Event Reporting and Sensor Operation Exclusions allows Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR customers to enforce process-based exclusions to address operational issues, such as network performance issues, endpoint performance issues, or interoperability issues with third-party software.
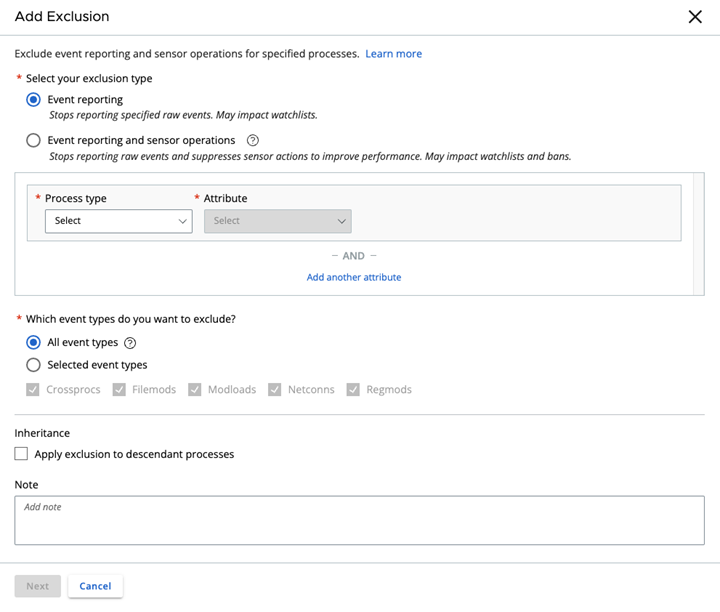
Event Reporting and Sensor Operation Exclusions are similar to Core Prevention Exclusions because they both allow you to specify the process criteria by defining the certificate information, command line, file path, and/or SHA-256 hash of the process or its parent process.
Event Reporting and Sensor Operation Exclusions are different from Core Prevention Exclusions in a few key ways:
- Event Reporting and Sensor Operation Exclusions address operational issue use cases, while Core Prevention Exclusions address prevention efficacy use cases such as eliminating unwanted preventions and reducing false-positive alerts.
- There are multiple forms of Event Reporting and Sensor Operation Exclusions. Each supports different configuration options. There is a singular form of Core Prevention Exclusion, which is the same across each Core Prevention type.
- Depending on the type of Event Reporting and Sensor Operation Exclusion that is used and the products in scope, the exclusion suppresses the reporting of raw events associated with Carbon Black Cloud Enterprise EDR and Observations associated with Carbon Black Cloud Endpoint Standard. A Core Prevention Exclusion prevents unwanted preventions and alerts, but the underlying events associated with those preventions and alerts are reported on the Investigate page.
Additionally, Event Reporting and Sensor Operation Exclusions are different from Permissions the following key ways:
- For customers who have Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR, a form of the Event Reporting and Sensor Operation Exclusions feature (All Reporting and Sensor Operations Exclusion) can be used to tune the behavior of both products. The Permissions feature only applies to Carbon Black Cloud Endpoint Standard.
- Event Reporting and Sensor Operation Exclusions support specification of process criteria by defining the certificate information, command line, file path, and SHA-256 hash of the process or its parent process, while Permissions only support specification of process criteria by defining the file path of the process.
- Event Reporting and Sensor Operation Exclusions support configurable inheritance by descendant processes for certain configurations, while inheritance by descendant processes is a default, non-configurable trait of Permissions.
- With the Event Reporting and Sensor Operation Exclusions feature, when a process is specified by its file path, the file path is interpreted in a single context: it is used to identify the initiator of the excluded activity. However, with the Permissions feature, the file path that is used to specify the process is interpreted in two contexts: it identifies the initiator of the permitted operation attempt and it identifies the target file path where the permitted operation attempt occurs. In other words, Permissions apply to process operation attempts that are executed from that file path and to operation attempts that occur at that file path.
See Event Reporting and Sensor Operation Exclusions.
Recommendation: Unlike Permissions and Core Prevention Exclusions, which are focused on tuning preventions to eliminate unwanted blocks and reduce false positives, Event Reporting and Sensor Operation Exclusions are focused on resolving operational issues such as network performance, endpoint performance, or interoperability issues with third-party software.
Instead of enforcing an overly broad Bypass of a process using the Permissions feature or placing the sensor into Bypass mode to address an operational issue (when Bypass is intended to be used as a temporary troubleshooting measure), we recommend that you use the more appropriate and more customizable Event Reporting and Sensor Operation Exclusions feature to address operational issues.
We recommend that Carbon Black Cloud Endpoint Standard customers who have implemented a Permissions setting to address a performance issue replace that setting with an Event Reporting and Sensor Operations Exclusion.
For customers who have Carbon Black Cloud Endpoint Standard and Carbon Black Cloud Enterprise EDR, the most direct replacement for a Permissions Performs any operation - Bypass is the NGAV Reporting and Sensor Operations Exclusion. This form of an Event Reporting and Sensor Operations Exclusion is scoped to only impact Carbon Black Cloud Endpoint Standard.