In most deployments, Avi Load Balancer is directly exposed to public, untrusted networks. To protect application traffic, Service Engines (SEs) are able to detect and mitigate a wide range of Layer 4-7 network attacks.
The following is a list of common denial of service (DoS) attacks and directed DoS (DDoS) attacks mitigated by Avi Load Balancer.
Attack Layer |
Attack Name |
Description |
Mitigation |
|---|---|---|---|
Layer 3 |
SMURF |
ICMP packets with the destination IP set as the broadcast IP and the source IP spoofed to the victim’s IP. |
Packets are dropped at the dispatcher layer if the source or destination IP is a broadcast IP or class D/ E IP address. |
ICMP Flood |
Excessive ICMP echo requests to the victim. |
ICMP packets are rate limited. |
|
Unknown protocol |
Packets with unrecognized IP protocol. |
Packets are dropped at the dispatcher layer. |
|
Tear drop |
Exploit the reassembly of fragmented IP packets. |
Packets are dropped in the protocol stack in the SE if fragment offsets are deemed bad. |
|
IP fragmentation |
Bad fragmented packets. |
Packets are dropped in the protocol stack in the SE. |
|
Layer 4 |
SYN flood |
Send TCP SYNs without acknowledging SYN-ACK; the victim’s TCP table will grow rapidly. |
If the TCP table is being filled with half connections, like uncompleted TCP 3-way handshakes, begin using SYN cookies. |
LAND |
Same as SYN flood except the source and destination IP addresses are identical. |
Packets are dropped at the dispatcher layerV. |
|
Port scan |
TCP/ UDP packets on various ports to find out listening ports for next level of attacks; most of those ports are non-listening ports. |
Packets are dropped at the dispatcher layer. |
|
X-mas tree |
TCP packets with all the flags set to various values to overwhelm the victim’s TCP stack. |
Packets are dropped in the protocol stack of the SE. |
|
Bad RST flood |
Send TCP RST packets with bad sequence. |
Packets are dropped in the protocol stack in the SE if the packet sequence numbers are outside the TCP window. |
|
Fake session |
Guess a TCP sequence numbers to hijack connections. |
To reduce the chance of success for a fake session attack, the SE uses random numbers for the initial sequence numbers. |
|
Bad sequence numbers |
TCP packets with bad sequence numbers. |
Packets with sequence numbers outside the TCP window are dropped in the protocol stack in the SE. |
|
Malformed/ Unexpected flood |
Unrelated TCP packets after a TCP FIN has been sent. |
Unexpected packets after the FIN is dropped in the protocol stack in the SE. |
|
Zero/ small window |
Attacker advertises a zero or very small window, <100, after the TCP 3-way handshake. |
If the first TCP packet from the client, after a SYN, is received with a zero or small window, the SE drops the packet and an RST is sent. |
|
Rate limiting CPS per IP |
Connection flood |
The rate limits configured in the application profile are applied. (). |
|
SSL errors |
Inject SSL handshake errors. |
The SE closes the connection after an error. |
|
SSL renegotiation |
Request for renegotiation after establishing an SSL connection. |
Client-triggered renegotiation is deactivated. |
|
Layer 7 (HTTP) |
Request idle timeout |
Establishing a connection without sending an HTTP request. |
The control timeout configured in the application profile is used. (). |
Size limit for header and request |
Resource consumption through long request time |
The header-size limits configured in the application profile are used. (). |
|
Slow POST |
Resource consumption through long request time. |
The body-size limits configured in the application profile are used. (). |
|
SlowLoris/ SlowPost |
Opening multiple connections to the victim by sending partial HTTP requests. |
The header and body timeouts configured in the application profile are used. |
|
Invalid requests |
Invalid header, body, or entity in HTTP request. |
The URI length, header length, and body length limits configured in the application profile are used. |
|
Rate limiting RPS per client IP |
Request flood |
The limit configured in the application profile is used. (). |
|
Rate limiting RPS per URL |
Request flood |
The limit configured in the application profile is used. (). |
|
Layer 7 (DNS) |
DNS Amplification Egress |
The DNS virtual service is targeted by sending very short queries which solicit very large responses, spanning to multiple UDP packets. The DNS virtual services can be made to participate in a reflection attack. The attacker spoofs the DNS query’s source IP and source port to be that of a well known service port on a victim server. |
Any requests coming from a defined range of source ports (well-known ports) will be denied. The range of ports to be denied is configured in the Security Policy. To know how to configure a security policy for DNS Amplification Egress DDoS protection, see Configure Security Policy for DNS Amplification Egress DDoS Protection. |
DNS Reflection Ingress |
Sending DNS Queries with spoofed IP address of the victim resulting in swamping the victim with unsolicited traffic through the DNS server response.s |
Early dropping of unwanted packets, at the dispatcher. |
|
DNS NXDOMAIN Attack |
Attackers send a flood of queries to resolve domains that do not exist. Usually a randomly generated unlikely domain names are used for the attack. |
Detection: Events are raised for the domains/ sub-domains that are under attack. The event also mentions the clients causing the attack. Mitigation (with Manual Configuration):
|
DDoS Insights
The DDoS section on the right of the default security page breaks down distributed denial of service data for the virtual service into the most relevant layer 4 and layer 7 attack data.
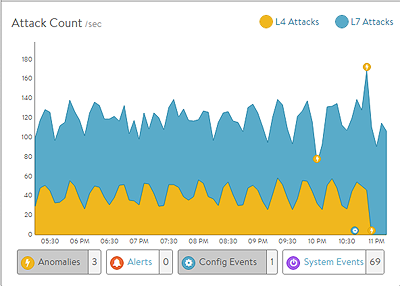
L4 Attacks: The number of network attacks per second, such as IP fragmentation attacks or TCP SYN flood. For the example shown here, each unacknowledged SYN is counted as an attack. (This is the classic signature of the TCP SYN flood attack, a large volume of SYN requests that are not followed by the expected ACKs to complete session setup.)
L7 Attacks: The number of application attacks per second, such as HTTP SlowLoris attacks or request floods. For the example shown here, every request that exceeded the configured request throttle limit is counted as an attack. (See the application profile’s DDoS tab for configuring custom layer seven attack limits.)
Attack Duration: The length of time during which an attack occurred.
Blocked Connections: If an attack was blocked, this is the number of connection attempts blocked.
Attack Count: Shows attacks plotted in a graph over time.