The Enforcement Level for a policy sets the overall security level and determines whether the policy is configured to block or permit execution of Unapproved files. More specific behavior is controlled by detailed policy settings and by rules that apply to a policy.
Detailed policy settings are divided into Device Settings and Advanced Settings, These two settings groups are shown and may be edited on a tabbed panel at the bottom of the Edit Policy page. Advanced Settings are described in the next section. Device Settings are described in Managing Devices
In addition to the settings for a policy, rules managed on other pages may be applied to selected policies or all policies. So that you can see which rules apply to a particular policy, a set of tabbed rule views is included on the Edit Policy page. These are described in Rules Affecting Policies.
Advanced Settings
When active, advanced settings block specified file activities and enforce other rules.
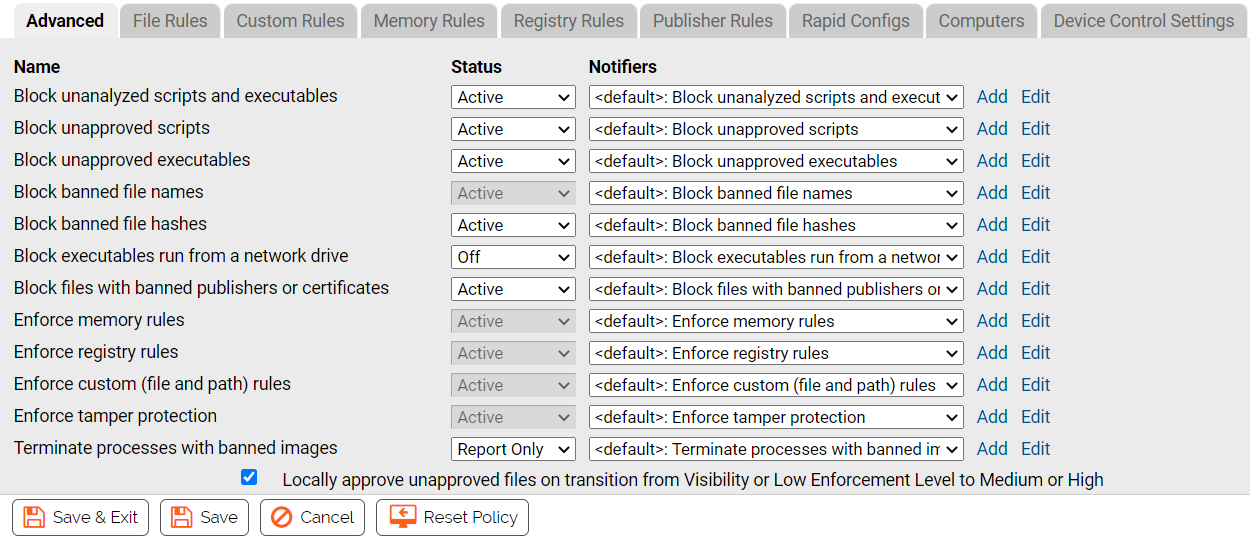
Because any file or activity is usually affected by more than one rule, turning a setting off can have varying results. There are three possible options for advanced settings:
| Setting Options |
Description |
|---|---|
| Active |
Setting is enabled. Files are blocked or permitted according to the specified Enforcement Level. |
| Off |
Setting is disabled and not enforced under any Enforcement Level. Files matching the setting continue to be tracked but are not blocked. |
| Report Only |
A test state that permits actions that would have been blocked if the setting were active and records a would-have-blocked event in the Events table. You can use it to verify that settings and Enforcement Level in a policy work as intended, without actually blocking any files. |
Turning off one setting that blocks an action or file does not necessarily mean the action or file is permitted; similarly, turning off one setting that permits an action does not necessarily mean that the action or file is blocked. The Events page might provide an explanation of why a file you expected to be permitted was blocked.
The table that follows shows the Advanced Settings and the effect of setting them to “Active” or “Off”. Some settings cannot be turned off, but are included so you can change or disable the Notifier that appears when they block a file execution.
-
There are different settings for “executables” and “scripts”. Carbon Black App Control determines whether a file is executable based on content, not file extension alone, while scripts are identified by file extension. After examining a file, the Carbon Black App Control Agent applies the appropriate policy setting based on the file’s content. See Script Rules for information about how scripts are defined.
-
Each setting has a Notifiers menu from which you can choose the notifier that appears on an agent computer when that setting in this policy blocks an action. See Endpoint Notifiers and Approval Requests for details about choosing and defining notifiers.
-
For more about banning software, see Approving and Banning Software. For more about creating custom rules for special treatment of files at certain paths, see Custom Software Rules
| Setting |
Active |
Off |
|---|---|---|
| Block unanalyzed scripts and executables |
Tracks executables (for example, .exe, .dll, and .com) and script files (for example, .bat, .vbs) that have not yet been analyzed and blocks them for systems in High, Medium, and Low Enforcement Levels, and in Local Approval mode. Scripts and executables are reported as unanalyzed if a user or process tries to execute them and Carbon Black App Control cannot finish its run-time checks of file state in the expected time. This usually happens when the root certificate for a file is out of date or otherwise not verifiable. |
Permits unanalyzed executables and script files to execute if no other settings prevent execution. Not recommended. |
| Block unapproved scripts |
Tracks script files (for example, .bat, .vbs) that have an unapproved status and blocks them according to Enforcement Level: High Enforcement Level blocks unapproved scripts. Medium Enforcement Level blocks unapproved scripts but presents a dialog that identifies the file and gives users the option to run it. Low Enforcement Level permits files to execute; records an event the first time the executable runs. Standard Script Rules and File Extensions in Script Rules shows the file types considered scripts by Carbon Black App Control. |
Permits script files not explicitly banned to execute if no other settings prevent execution. |
| Block unapproved executables |
Tracks executable files, for example, .exe, .dll, and .com, that have an unapproved status and blocks or permits them according to Enforcement Level: High Enforcement Level blocks all unapproved executables. Medium Enforcement Level blocks unapproved executables but presents a dialog that identifies the file and gives users the option to run it. Low Enforcement Level permits files to execute; records an event the first time the file runs. |
Permits unapproved files not explicitly banned to execute if no other settings prevent execution. |
| Block banned file names |
Blocks execution of files banned by file name on computers in Control mode. |
Cannot be disabled on the policy page, but individual bans can be made policy-specific. |
| Block banned file hashes |
Blocks all banned hashes on computers in Control mode. |
Disables the Banned Hashes setting and permits banned hashes to execute if no other settings prevent it. |
| Block executables run from a network drive |
Blocks execution of files (including Approved files) run over the network on computers in Control mode. Platform Note: This setting is effective for Windows agents only. |
Permits network executable files not unapproved or explicitly banned to execute if no other settings prevent it. |
| Block files with banned publishers or certificates |
Blocks execution of files with banned publishers (or certificates) in Control mode. |
Permits files with banned publishers/certificates to execute if no other settings prevent it. |
| Enforce memory rules |
Apply all enabled memory access, control, and reporting rules. Platform Note: This setting is effective for Windows agents only. |
Cannot be disabled on the policy page, but individual rules can be made policy-specific. |
| Enforce registry rules |
Apply all enabled registry access and reporting rules to this policy. Platform Note: This setting is effective for Windows agents only. |
Cannot be disabled on the policy page, but individual rules can be made policy-specific. |
| Enforce custom (file and path) rules |
Apply all enabled custom rules (special treatment of files at defined paths) to this policy. You configure custom rules on the Custom Rules tab of the Software Rules page. |
Cannot be disabled on the policy page, but individual rules can be made policy-specific. |
| Enforce tamper protection |
Apply rules to prevent tampering with an Carbon Black App Control Agent. |
Cannot be disabled for a policy. Use the Computer Details page to disable for a specific computer. |
| Terminate processes with banned images |
When a file is banned, terminate currently running processes that match the file. |
Permits a file banned while already running to continue running. |
| Locally approve unapproved files on transition from Visibility or Low Enforcement Level to Medium or High |
When checked, causes certain Unapproved files to be locally approved when the policy Enforcement Level changes from Low (or None) to Medium or High. This only applies to files that first appeared on the computer as Unapproved when the computer was in a Low (or None) Enforcement Level policy. These files have Local State Details of “Unapproved”. See Locally Approving Files for details. |
When not checked, Enforcement Level changes do not affect local file state in this policy. |