To include image scanning in your continuous integration script, configure and use the Carbon Black Cloud CLI Client (Cbctl). This client is available for Linux and macOS.
You can install the CLI client on a Dev/Sec/Ops machine, or you can include it in a CI/CD pipeline — for example, Jenkins or Gitlab. The CLI client requires an Internet connection to Carbon Black Cloud and access to your container registries.
Carbon Black CLI Client performs an image scan for known vulnerabilities and enforces security or compliance rules. The CLI Client performs the following tasks:
- Vulnerabilities scanning of container images.
Container images are matched against a known vulnerabilities database. The image details include operating system and non-operating system packages, libraries, licenses, binaries, and metadata. The vulnerabilities scan result is included in the image metadata.
- Enforcing standards for container images.
To evaluate policy violations, the image scan results are matched against a specific policy that is configured for the CLI scope. The CLI run fails the build pipeline step if policy violations are detected. The violation of policy rules is added to the image metadata together with image rule exceptions.
- Enforcing standards for Kubernetes workloads.
Kubernetes workloads are matched against a Kubernetes hardening policy to evaluate the workload compliance for security risks. By leveraging the information from both image vulnerabilities and workload configuration, a complete picture of the workload risk exposure is available.
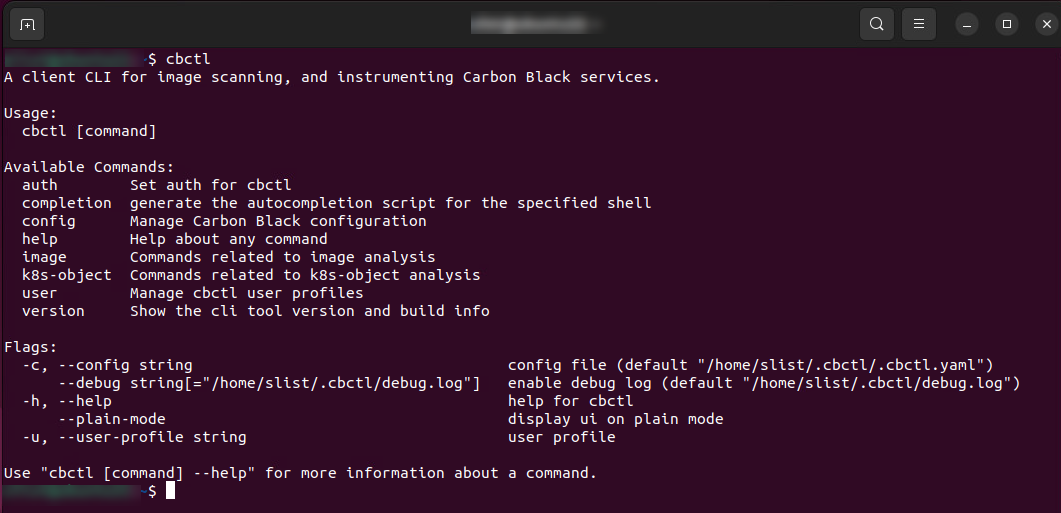
The CLI client presents the following interface and command options:
Secrets File Detection
If secret detection is enabled, Carbon Black Cloud detects all text files in an image. Files can be ignored; these are specified by using CLI flags. System files are ignored by default to reduce scan time.
| Flag | Description | Default Setting |
|---|---|---|
enableSecretDetection |
Indicates whether the scan should scan for secrets | False |
skipDirsOrFiles |
Files or directories to not scan for secrets | N/A |
scanBaseLayers |
Indicates whether the scan should scan the base layers for secrets | False |
ignoreBuildInRegex |
Indicates whether the scan should ignore the build-in regexes of files | False |