When an alert is triggered, notification mail is sent to each subscriber to that particular alert and, if configured, to the global alert subscriber.
The console shows one banner per triggered alert class. The Carbon Black App Control Server sends alert email for every instance. Instances are defined as distinct cases that match the alert conditions. In the case of malicious files, for example, if the same malicious file shows up 20 times before you reset the alert, it only counts as one instance. But if 20 different malicious files appear before the alert notification is reset, each one counts as an instance and each one generates a new email message to alert subscribers.
Mail notifications contain basic information about the alert such as the time of the action for this instance alert, the system on which an action took place, the logged in user, and the file hash. The File Propagation Alert mail shown here is typical of file-related alerts. The exact information in the mail varies by alert type.
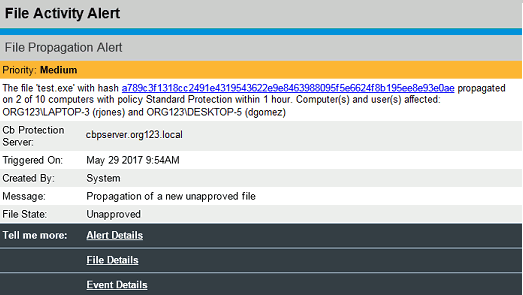
Mail notifications include links to console pages that display relevant information. Links include Alert Details (the list of instances for this alert). In the File Propagation Alert case, the File Details page for the triggering file and Event Details related to the file (hash) that is the subject of the alert are linked. File and Event Details are not included for non-file alerts. There can be a Manage Computers link to the Computers table for events that involve Carbon Black App Control settings such as the policy for the computer.
Each email generated by a new instance of the same alert class is tracked in the same Alert History and has a link to a list of instances of that alert. When you reset an alert, the instance history is cleared, but a record of when it was first triggered during this session remains. See Viewing Alert Instances and History for an example of the history and instance list for one triggered alert.