The File Details page shows details of the global state of a file. In any table showing unique files, such as the File Catalog, you click the View Details button to open the File Details page.
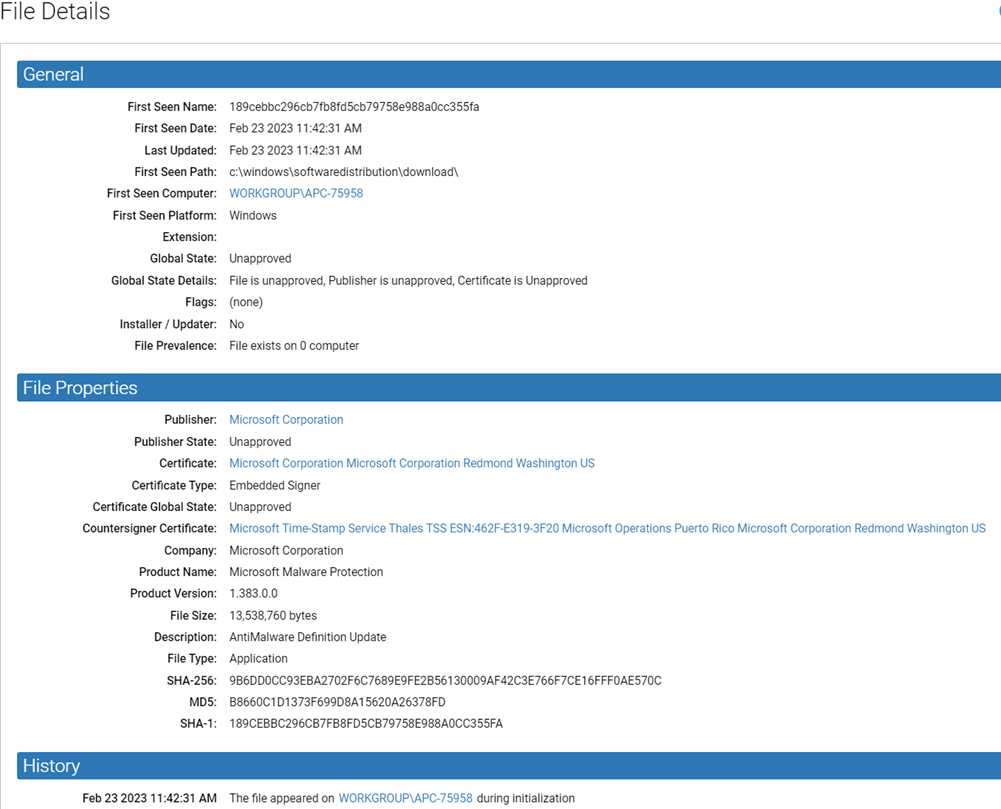
The following table shows the information and actions available on the File Details page. Certain global file attributes are captured only for the first seen instances of the file seen by a Carbon Black App Control Agent. These are labeled as such on the File Details page.
| Field |
Description |
|---|---|
| General panel |
|
First Seen Name |
File name of the first file to have this hash discovered by an agent managed by this Carbon Black App Control Server. |
|
|
Time the first file with this hash was seen on a network computer, displayed in the format: MM DD YYYY hh:mm:ss(AM/PM). |
|
|
Last date and time when the file metadata was updated. (Not affected by Carbon Black App Control-provided data, for example, prevalence or trust). |
|
|
Path of the first file to have this hash reported to this server. |
|
|
Name of the computer on which the file was first seen. Click this name to open the Computer Details page for this computer. If you later delete the first-seen computer from the system, it is no longer associated with the file and this field is blank. |
|
|
Platform (Windows, macOS, Linux) on which this file was first seen by this server. |
|
|
File extension of the first seen file to have this hash. |
|
|
Global State is a combination of File State and Publisher State, and indicates the overall approval state for all systems or by policy. Files can be globally approved by hash or publisher. The possible values are Approved, Banned, Unapproved, Approved by Policy, Banned by Policy, and Mixed. Global State is Mixed when a file is approved in some policies but banned in other policies. For example, a file can be banned by hash in some policies, and approved by publisher in the remaining policies. |
|
|
The File State and Publisher State contributing to Global State. |
|
|
File-state metadata for use by VMware Carbon Black Support engineers. |
|
(in File Details)
(in File Catalog) |
Indicates whether either Carbon Black App Control analysis or a user selection has identified this file as an installer or updater (which means that if the file is approved, so are all files that it creates). Yes – Treat the file as an installer that will expand to create more files. If this file is approved, files that it writes are locally approved. No – Treat the file as non-expandable. |
|
|
Indicates whether reputation-based approval is enabled for this file (Yes or No). This field only displays if Carbon Black File Reputation is properly configured. |
|
(in File Details)
(in File Catalog) |
The number of computers on which this file exists. You can use the Add Alert command on the Actions menu to add an alert that triggers when the prevalence of a file reaches a set level. See Using App Control Alerts for details. |
|
|
Click to get a detailed analysis (if available) of this file from Carbon Black File Reputation. This button appears on the File Details page after you activate Carbon Black File Reputation. See Activating Carbon Black File Reputation. |
| File Properties panel |
|
Publisher |
If the file is digitally signed or is included in a digitally signed package, the console displays the publisher (software manufacturer) of the associated application. |
|
|
The approval state of the publisher. Values are Approved, Approved by Policy, Banned, Banned by Policy, and Unapproved. This field does not display if the publisher is unknown. |
|
|
The Subject Name for the certificate that signed this file. |
|
|
For leaf certificates, certificate type indicates what the leaf certificate is being used for and how it is associated with a file. Type is a combination of the following terms: Embedded, Detached, Signer, Cosigner. |
|
|
The effective state of the certificate. Values are Unapproved, Approved, Banned, Approved By Policy, Banned By Policy, Mixed. |
|
|
The Company name (if provided) in the file metadata. |
|
|
The Product Name (if provided) in the file metadata. |
|
|
The Product Version (if provided) in the file metadata. |
|
|
Size of the file (in bytes). |
|
|
The Description (if provided) in the file metadata. |
|
|
One of the following: Application – Any executable (for example, .exe or .com) except for Packages Supporting File – Any library loaded by an executable (for example, .dll, .ocx, .sys) Package – Any installer (.exe with contents, such as a self-extracting zip or setup program) Script File – Any script or batch file (for example, .bat, .vbs, .wsf) Other – Reserved for future types Unrecognized Executed File – A file that was not identified as an executable by Carbon Black App Control during initialization or later analysis, but that some process attempted to execute. The execution attempt adds the file to the lists of files tracked and managed by the Carbon Black App Control Server and Agents. Unknown – Files reported by older Carbon Black App Control Agents that do not provide file type information |
|
|
Hash (data signature) of the file created using Carbon Black App Control’s proprietary SHA-256 algorithm. SHA-256 is used internally as the preferred hash for files tracked by Carbon Black App Control. SHA-256 hashes created by the Carbon Black App Control algorithm may be identical to those created by other means. However, some files change their hash every time they are installed because they include date, location, or other context-specific information not relevant for tracking purposes. For files known to do this, Carbon Black App Control uses a special fuzzy hashing algorithm that eliminates this extraneous variation and shows every instance of such files on computers running Carbon Black App Control Agents to be identical. When this algorithm has been used, the hash is identified as "SHA-256 (Normalized)". You can search for files by hash using filters on the Files page or the Find Files page. All File Instances in the Related Views menu provides a way to do this directly from the File Details page. |
|
|
MD5 is a widely used hashing algorithm. Carbon Black App Control provides this alternate hash to identify the file against a list of published MD5 hashes. |
|
|
SHA-1 is a widely used hashing algorithm. Carbon Black App Control provides this alternate hash to identify the file against a list of published SHA-1 hashes. |
| Carbon Black File Reputation Information panel |
|
Trust |
Indicates the level of trust for the file based on Carbon Black File Reputation information such as file source and certificates. The trust rating is showing on a scale of 0 (none) to 10 (most trusted) together with a graphic meter reflecting this rating. Trust for a file also might be unknown, in which case this field is blank in the column for that file and shows (unknown) in its details page. The value of this field is a subjective assessment of the file’s integrity. As an indication of whether the file appears to be safe based on information derived from Carbon Black File Reputation analysis, the trust value does not signify actual approval on the Carbon Black App Control Server. However, you can use Reputation Rules to automatically approve files based on their trust rating or the trust rating of their publisher. |
|
(in File Details)
(in File Catalog) |
If Carbon Black File Reputation is configured, discovered files are automatically submitted for threat analysis. Carbon Black File Reputation flags known malware with a red X icon. No flag indicates that the file was not recognized as malware, not necessarily that it is safe. Threat levels include: 0 - Clean 1 - Potentially malicious 2 - Malicious Unknown - Not identified |
|
|
If you have configured Carbon Black File Reputation, this field shows the category that this file is in (for example, Entertainment, Hacking Tools, Instant Messaging, Media Players). If the category is unknown, this field is not displayed on the details page. |
|
|
Indicates ways in which the file is treated differently in particular policies. For example, if the file is under a policy-specific hash ban or approval, the policy name is shown here. This field does not display if there is no policy specific treatment of the file. |
| Carbon Black EDR panel (all data is from Carbon Black EDR Server) |
|
First Seen Activity |
Date and time when activity involving this file was first reported to the Carbon Black EDR server. |
|
|
Number of Carbon Black EDR Watchlists that this file is on. |
|
|
Number of hosts that have observed the binary with this MD5 hash value. |
|
|
Number of unique paths in which this file has been seen. |
|
|
Number of network connections that the execution of this process attempted or established. |
|
|
Number of registry modifications made because of execution of this file. |
|
|
Desktop icon associated with this file (if any). |
|
|
Links back to the Carbon Black EDR console to get additional information about the file. |
| External Analysis Results panel | |
| <productname> | If you integrated Carbon Black App Control with a supported network security device or service and have correlated notifications from that source with the Carbon Black App Control File Catalog, files that match malicious or potential risk notifications from the third party source show those results in this panel. Possible options are:
|
| Group Information panel | |
| <group name> |
If a file is the root of a group, this indicates the group name (usually the file name) and how many files are in the group. Note that tools such as browsers can display as the root of a group because they download files. These files may appear as group members even though they are unrelated to the tool in any other way. |
| Groups that contain this file panel | |
| <group names> |
If a file is associated with a group, this panel indicates the group(s) with which this file is associated and the root file(s), if known, of the group(s). Some files may be installable by multiple root files (or be copies of another file), and so they will show multiple groups here. Each group shown includes a Find all files contained in this group link that opens the File Group Details page to show the results. |
| History panel | |
| <dates and times> |
Indicates whether the file was identified on the first-seen computer during initialization or detected after initialization. Also indicates any approvals or bans applied to the file. Files detected after initialization are tracked as unapproved files until approved or banned, and may be viewed in the New Unapproved view on the Files page File Catalog tab. |
| Fields in table only | |
|
|
Indicates whether a console user acknowledged this file (Yes or No). You can acknowledge a file using the Action menu on the File Catalog tab. This can help distinguish files you already know about from new arrivals. Acknowledging a file removes it from the New Unapproved Files view but does not change its state. |
|
|
Indicates whether the file was approved by either its own or its publisher’s reputation. (Yes or No). |
|
|
Shows an overall assessment of the risk of this file, combining file threat, file trust, and publisher trust from all available sources. |
|
|
Unique, App Control-generated hash identifier for this file. |
|
|
For Approved or Banned certificates, how its state is specified. The possible values are: Manual, Trusted Directory, Imported, External (API), Unknown. |
|
|
Distinguished name of the subject of the certificate, in this case the signer of the file. |
|
|
For individual files, the configuration list number in which the current global state for this file was defined. Agents at or beyond this CL Version have the correct global state for the file. |
|
|
Indicates whether this file was ever blocked by an Carbon Black App Control rule. |
|
|
Indicates whether this file is excluded from the Files on Computers inventory. See Excluding Tracking of Microsoft Support Files. |
|
|
Size in bytes of each file. |
|
|
The approval/ban state of the file hash (Unapproved, Approved, Banned, Approved by Policy or Banned by Policy). The effective Global State of a file combines File State and Publisher State. You can change File State using the Action menu on any of the tables on the Files page or any of the details pages for files. On details pages, you can edit an existing approval or ban. |
|
|
For Approved or Banned file hashes, how its state is specified. The possible values are: Manual, Trusted Directory, Reputation, Imported, External (API), Unknown. |
|
|
Unique numeric ID for this file. |
|
|
Indicates whether this file was present during agent initialization (Yes or No). |
|
|
Full package or application name of the installed program (if any) with which this file is associated. Only Windows files are identified as Installed Programs. |
|
|
Indicates whether a file not identified by Carbon Black App Control as an installer has been marked as in installer by a console user. Yes – File was marked as an installer by a user. No – File was not marked as an installer by a user (although it might have been identified by Carbon Black App Control as an installer). |
|
|
Publisher (if available) or company (if available and there is no publisher information) for the file. |
|
|
Indicates whether this file is part of a trusted package. (Yes or No). A trusted package is a common source or installer located in a Trusted Directory. Only Windows files can be in a trusted package. |
|
|
If a unified rule has been applied to this file, the name of the unified management server that created or copied the rule. |