The Carbon Black EDR server uses virtual server names to allow multiple active routes to the server using the same real address and port.
Each virtual name and route uses a different certificate, as depicted in the following schematic. This implementation is done via runtime server blocks in NGINX configuration files.
Virtual server names are parsed from a SAN.DNS entry in the certificate so that each certificate can be validated from the sensor’s perspective.
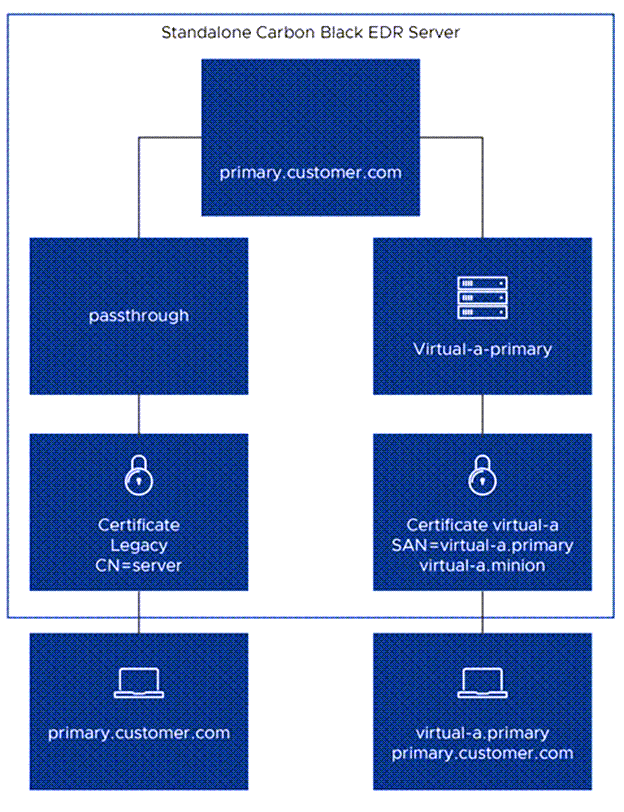
Sensors use the Server Name Indication (SNI) extension to the TLS protocol handshake to access a specific route and certificate. The Legacy certificate remains available without any SNI indications so that older sensor versions are able to use it to access the server.
Sensors confirm the resolution of virtual names to addresses internally; for example, resolution from "virtual-a.primary" in the preceding certificate example to the actual "primary.customer.com" server address. That means that virtual server addresses do not need to be added to external DNS servers.
On an upgrade to Carbon Black EDR 6.4.0, the previously used self-signed certificate is named "Legacy" and would be served via the default server access route (using no virtual servers), which is supported for all sensor versions and configurations. New server installations also include a "Legacy" certificate.
If you are using a Reverse Proxy, you must manually configure your Reverse Proxy to match the SNI configuration in your server environment. Contact Carbon Black Support for additional details.