The Certificate Global State is the effective state of a certificate.
The following are possible values for Certificate Global State:
- Unapproved
- Approved
- Banned
- Approved By Policy
- Banned By Policy
- Mixed
Certificate Global State is determined by the following factors:
- Certificate State – Values are Unapproved, Approved, or Banned.
- Publisher State – Values are Unapproved, Approved, Banned, Approved By Policy, or Banned By Policy.
- Certificate Path State – Values are Unapproved, Approved, Banned, or Mixed (some certificates in the chain are Approved and some are Banned).
- Certificate Key Length and Algorithm – Does this certificate meet System Configuration/Advanced Settings requirements.
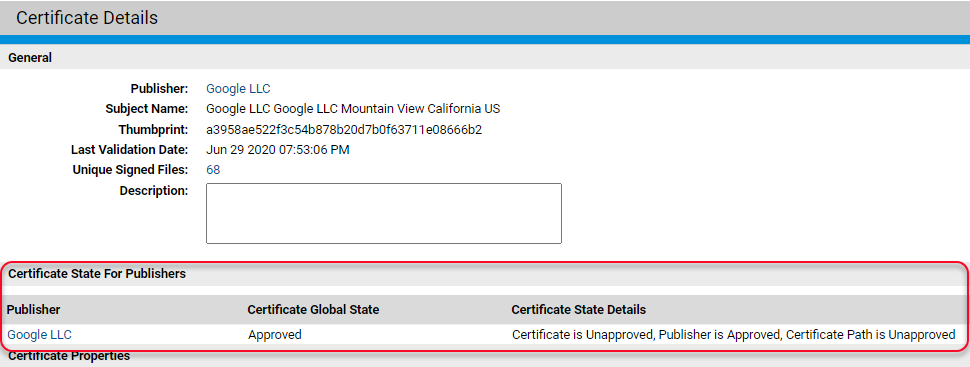
For any certificate, you can view the factors that contribute to Certificate Global State on the Certificates (table) page or the Certificate Details page. The Certificate State for Publishers panel on the details page summarizes the relevant factors.
Even if other elements of certificate state are approved, Certificate Global State might be Unapproved if the certificate does not meet the certificate specifications on the System Configuration/Advanced Options page. When a certificate fails to meet more than one configuration requirement (for example, both the minimum key size and the allowed algorithm specifications), only one of the two reasons appears in Certificate State Details.
The following examples may help clarify the way these values interact with each other to produce Certificate Global State. All possible combinations are shown in the table Determining Certificate Global State.
Example 1: All States and Configuration Allow Approval
| Condition |
Example/Comments |
|---|---|
| If the certificate meets the minimum key size configuration… |
Minimum Certificate Key Size: 1024 Key length of this certificate: 2048 |
| …and its algorithm type is not configured to be ignored… |
Certificate Signature Algorithms to Ignore: Only MD2RSA is checked Signature Algorithm of this certificate: SHA1RSA |
| …and the certificate has a countersignature if required… |
. |
| …and the configured revocation checks have not found the certificate revoked… |
|
| …and the leaf Certificate State is Approved… |
A console user chose to approve the certificate. |
| …and the Publisher State is Approved… |
The publisher was approved by a console user or by reputation. |
| …and no other certificate in this certificate’s path is Banned… |
The state of the Certificate Path is shown in the Certificate Details |
| …then the Certificate Global State is Approved. |
This is the state that will affect files signed by the certificate. |
Example 2: Certificate Does Not Meet a Configuration Requirement
| Condition |
Example/Comments |
|---|---|
| If the certificate meets the minimum key size configuration… |
Minimum Certificate Key Size: 1024 Key length of this certificate: 2048 |
| but its algorithm type is configured to be ignored… |
Certificate Signature Algorithms to Ignore: Has MD2RSA and SHA1RSA checked Signature Algorithm of this certificate: SHA1RSA |
| …and the Certificate State is Approved… |
|
| …and the Publisher State is Approved… |
|
| …and no other certificate in this certificate’s path is Banned… |
|
| …then the Certificate Global State is Unapproved. |
Although all other approval criteria were met, the certificate algorithm is not allowed for approvals. |
Example 3: Banned Certificate in the Path
| Condition |
Example/Comments |
|---|---|
| Whether or not the certificate meets the minimum key size… |
|
| …and no matter whether it meets any of the other Advanced Options requirements… |
|
| …and if the Publisher State is Approved or Unapproved and does not have any policy restrictions… |
|
| …if this certificate or any certificate in the certificate path is Banned… |
|
| ...then the Certificate Global State is Banned. |
Although Certificate Global State is Banned, the ban’s effectiveness on each agent depends upon Block files with banned publishers or certificates on the Advanced Settings of the agent’s policy. This setting is active by default. |
Example 4: Mixed Global State
| Condition |
Example/Comments |
|---|---|
| If the Publisher State is Approved by Policy… |
|
| …and if this certificate or any certificate in it the certificate path is Banned… |
|
| …then the Certificate Global State is Mixed. |
Certificate Global State acts as Unapproved for policies with publisher approval. Certificate Global State acts as Banned for policies not included in the publisher approval if banning by certificates is allowed in the policy. |
The following table shows how different combinations of Certificate, Publisher, and Certificate Path states produce different Certificate Global states. All of these outcomes assume that all certificates in the path meet the configuration requirements specified on the System Configuration Advanced Options page. Where “(by Policy)” appears in parentheses in the table, the Certificate State shown is not specified as being by policy but is effectively “by Policy” because Publisher State is Approve by Policy or Ban by Policy.
| # |
Certificate State |
Publisher State |
Certificate Path State |
Certificate Global State |
|---|---|---|---|---|
| 1 |
Unapproved |
Unapproved |
Unapproved |
Unapproved |
| 2 |
Approved |
Unapproved |
Unapproved |
Approved |
| 3 |
Banned |
Unapproved |
Unapproved |
Banned |
| 4 |
Unapproved |
Approved |
Unapproved |
Approved |
| 5 |
Approved |
Approved |
Unapproved |
Approved |
| 6 |
Banned |
Approved |
Unapproved |
Banned |
| 7 |
Unapproved |
Banned |
Unapproved |
Banned |
| 8 |
Approved |
Banned |
Unapproved |
Banned |
| 9 |
Banned |
Banned |
Unapproved |
Banned |
| 10 |
Unapproved |
Approved By Policy |
Unapproved |
Approved By Policy |
| 11 |
Approved (by Policy) |
Approved By Policy |
Unapproved |
Approved By Policy |
| 12 |
Banned (by Policy) |
Approved By Policy |
Unapproved |
Mixed |
| 13 |
Unapproved |
Banned By Policy |
Unapproved |
Banned By Policy |
| 14 |
Approved (by Policy) |
Banned By Policy |
Unapproved |
Mixed |
| 15 |
Banned (by Policy) |
Banned By Policy |
Unapproved |
Banned By Policy |
| 16 |
Unapproved |
Unapproved |
Approved |
Approved |
| 17 |
Approved |
Unapproved |
Approved |
Approved |
| 18 |
Banned |
Unapproved |
Approved |
Banned |
| 19 |
Unapproved |
Approved |
Approved |
Approved |
| 20 |
Approved |
Approved |
Approved |
Approved |
| 21 |
Banned |
Approved |
Approved |
Banned |
| 22 |
Unapproved |
Banned |
Approved |
Banned |
| 23 |
Approved |
Banned |
Approved |
Banned |
| 24 |
Banned |
Banned |
Approved |
Banned |
| 25 |
Unapproved |
Approved By Policy |
Approved (by Policy) |
Approved By Policy |
| 26 |
Approved |
Approved By Policy |
Approved (by Policy) |
Approved By Policy |
| 27 |
Banned (by Policy) |
Approved By Policy |
Approved (by Policy) |
Mixed |
| 28 |
Unapproved |
Banned By Policy |
Approved (by Policy) |
Mixed |
| 29 |
Approved (by Policy) |
Banned By Policy |
Approved (by Policy) |
Mixed |
| 30 |
Banned (by Policy) |
Banned By Policy |
Approved (by Policy) |
Mixed |
| 31 |
Unapproved |
Unapproved |
Banned |
Banned |
| 32 |
Approved |
Unapproved |
Banned |
Banned |
| 33 |
Banned |
Unapproved |
Banned |
Banned |
| 34 |
Unapproved |
Approved |
Banned |
Banned |
| 35 |
Approved |
Approved |
Banned |
Banned |
| 36 |
Banned |
Approved |
Banned |
Banned |
| 37 |
Unapproved |
Banned |
Banned |
Banned |
| 38 |
Approved |
Banned |
Banned |
Banned |
| 39 |
Banned |
Banned |
Banned |
Banned |
| 40 |
Unapproved |
Approved By Policy |
Banned (by Policy) |
Mixed |
| 41 |
Approved (by Policy) |
Approved By Policy |
Banned (by Policy) |
Mixed |
| 42 |
Banned (by Policy) |
Approved By Policy |
Banned (by Policy) |
Mixed |
| 43 |
Unapproved |
Banned By Policy |
Banned (by Policy) |
Banned By Policy |
| 44 |
Approved (by Policy) |
Banned By Policy |
Banned (by Policy) |
Mixed |
| 45 |
Banned (by Policy) |
Banned By Policy |
Banned (by Policy) |
Banned By Policy |
| 46 |
Unapproved |
Unapproved |
Mixed* |
Banned |
| 47 |
Approved |
Unapproved |
Mixed* |
Banned |
| 48 |
Banned |
Unapproved |
Mixed* |
Banned |
| 49 |
Unapproved |
Approved |
Mixed* |
Banned |
| 50 |
Approved |
Approved |
Mixed* |
Banned |
| 51 |
Banned |
Approved |
Mixed* |
Banned |
| 52 |
Unapproved |
Banned |
Mixed* |
Banned |
| 53 |
Approved |
Banned |
Mixed* |
Banned |
| 54 |
Banned |
Banned |
Mixed* |
Banned |
| 55 |
Unapproved |
Approved By Policy |
Mixed* (by Policy) |
Mixed |
| 56 |
Approved (by Policy) |
Approved By Policy |
Mixed* (by Policy) |
Mixed |
| 57 |
Banned (by Policy) |
Approved By Policy |
Mixed* (by Policy) |
Mixed |
| 58 |
Unapproved |
Banned By Policy |
Mixed* (by Policy) |
Mixed |
| 59 |
Approved (by Policy) |
Banned By Policy |
Mixed* (by Policy) |
Mixed |
| 60 |
Banned (by Policy) |
Banned By Policy |
Mixed* (by Policy) |
Mixed |