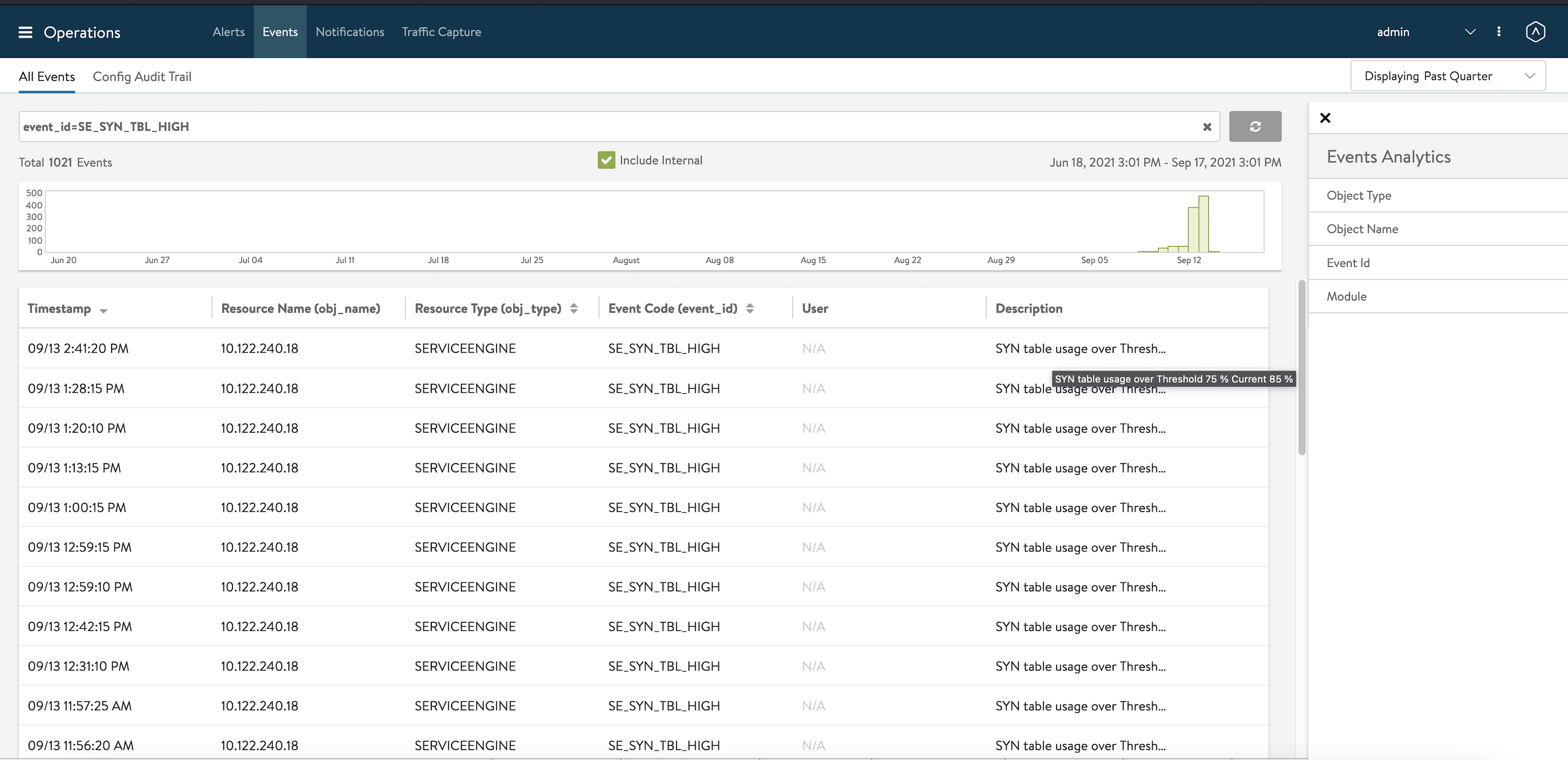
SE_SYN_TBL_HIGH Alert
When SE Limits are breached for total SYN that can be in TCP SYN FLOOD traffic, the Controller will display an alert message as SE_SYN_TBL_HIGH.