The following schematic describes some details of the clustered server set up with TLS certificate management. Although the legacy route is not depicted in this schematic for readability, it does exist and works in a cluster just as it does in a standalone scenario.
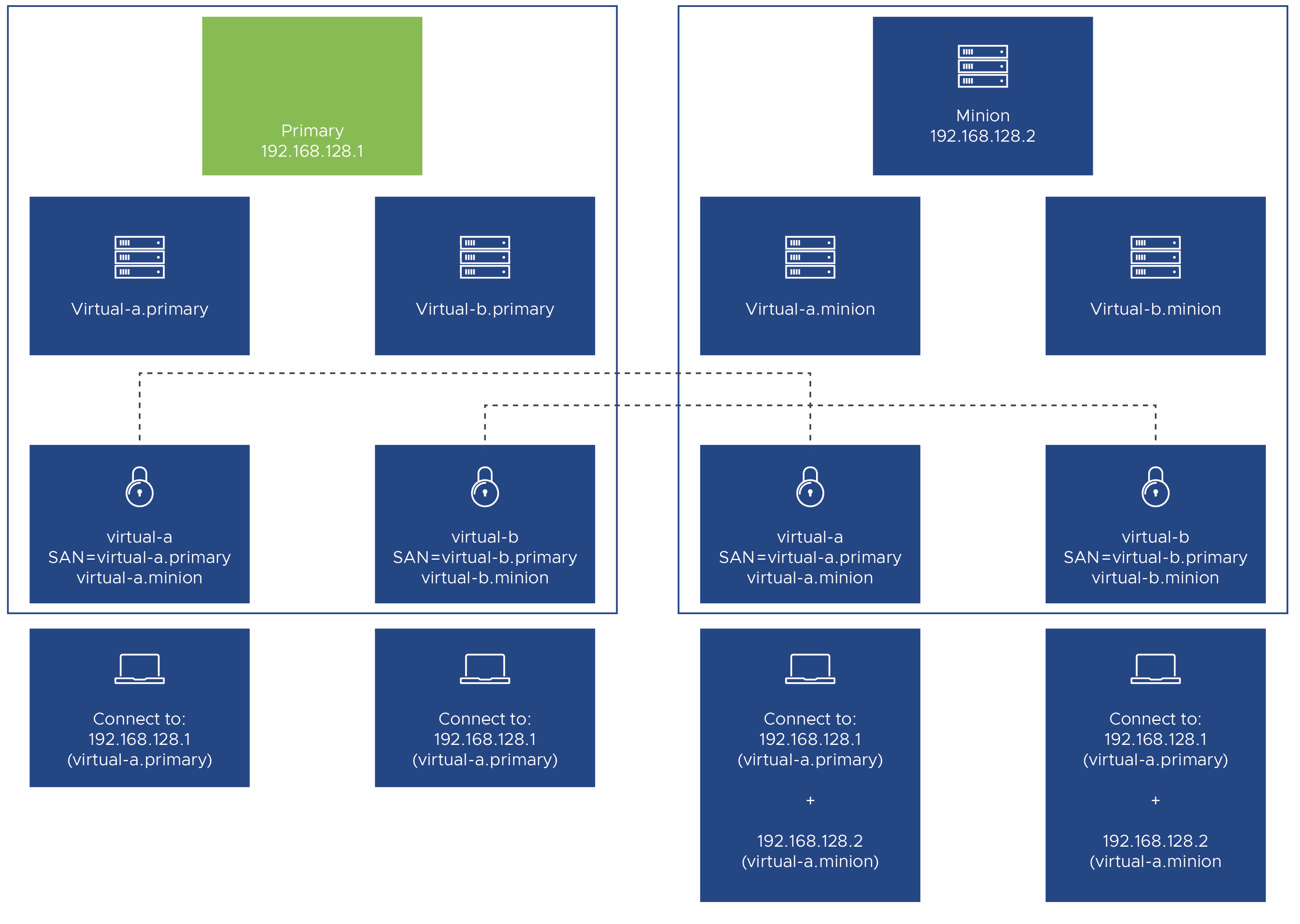
When TLS certificate management is used in a cluster environment:
-
Added TLS certificates are automatically copied to minions.
-
Virtual server names are replicated on minions.
-
Sensors expect the same server certificate to be present on primary and the minion.
-
Server certificates support the switch from standalone to cluster or adding new nodes without having to re-issue certificates. This is the reason why the certificates must have two distinct SAN DNS entries.
-
Sensors need to distinguish only two different virtual addresses to communicate to the servers (primary and minion). Because resolution of those virtual names happens internally, and virtual minion addresses can get mapped to different real addresses, there is no need for SAN DNS entries for each individual minion in a cluster.