This section discusses creating roles and permissions with different deployment examples.
A role is a group of permissions that can be assigned to members. You can create roles and assign permissions to the roles from the Google Cloud Platform (GCP) console.
The following is a list of GCP specific terminologies used in this topic:
Field |
Value |
|---|---|
GCP Virtual Private Cloud (VPC) provides networking functionality to the GCP resources. |
|
A project organizes all GCP resources. A project consists of a set of users, a set of APIs,and billing, authentication, and monitoring settings for those APIs. |
|
Shared VPC allows an organization to connect resources from multiple projects to a common VPC network. When using a shared VPC, one project is designated as a host project and one or more other service projects can be attached to the host project. Shared VPC is also referred to as XPN.
Note:
The service account will need permission to access shared VPC network. |
|
A service account is a special Google account that belongs to your application or a virtual machine (VM), instead of to an individual end user. Your application uses the service account to call the Google API of a service, so that the users are not directly involved. |
Roles and Permissions in GCP
A role contains a set of permissions that allows you to perform specific actions on Google Cloud resources. To make permissions available to users, groups, and service accounts, you assign roles.
Using Google Cloud's Identity and Access Management (IAM) system you can access resources specific to the roles and this helps prevent access to the other resources.
Role Types
The following are the types of roles in IAM
- Basic roles:
-
This includes the Owner, Editor, and Viewer roles that existed prior to the introduction of cloud IAM.
- Predefined roles:
-
This provides granular access for a specific service and are managed by GCP.
- Custom roles:
-
This provides granular access according to a user-specified list of permissions.
In this case, all instances of Roles refer to Custom Roles.
To know more about creating custom roles, see Creating and Managing Custom Roles.
The following are the cross project deployment scenarios:
The Controller, Service Engine and XPN are in the same project.
The Controller and Service Engines are in Projects other than the XPN.
Option 1 - Controller, Service Engines, and XPN in the same Project
In this deployment scenario, the shared VPC (XPN), the Controller, and the Service Engines are in project A as explained below:
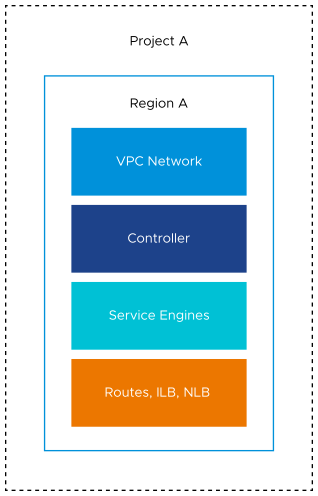
Roles and Permissions for the Virtual Machine
From the GCP cloud console, navigate to and click CREATE SERVICE ACCOUNT.
The Controller
When using a default Compute Engine service account (a project has Compute Engine Service Account enabled), select that as the service account and provide
Read Writepermissions for Compute Engine API as shown in the following image: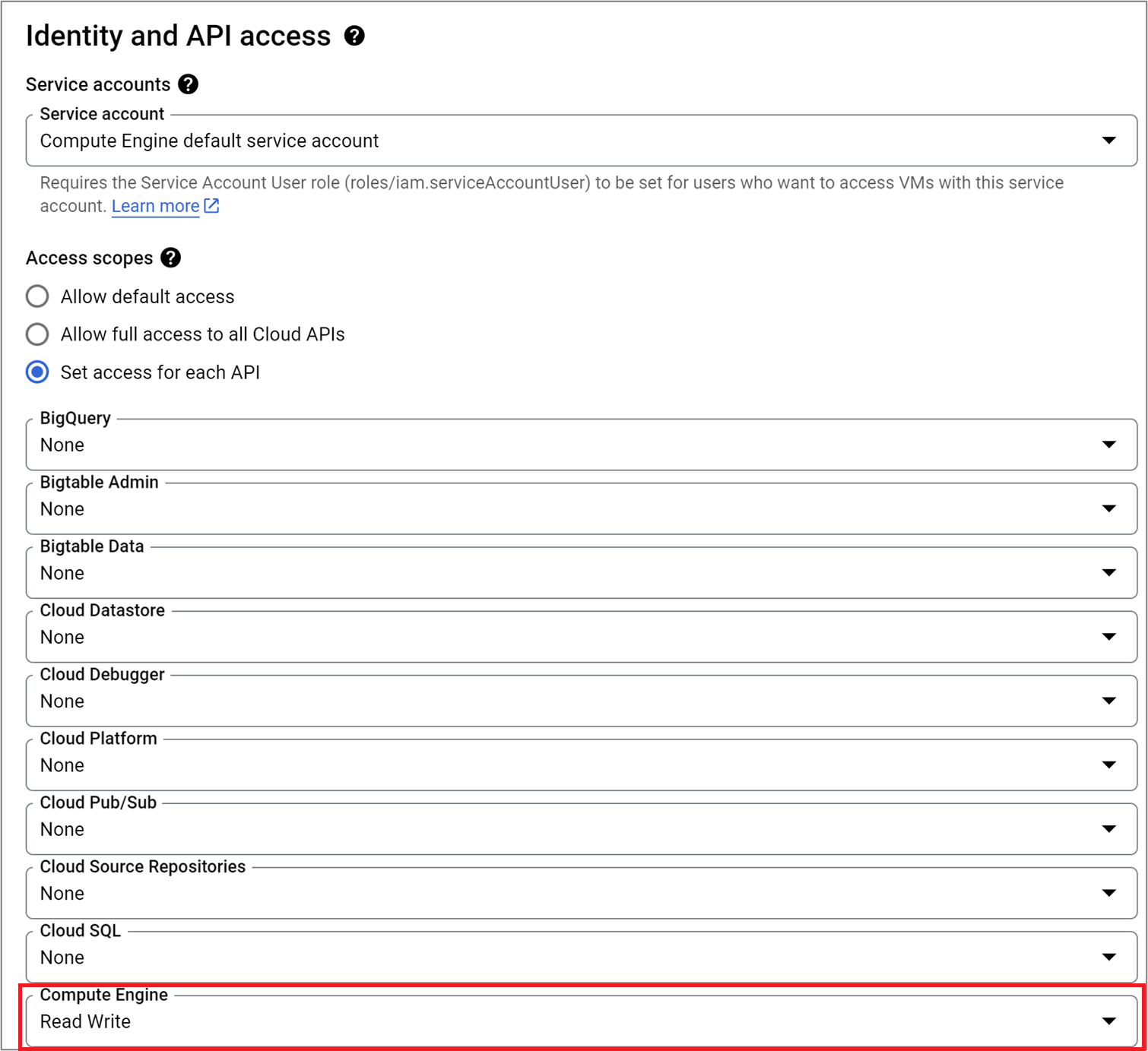
Service Engine
When using default Compute Engine service account (a project has Compute Engine Service Account enabled), select that as the service account and provide
Read Onlypermissions for Compute Engine API, as shown in the following image: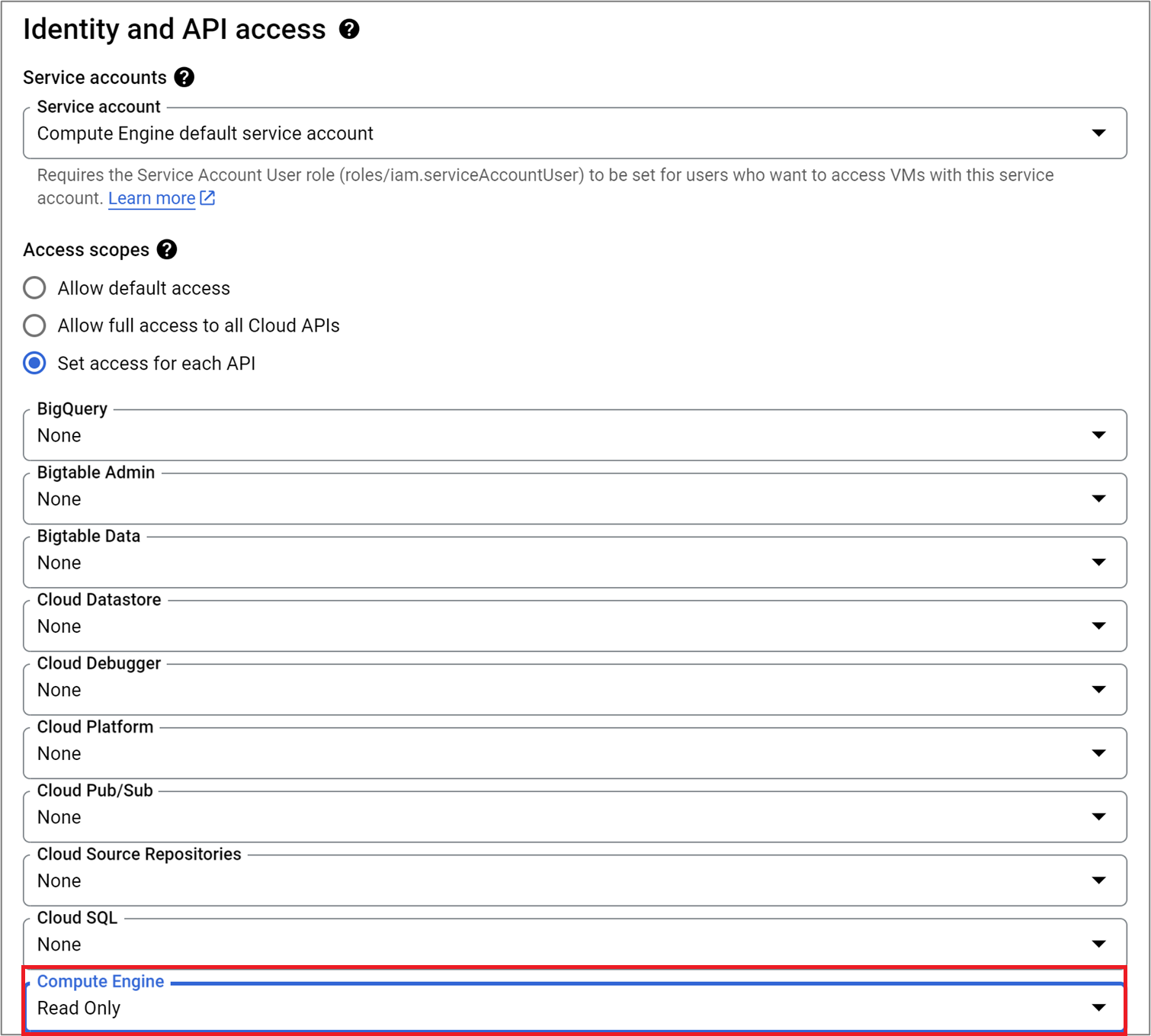
Configuring IPAM
Use the inputs below to configure IPAM.
Field |
Value |
|---|---|
usable_network_uuids |
Network ID for VIP allocation |
network_host_project_id |
|
se_project_id |
Project A (Project Name of the SEs) |
region_name |
Region A (Region Name of the SEs) |
vpc_network_name |
Option 2 - The Controller and Service Engines are in Projects other than the XPN
In this deployment example Shared VPC is in Project A and the Controller, and Service Engines are in Project B.
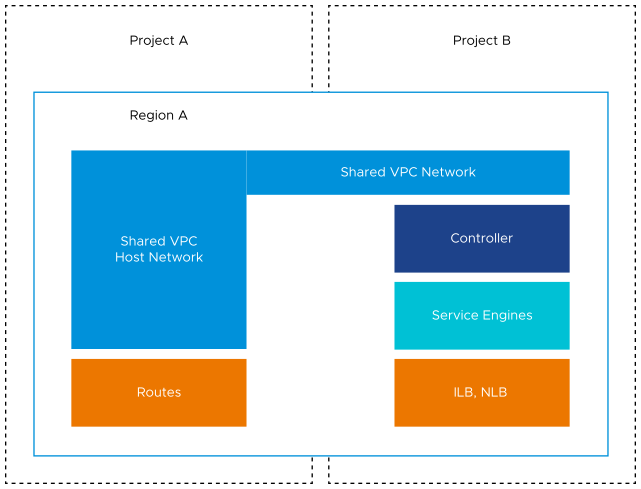
Configuring IPAM
Field |
Value |
|---|---|
usable_network_uuids |
AVI Network ID for VIP allocation |
network_host_project_id |
Project A (Shared VPC Project ID) |
se_project_id |
Project B (Project ID of the SEs) |
region_name |
Region A (Region Name of the SEs) |