Permissions allow Carbon Black Cloud Endpoint Standard customers to permit specific process behaviors to tune prevention efficacy; for example, to minimize false positives and unwanted preventions.
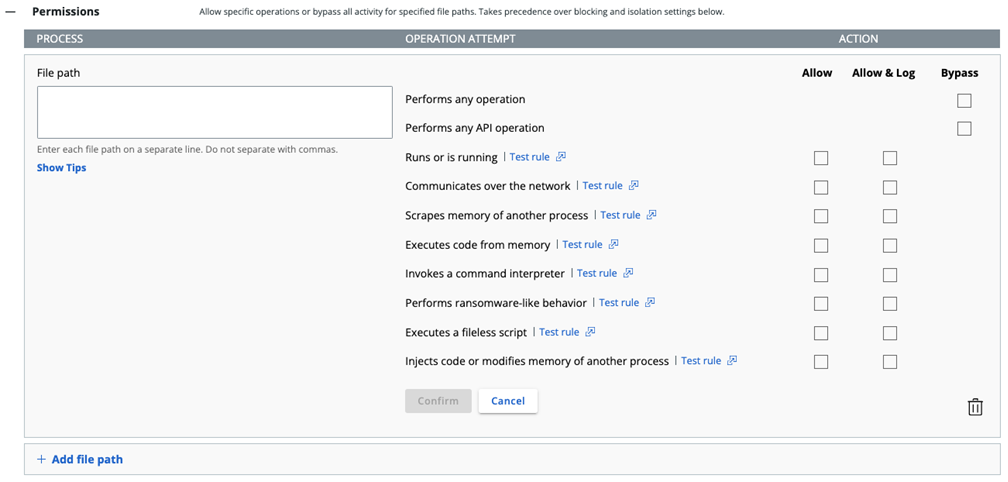
To apply a Permission, you must define a combination of the following criteria:
- one or more processes, specified by file path
- one or more Operation Attempt (behavior) categories
- the permitted Action (Allow, Allow & Log, or Bypass) for each selected Operation Attempt
Permissions features some nuances:
- Descendant processes inherit the Permission by default.
- The application specified by its file path is affected in the context of it being both the actor (the source process) and the target (the target file path of other processes). This means that the specified activity of the process that exists at the specified file path is permitted, and other process activity that occurs at the specified file path is permitted too.
For more information about Permissions, see Prevention Policy Settings.
Recommendation: The Permissions feature is primarily intended to be used for prevention efficacy tuning and false positive reduction for non-Core Preventions. Use the Core Prevention Exclusions feature to tune the efficacy of Core Preventions. See Comparing Permissions to Core Prevention Exclusions.
Historically, Carbon Black Cloud Endpoint Standard customers were instructed to use Performs any operation - Bypass or Performs any API operation - Bypass to address performance issues. Moving forward, the Permissions feature should largely be used only for prevention efficacy tuning. Use instead Event Reporting and Sensor Operation Exclusions to address performance or operational issues. Event Reporting and Sensor Operation Exclusions are more customizable and therefore enable the creation of narrower exclusions. See Comparing Permissions, Core Prevention Exclusions, and Event Reporting and Sensor Operation Exclusions.
We recommend that Carbon Black Cloud Endpoint Standard customers replace Performs any operation - Bypass Permissions that are intended to resolve performance issues with Event Reporting and Sensor Operation Exclusions.
We recommend that customers who have Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR replace Performs any operation - Bypass Permissions that are intended to resolve performance issues with NGAV Reporting and Sensor Operations Exclusions (scoped to Carbon Black Cloud Endpoint Standard) or All Reporting and Sensor Operations Exclusions (scoped to Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR).