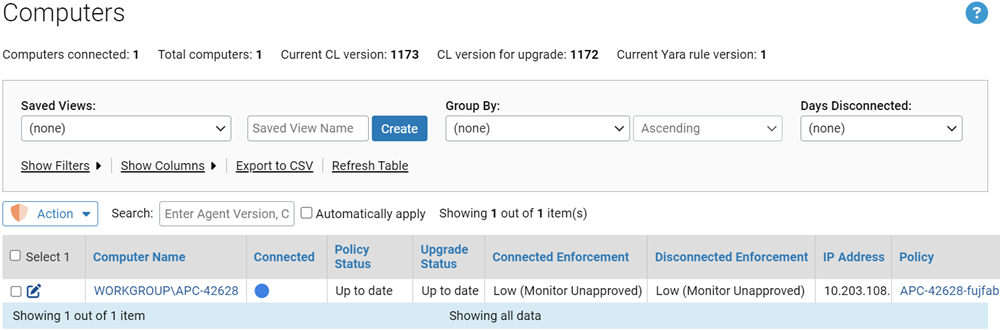
The Computers page provides a table of computers and information about them, including their platform, policies, Enforcement Levels, and whether they are currently connected to the server. As with most console tables, you can add or remove details shown in the table using the Columns button.
You also can use the Filters panel or Search field to limit the computers shown to those you are most interested in. For more about customizing your view, see Console Tables.
In addition to the table of agent-managed computers, the Computers page shows the following information:
- Computers connected – Shows the number of computers running the agent that are currently connected to the server.
- Total computers – Shows the total number of computers that are currently members of security policies managed by the server.
- Current CL version – Shows the version number of the latest Configuration List (CL) available from the server. This can be used to help determine whether the CL for a particular agent is out of date. Note, however, that some CL versions are agent-specific, so the fact that the CL version for an agent doesn’t exactly match the CL version shown here does not automatically mean the agent is out of date.
- CL version for upgrade – Shows the minimum CL version that an agent must have before it can be upgraded. Earlier versions might be missing rules, such as approvals needed for upgrade packages, required for upgrade.
View the Table of Computers
Use this procedure to view the table of computers managed by your Carbon Black App Control Server.
Procedure
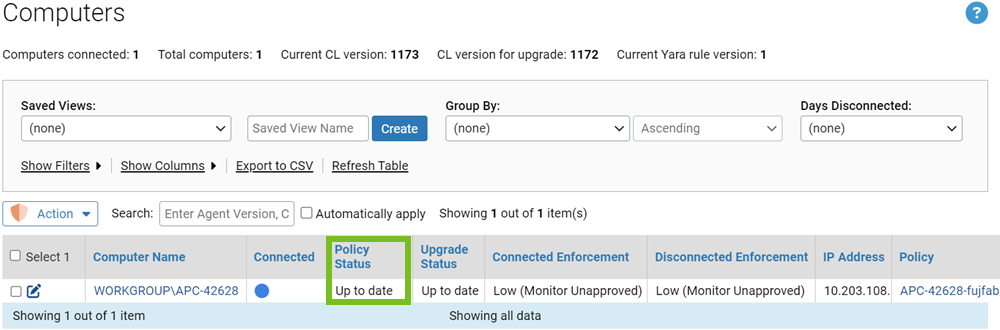
Agent Policy Status
The Computers table includes a column called Policy Status, which indicates whether the agent for each listed computer is up to date with the App Control Server rules that apply to it.
Notice that this field does not appear on the Computer Details page.
| Policy Status |
Description |
|---|---|
| Up to date |
Agent Enforcement Level, policy, and rules are all up to date. |
| Policy out of date |
Agent is not up to date on changes to its policy. |
| Approvals out of date |
Agent rules (including file approvals or bans, trusted users, publisher rules, updater rules, device rules, memory rules and registry rules) are out of date. |
| Enforcement Level out of date |
Agent Enforcement Level is out of date. |
| Out of date |
Agent is out of date on more than one of these: Enforcement Level, policy, or other rules. |
| Unprotected |
Agent is unprotected because of an upgrade failure. |
| Yara rules out of date |
Agent does not have up-to-date Yara rules. Yara rules help identify malicious files. |
Actions on Selected Computers
The Action menu on the Computers page has commands that can be applied to one or more computers.
You select a computer for action by checking the box to the left of its row.
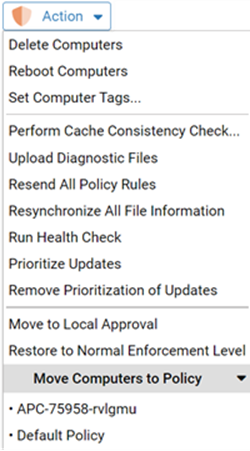
The actions include deleting, upgrading (if enabled), tagging, and rebooting computers, and moving the computers to different policies. Additional commands available on this menu are described in the Actions and Advanced sections of Computer Details.