Enabling the Carbon Black App Control Connector adds an External Notifications page to the console.
This page is a table of notifications from network security devices and services. Each row in the table includes key information such as file hashes and source IP addresses. If the file or computer referenced in a notification is also in Carbon Black App Control endpoint data, that data can be correlated with the notification.
In addition to notifications, this page shows an error message if there is a problem receiving notifications from any of the configured connected devices or services.
Notifications from Palo Alto Networks are pre-filtered to eliminate those not likely to be of interest for security analysis purposes. If a Threat Log notification has a Severity equal to “informational”, “low”, or “medium”, by default it is not included in the notifications that are delivered to the Carbon Black App Control Server. WildFire Log notifications with a Category of “benign” are filtered out by default.
A daily check is done on the total number of notifications from all sources. If the daily check finds that this number is excessive, the oldest notifications in the logs are trimmed. The number of notifications can exceed the limit by a considerable amount before trimming is scheduled, such as when notifications are first enabled.
In addition to trimming notifications after they reach a numeric limit, the server deletes notifications past a maximum age. Initially, the numeric limit is 200,000 notifications and the age limit is six months. These may be modified in the future.
To open the External Notifications table in the console, click Reports > External Notifications on the console menu.
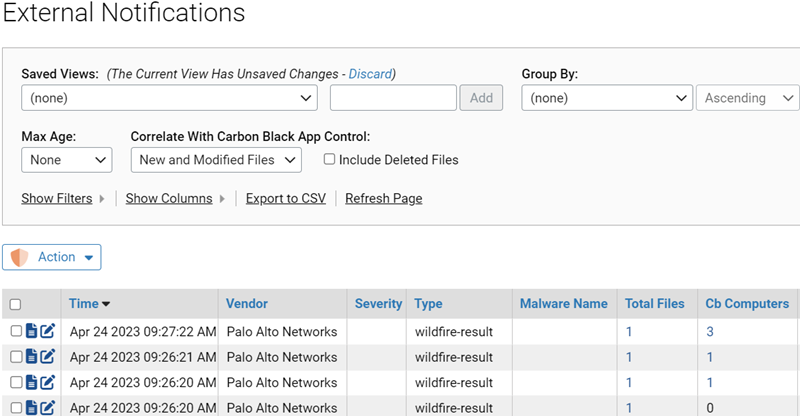
Because of the data correlation with the Carbon Black App Control Server, external notifications can be prioritized immediately by their impact on systems running agents. When a malware notification is received from a connected network security source, you can determine the following:
- Whether the malware is present on any of your systems.
- Whether the malware has ever executed on any of the systems.
- How much the malware has spread (that is, on how many computers).
- Details on the system identified as the source for this malware, including what kind of user activity there was on the system and other system activity.
- The External Notifications table includes several ways to drill down for additional information:
- The View Details button opens the External Notification Details page for the notification in its row. The details page includes all of the information stored in your Carbon Black App Control database for this notification. See External Notification Details for more information. It also includes a link to open the full XML details file for the notification. See Showing XML Details for more information on this page.
- If there is a number greater than zero in the Total Files or New and Modified Files column, clicking on the number opens the External Notification Details page.
- If the Malware MD5, SHA-1 or SHA-256 hash is listed in the table and identifies a file inventoried by your Carbon Black App Control Server, clicking on the hash opens the File Details page for that file.
- In any of the Cb Files columns, if the number of files shown is 1, clicking on the number opens the File Details page for that file. If the number shown is 2 or greater, clicking on the number opens the External Notification Details page with the Known Files tab showing.
- In the Cb Computers column, if the number of computers shown is 1, clicking on the number opens the Computer Details page for that computer. If the number shown is 2 or greater, clicking on the number opens the Computers table.
- If the Source or Destination Address column shows an address for a system that has the agent installed, clicking on the address opens the Computer Details page for that computer.
- The History button opens the Notification Details page with the History tab showing. The History tab includes the 20 most recent actions related to this notification.
The following table shows the information available in the External Notifications table. Not all of these columns appear in the table by default.
| Column |
Description |
|---|---|
| Vendor |
Vendor whose product sent the external notification. Currently Palo Alto Networks (other vendors might appear if you have upgraded from previous App Control versions). |
| Appliance |
Name of the external appliance or service that provided the notification; has link to appliance or service console URL. |
| Product |
External appliance or service product name, if provided; has link to appliance console URL. |
| Version |
External appliance, agent, or report version; has link to appliance console URL. |
| Time |
Date and time when the malware was detected on the network. |
| Severity |
Severity of notification. Scale varies by vendor. |
| Type |
Type of notification (not the name). For Palo Alto Networks, this can be: wildfire, spyware, virus, vulnerability, wildfire-result. Other notification types might appear if you implemented a connector for a different device or service in previous Carbon Black App Control versions. |
| Source IP |
The IP address from which the malware originated. |
| Source Address |
Source Address is the address from which the malware originated, from one of the following sources:
|
| Source URL |
URL of the computer on which the malware was originated, as resolved by the provider. |
| Source Username |
Name of user logged into the system at the Source Address. Appears for Microsoft and Palo Alto Networks integrations if Active Directory is integrated with the appliance or service. |
| Destination IP |
IP address to which the malware was targeted. |
| Destination Address |
Address to which the malware was targeted, resolved as described for Source Address. |
| Destination Username |
Name of user logged into the system at the Destination Address. Appears for Palo Alto Networks integrations if Active Directory is integrated with the appliance or service. |
| Malicious |
Shows whether the notification identifies malicious files (Yes/No). |
| Malware Name |
Malware name reported in notification (can be multiple, comma separated). |
| Malware MD5 |
Top-level MD5 hash reported in notification. |
| Malware SHA1 |
Top-level SHA1 hash reported in notification. |
| Malware File |
Top-level filename reported in notification. |
| Application |
Application reported in the notification. |
| Analysis Environment |
Operating System environment used for file analysis. For Palo Alto Networks, may also include information about key applications in the environment, such as Office. |
| Registry Keys |
Number of registry key modifications reported in the notification. |
| Directories |
Number of directory modifications reported in the notification. |
| New and Modified Files |
Number of files created or modified by this malware as reported in this notification. |
| Total Files |
Total number of unique files in this notification. |
| Received Time |
Date and time this notification was received by the App Control Server. |
| Modified Time |
Date and time when this notification was last modified (that is, its status changed). |
| Cb Status |
Status of the notification in Carbon Black App Control (Notified, Escalated, Resolved, Closed). |
| Cb Known Files |
Number of unique files in this notification known to the App Control Server. May change based on the Correlate with Carbon Black App Control option on the External Notifications page. |
| Cb Executed Files |
Number of files in this notification known to the Carbon Black App Control Server and executed on an endpoint. May change based on the Correlate with Carbon Black App Control option on the External Notifications page. |
| Cb Banned Files |
Number of files in this notification known to the Carbon Black App Control Server and banned. May change based on the Correlate with Carbon Black App Control option on the External Notifications page. |
| Cb Computers |
Number of Bit9-managed computers that have at least one file matching one of the reported MD5 hashes in this notification. |
| Cb Files On Computers |
Total number of instances on agent-managed computers of files reported in this notification. |
| Cb Submitted |
Indicates whether a file from this notification was submitted to an external device by this Carbon Black App Control Server for file analysis (Yes/No). |