Perform the following procedure to initialize and configure a new Carbon Black EDR Server.
Prerequisites
- If you are installing a Carbon Black EDR server in a FIPS-enabled environment, see Enable FIPS Mode on a RHEL 8 Machine and Configure OpenSSH on RHEL 8 in FIPS Mode.
- Install a new server using the steps described in Install a New Server or Installing Carbon Black EDR on an Air-Gapped Server.
Procedure
- Run the following command on the new server. If you plan to use the server-provided certificate to secure communications with sensors, no arguments are necessary.
sudo /usr/share/cb/cbinit
To substitute your own certificate, add the following arguments to thecbinitcommand, substituting the full path to a certificate file and a key file where shown:--server-cert-file= <certpath> --server-cert-key= <keypath>
Important: See Substituting a Server Communication Certificate for certificate requirements. - Press [Return] to open the EULA. When you are done reviewing it, if you agree to the terms, type q and then type yes to continue.
- Select a storage location for your data and press [Return].
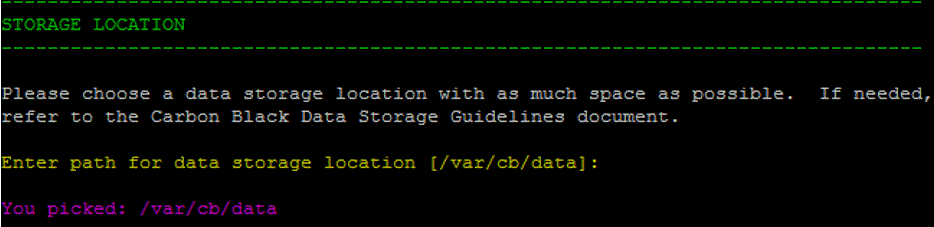 Note: By default, the primary datastore is mapped to /var/cb/data. If you configured your storage differently, review your current file system mapping
Note: By default, the primary datastore is mapped to /var/cb/data. If you configured your storage differently, review your current file system mapping(df -h)with Carbon Black Support or Professional Services. Incorrect or insufficient disk configurations prevent Carbon Black EDR from operating correctly. - Enter an initial Administrator account to log in and configure Carbon Black EDR. Enter values for Username, First Name, Last Name, E-Mail, Password, and Confirm password:
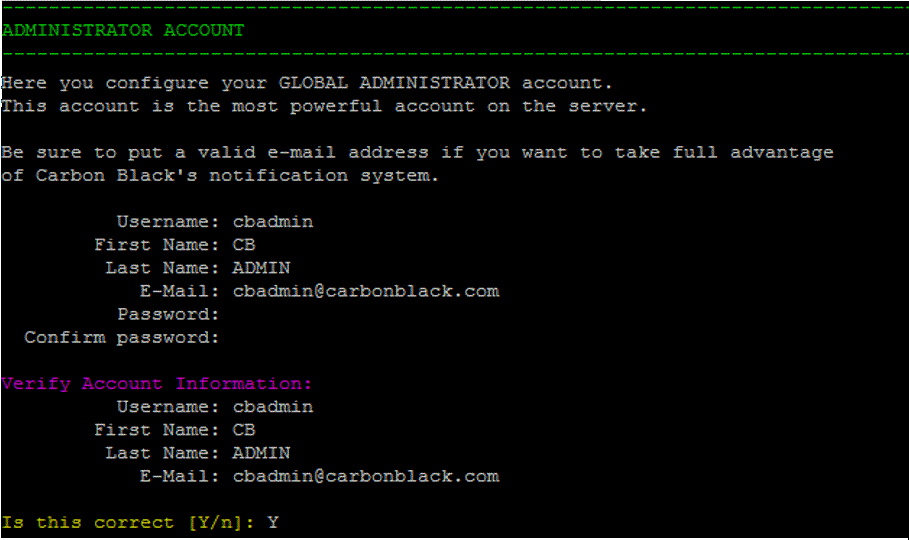
- Press [Enter] and then validate the account information by typing y.
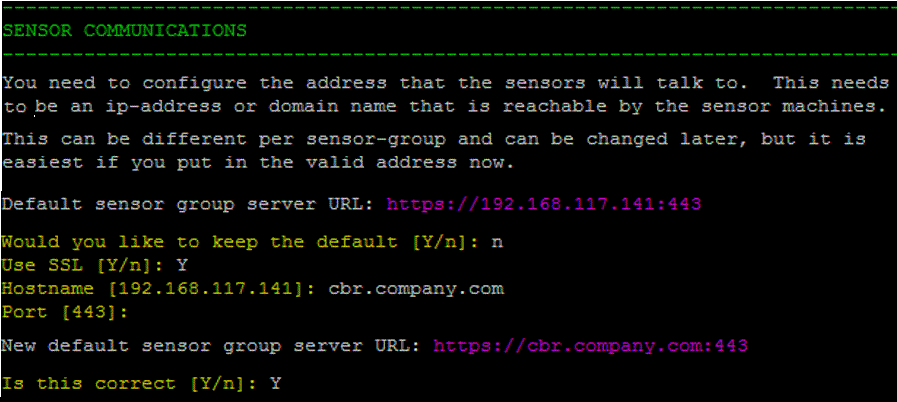
- In the Sensor Communications section, define the address that the sensors will use to communicate to the Carbon Black EDR server:
Would you like to keep the default [Y/n]: n Use SSL [Y/n]: Y Hostname [192.168.117.141]: cbr.example.com Port [443]: return If the Verify Account Information looks correct, Y
Note: The IP address of the server is accessed via the default SSL port 433. A best practice is to use a DNS record that points to this IP address.Work with Carbon Black Support or Professional Services to make sure that you understand the external connectivity options supported by the Carbon Black EDR server.
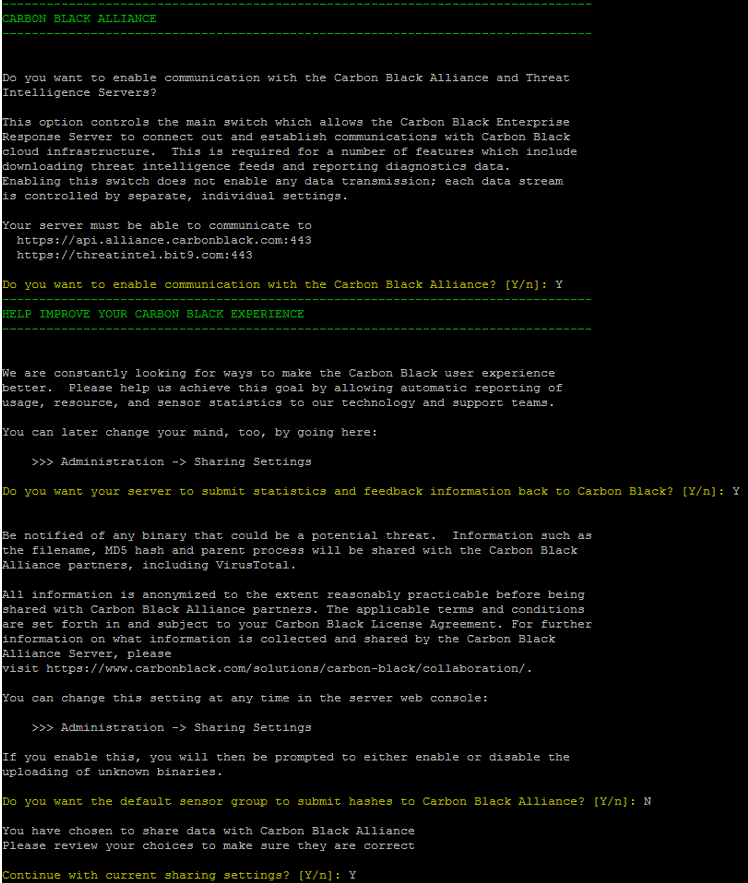
- Review all prompts and configure sharing settings in accordance with your company’s security policies. The recommended settings are provided here. You can change these settings at any time by accessing the Carbon Black EDR console and clicking Username> Sharing Settings.
-
This enables the program to be supplemented with updated threat intelligence from Carbon Black Threat Intel and the extended network of Carbon Black Threat Intel partners.
Do you want to enable communication with the Carbon Black Alliance? – Y
-
Do you want your server to submit statistics and feedback information to Carbon Black? – Y
This enables the server to submit health statistics to Carbon Black EDR. These are used by Carbon Black Support and Professional Services to determine how the allocated server is performing.
-
Do you want the default sensor group to submit hashes to Carbon Black Alliance? – N
See “Threat Intelligence Feeds” in the Carbon Black EDR User Guide for more information on sharing hashes with Carbon Black EDR.
- Continue with current sharing settings? – Y
-
- The SSL Certificates section is automated and requires no user input. If you used arguments pointing to valid certificate and key files when you ran
cbinit, the certificate from your organization is substituted for the default certificate that the server creates. See Substituting a Server Communication Certificate and the Carbon Black EDR User Guide for more information.Run the following script to create an encrypted backup of your certificates. The exact certificates are critical to disaster recovery efforts./usr/share/cb/cbssl backup --out <backup_file_name>
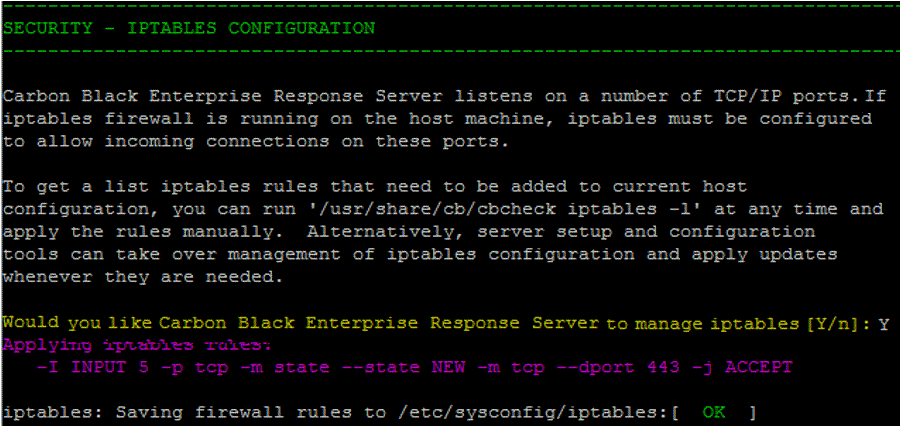
- In the IP Tables section, answer Y. This opens port 433 in the server’s IP tables.
- The POSTGRESQL Database Setup section is automated and requires no user input.
- If you have a FIPS-enabled environment, see Solr FIPS before starting the services.
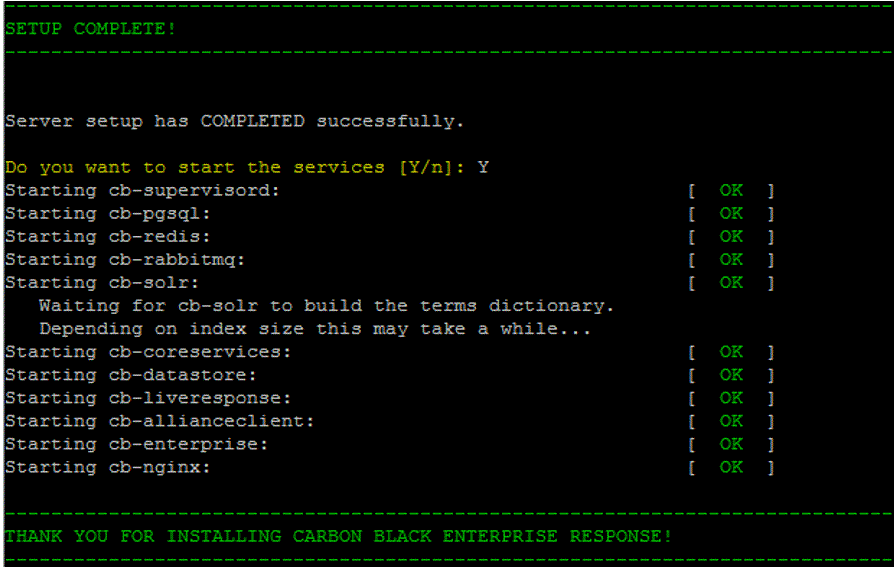
- In the Setup Complete section, enter Y to start the services.
- Configure the firewall if you have not already done so. There are many ways to configure a firewall. The following is an example for CentOS 6.
- Open port 443 if you did not allow the
cbinitscript to manage iptables for you.[jdoe@localhost yum.repos.d]$ sudo vim /etc/sysconfig/iptables # Firewall configuration written by system-config-firewall # Manual customization of this file is not recommended. *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited # New additions to the IPTABLES for carbon black -A INPUT -m state --state NEW -m tcp -p tcp --dport 443 -j ACCEPT COMMIT
- (Optional) Open port 80 to allow use of web interface and sensor communications through an unsecured channel. This is not required and only recommended for exploration or troubleshooting. Connections to the web interface through port 80 are redirected to port 443.
- Open port 443 if you did not allow the
- Log into the Carbon Black EDR server web console at https://<your server address>/ and use the username and password that you set up in the
cbinitscript.Note: Google Chrome is the only supported browser for this release.After you have installed, configured, and initialized Carbon Black EDR, it should be accessible through the web interface on port 443 with a self-signed certificate. If you attempt to access the web interface through HTTP on port 80, the connection is redirected to port 443.
To enable Redis network encryption, see Enable Redis Network Encryption.