Prerequisites
- Verify that you have Helm charts VMware-Bare-Metal-Automation-Remote-Worker-Chart-3.1.0-v2023.2.459-b6.tgz for the VMware BMA Remote Worker from VMware download page.
Note: The Helm charts are designed to work in an Air-gapped environment. So, the images must first be available in a network location accessible within the Air-gapped environment before deploying the Helm charts.
- Verify that you have container images VMware-Bare-Metal-Automation-Remote-Worker-3.1.0-v2023.2.459-b6.tar.gz for VMware BMA Remote Worker.
- Verify that your environment have minimum requirements of the VMware BMA.
- Verify that you have a machine (with minimum 30 GB disk space) with Docker installed to push VMware BMA container images to your container registry.
- Verify that you have mapped domain name in a DNS service for your VMware BMA FQDN.
- Ensure you have a default storage class available on the Kubernetes cluster.
Procedure
- Configure container server or registry.
You need a container registry to store the container images of VMware BMA.
VMware has verified the deployment with Harbor. For more information on Harbor installation, see Configuring an Airgap Repository topic in VMware Telco Cloud Automation Deployment Guide in VMware Telco Cloud Automation Documentation.
- Create a public project in Harbor server for VMware BMA Remote Worker.
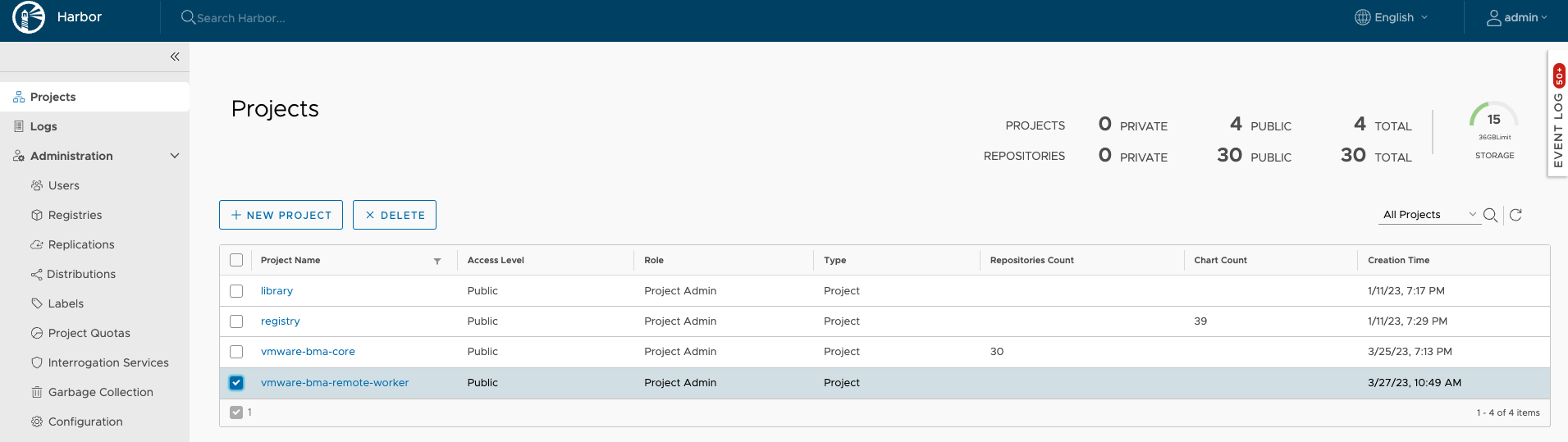
- Setup a Kubernetes cluster.
Note: VMware has validated against VMware Kubernetes cluster. For more information, see Minimum Requirements.
- Download the Container images and the Helm charts from the VMware Downloads section.
- Copy the Container images and Helm charts to the Kubernetes cluster.
- Run the following command to extract the VMware BMA Remote Worker tar bundle VMware-Bare-Metal-Automation-Remote-Worker-3.1.0-v2023.2.459-b6.tar.gz in your machine from where you want to push the container images.
gunzip VMware-Bare-Metal-Automation-Remote-Worker-3.1.0-v2023.2.459-b6.tar.gz
- Push the container images to your container registry in the public project.
You can push container images to Harbor server or registry in different ways. The below example explains pushing container images using Docker.
- Run the following command to start and enable the docker service as sudo if Docker is not installed.
sudo yum install docker sudo systemctl start docker sudo systemctl enable docker
- Run the following command to login to Harbor via Docker.
docker login harbor_sever_ip -u username -p password
Example:docker login 192.168.10.25 -u admin -p Harbor12345
In the above example, 192.168.10.25 is the harbor_server_ip, Harbor12345 is the password and admin is the username.
If Docker login fails, see Docker Login Failure Troubleshooting section.
- Run the following command to load Docker.
docker load -i vmware-images-bma-remote-worker-v2023.2.459-b6.tar
Currently, the repository for VMware BMA Helm charts is 423562884727.dkr.ecr.us-east-1.amazonaws.com.
- Run the following command to start and enable the docker service as sudo if Docker is not installed.
- Run the following command to tag the container images through docker.
docker tag <loaded_image_location> <registry_image_location>
192.168.10.25 is the IP address of the Harbor server and vmware-bma-remote-worker is the public project created in the Harbor server.
docker tag 423562884727.dkr.ecr.us-east-1.amazonaws.com/pliant-worker-nodejs-master:v1.107.0 192.168.10.25/vmware-bma-remote-worker/pliant-worker-nodejs-master:v1.107.0 docker tag 423562884727.dkr.ecr.us-east-1.amazonaws.com/addon-ansible-master:v1.15.2 192.168.10.25/vmware-bma-remote-worker/addon-ansible-master:v1.15.2 docker tag 423562884727.dkr.ecr.us-east-1.amazonaws.com/addon-napalm-master:v3.5.0 192.168.10.25/vmware-bma-remote-worker/addon-napalm-master:v3.5.0 docker tag 423562884727.dkr.ecr.us-east-1.amazonaws.com/addon-textfsm-master:v1.7.1 192.168.10.25/vmware-bma-remote-worker/addon-textfsm-master:v1.7.1
- Run the following command to perform docker push to Harbor registry.
docker push <registry_image_location>
In the below example, 192.168.10.25 is the IP address of the Harbor server and vvmware-bma-remote-worker is the public project created in the Harbor server.docker push 192.168.10.25/vmware-bma-remote-worker/pliant-worker-nodejs-master:v1.107.0 docker push 192.168.10.25/vmware-bma-remote-worker/addon-ansible-master:v1.15.2 docker push 192.168.10.25/vmware-bma-remote-worker/addon-napalm-master:v3.5.0 docker push 192.168.10.25/vmware-bma-remote-worker/addon-textfsm-master:v1.7.1
If Docker push fails, see Docker Push Failure in Troubleshooting.
In Total, container registry public project, here Harbor project, must contain four container images for VMware BMA Remote Worker.
- Establish certificates trust between Harbor server and Kubernetes cluster.
Add Harbor as partner systems in VMware TCA and associate it with the Kubernetes cluster on top of which VMware BMA runs. This step is required to avoid any certificates related issues while the pods come up.
For more information, see Add a Partner System to VMware Telco Cloud Automation topic in VMware Telco Cloud Automation User Guide in VMware Telco Cloud Automation Documentation.
- Create a Remote worker group in the VMware BMA UI.
Before installing VMware BMA Remote Workers, you must have an existing worker group's credentials or you can create a new worker group from the VMware BMA Core Web UI.Note: If you create a new worker group, ensure that you add permission to various roles to access this worker group.
- Access VMware BMA Web UI.
- Click Global Settings
 > Worker Groups.
> Worker Groups. - Click Create Worker Group.
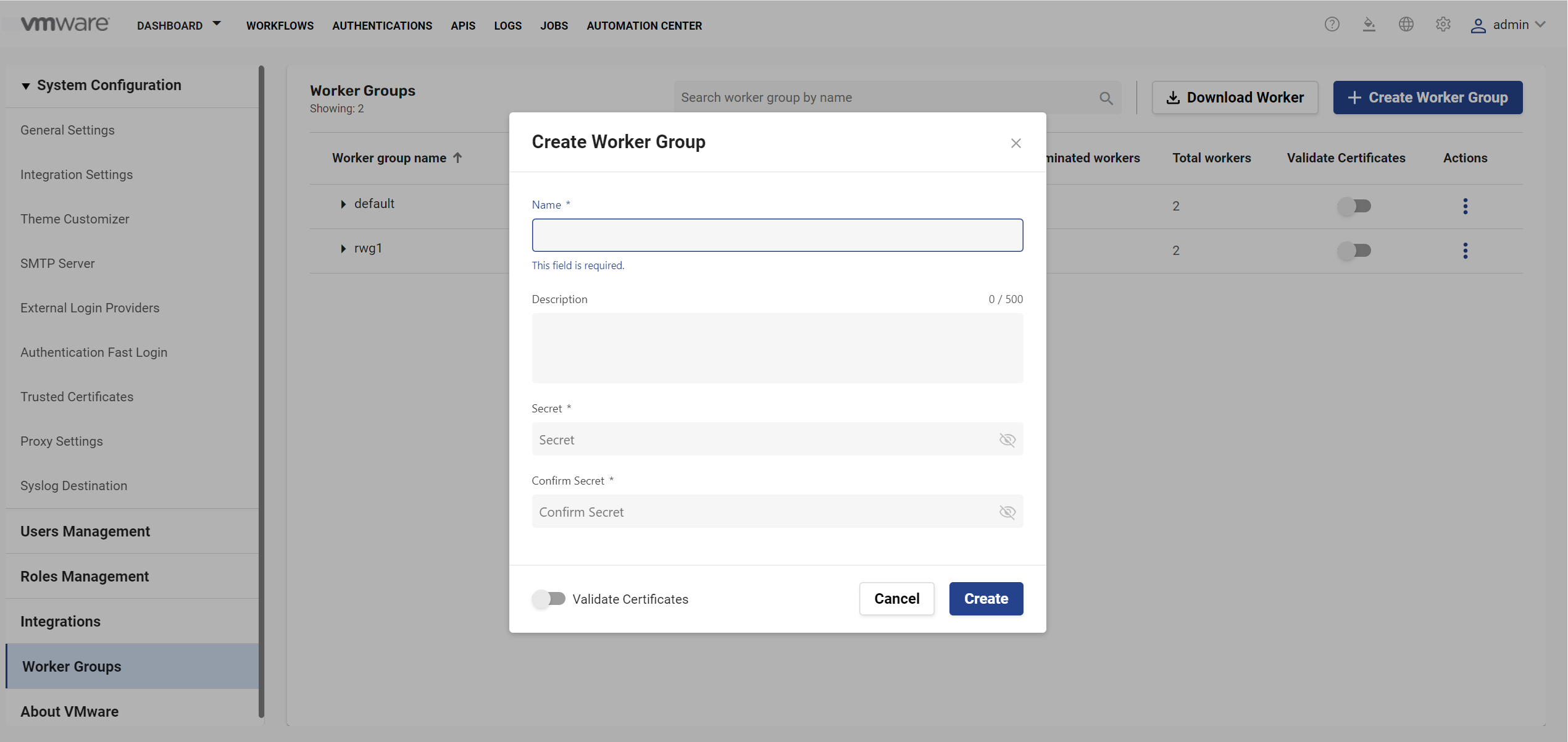
In the above example, Validate Certificates is disabled. This is correct if you are not using an external certificate to install VMware BMA Remote worker. If you are using a certificate during the VMware BMA Remote worker installation, then you must enable Validate Certificates.
- Click Create.
- Place the file VMware-Bare-Metal-Automation-Remote-Worker-Chart-3.1.0-v2023.2.459-b6.tgz on your Kubernetes cluster.
- Validate certificate.
Certificate validation is the process of establishing the trust between VMware BMA Remote Workers and:
- VMware BMA Core
- Any third party TLS communication (Example: iDRAC servers)
You can establish the certificate validation using a custom Enterprise Certificate Authority (CA) certificate. For any external remote worker groups, you must set the verify_certificate flag to true. To ignore the certificate validation, you can set the verify_certificate flag to false. You can disable certificate validation from the VMware BMA Web UI, if it is not required. For more information, see step 14.
All the servers shipped by Hardware vendors such as Dell, HPE can have certificates signed by one Enterprise CA and customer can add this CA certificate as Trusted CA in VMware BMA Web UI to get the authentication working. For more information, see Create Trusted Certificate topic in VMware Bare Metal Automation for VMware Telco Cloud Platform User Guide in VMware BMA Documentation. If this is not done, workflow authentication fails while trying any TLS communication if the verify_certificate flag is set to true.
- Create the overrides values YAML file, bma-remote-worker-values.yaml, with the following content.
VMware BMA Helm charts installation with Signed certificates
The VMware BMA Remote Worker chart needs a Enterprise CA certificate to evaluate TLS certificate of VMware BMA Core. You can specify .Values.bma.certificates.api_ca_cert either as its plain PEM representation or as the Base64 encoded PEM.
When using the TLS CA certificate, the address of the VMware BMA Core, .Values.bma.host.address must be specified as a domain name, and not as an IP address. If the VMware BMA Core host machine does not have its own domain name such as virtual machine, then you must set the host alias using .Values.bma.host.alias.{ip, hostname}. Both .Values.bma.host.alias.hostname and .Values.bma.host.address must match the VMware BMA Core’s TLS certificate’s Common Name (CN).
You must assign .Values.bma.host.alias.{ip,hostname} if a hostname is assigned to the address field in VMware BMA Core Helm chart overrides values YAML file.
The following example uses, certificate provided by VMware, that has CN=telco-baremetal-automation.local.
# required - sets the registry for this chart's images. Does not have default value. # example, imageRegistry: 192.168.10.25/vmware-bma-remote-worker imageRegistry: <FQDN/IP>/<VMware BMA Remote Worker project name in harbor> # if set, used as value of imagePullSecrets directive for all images pulled from imageRegistry # imagePullSecretName: bma: host: alias: # both ip and hostname must be provided for the alias to take effect ip: "192.168.10.1" # optional; if provided binds the hostname of the pliant api to this ip in the /etc/hosts file hostname: "telco-baremetal-automation.local" # optional; the host name of the pliant api. Should be the same host as in the .Values.bma.host.address, without the 'https://' protocol prefix address: "https://telco-baremetal-automation.local" # required; the address (with https:// protocol prefix) of the VMware BMA core host, ex. "https://my.host.com" worker_group_name: "bma-rw-group" # required; the worker group this worker will attach to worker_group_secret_key: "vmware" # required; the password of the worker group this worker will attach to verify_certificate: true # Set verify_certificate: true since an external certificate is set certificates: # sets certificate for communication with pliant-api in plain PEM format or Base64 encoded PEM; if not set, .Values.bma.host.verify_certificate is assumed to be false and certificate validation is disabled api_ca_cert: | -----BEGIN CERTIFICATE----- MIID6jCCAtKgAwIBAgIEPJ/xUjANBgkqhkiG9w0BAQsFADCBjTELMAkGA1UEBhMC VVMxKTAnBgNVBAMMIHRlbGNvLWJhcmVtZXRhbC1hdXRvbWF0aW9uLmxvY2FsMRMw EQYDVQQIDApDYWxpZm9ybmlhMRIwEAYDVQQHDAlQYWxvIEFsdG8xFDASBgNVBAoM C1ZNd2FyZSwgSW5jMRQwEgYDVQQLDAtUZWxjbyBDbG91ZDAeFw0yMjExMDkwNjIz MDFaFw0yNzExMDgwNjIzMDFaMIGNMQswCQYDVQQGEwJVUzEpMCcGA1UEAwwgdGVs Y28tYmFyZW1ldGFsLWF1dG9tYXRpb24ubG9jYWwxEzARBgNVBAgMCkNhbGlmb3Ju aWExEjAQBgNVBAcMCVBhbG8gQWx0bzEUMBIGA1UECgwLVk13YXJlLCBJbmMxFDAS BgNVBAsMC1RlbGNvIENsb3VkMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC AQEApCG9nv+a1/IWTzeIiCG74sww1bFeF3z6phYnryve0Y17SOSAZ9LbE4sdi4Db l5rzGmaIiiZcJer7pIqseaApscRicujzn5iMM8l9k0XQQAez7DIqs9UR64kQghxb X0KVSvLoJup4B/8WLBbom2Udqctzo6VPvlbZy1md8w9byBe89SfspgMkJBumvZ4A 55Wos42EUJC6g7QmroFDgqZCdimT2E7XPCbDhu3wPywUbeuqRoasgNsirpuyL/LX w4nC/sdsPzSOyfJrWcmZHPiEnH54DdUGGIkt2Unxyi3hRbmYmsNHLQW8sQM+LbwN +5Gik2t5q3TUzRpKz2dJDUdlHQIDAQABo1AwTjAdBgNVHQ4EFgQUZ26/Lr/TSa25 +2XrjygBL45Hv6UwHwYDVR0jBBgwFoAUZ26/Lr/TSa25+2XrjygBL45Hv6UwDAYD VR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAWBA30D6GNSHXRO8RExGzf8DC KkpBGEBmYGC0oiq1hsr3q+360E7Sf8YvgC/7t0OKISrrkUg1CRn5qruQJ+dh3sWA 5Rfer9wInARrzxhgusIFxaUBl/A35WmpCtDkAs3vWKo3qWMdny1EZDwpbsyiUYrT KQtezAzM940s80lmju2FXAPx/MZZTIu9X0bbBrxpzHtV9egjfkn2beOn6LQnATua jq7hqjm3jzVIwIH1ciDOESww78F8OfZyXuVqVqqgYmRgTY8iVgV0KxNUFB/K4lBy fMbN9w5lXsHOwB0dVrrgJuyZfuX3VXr6taTnADWPfAFPjjyhojHQsn/x+n06WA== -----END CERTIFICATE-----VMware BMA Helm charts installation with Self-Signed or auto-generated certificates# required - sets the registry for this chart's images. Does not have default value. # example, imageRegistry: 192.168.10.25/vmware-bma-remote-worker imageRegistry: <FQDN/IP>/<VMware BMA Remote Worker project name in harbor> # if set, used as value of imagePullSecrets directive for all images pulled from imageRegistry # imagePullSecretName: bma: host: alias: # both ip and hostname must be provided for the alias to take effect ip: "192.168.10.1" # optional; if provided binds the hostname of the pliant api to this ip in the /etc/hosts file hostname: "telco-baremetal-automation.local" # optional; the host name of the pliant api. Should be the same host as in the .Values.bma.host.address, without the 'https://' protocol prefix address: "https://telco-baremetal-automation.local" # required; the address (with https:// protocol prefix) of the VMware BMA core host, ex. "https://my.host.com" worker_group_name: "bma-rw-group" # required; the worker group this worker will attach to worker_group_secret_key: "vmware" # required; the password of the worker group this worker will attach to certificates: # sets certificate for communication with pliant-api in plain PEM format or Base64 encoded PEM; if not set, .Values.bma.host.verify_certificate is assumed to be false and certificate validation is disabled api_ca_cert: "" # ex. "-----BEGIN CERTIFIATE-----\n..."- Enter image registry information in imageRegistry.
- Add values for address, worker_group_name, and worker_group_secret_key attributes.
- Run the following command to install VMware BMA Remote Worker.
helm install <name of the service> -n <namespace> --create-namespace -f <overrides Helm chart values file> ./<name of the Helm charts zipped tar bundle>
In the following example:- vmware-bma-remote-worker is the name of the service
- bma-remote-worker is the name of the namespace
- bma-remote-worker-values.yaml is the overrides Helm chart values file.
- VMware-Bare-Metal-Automation-Remote-Worker-Chart-3.1.0-v2023.2.459-b6.tgz is the name of the Helm charts zipped tar bundle.
helm install vmware-bma-remote-worker -n bma-remote-worker --create-namespace -f bma-remote-worker-values.yaml ./VMware-Bare-Metal-Automation-Remote-Worker-Chart-3.1.0-v2023.2.459-b6.tgz NAME: vmware-bma-remote-worker LAST DEPLOYED: Fri Apr 10 14:01:30 2023 NAMESPACE: bma-remote-worker STATUS: deployed REVISION: 1 TEST SUITE: None
- Run the following command to verify if all the pods are running.
kubectl get pods -n <namespace>
kubectl get services -n bma-remote-worker