VMware Cloud Director Container Service Extension 4.1 and newer versions can support airgapped environments, and the use of local container registries.
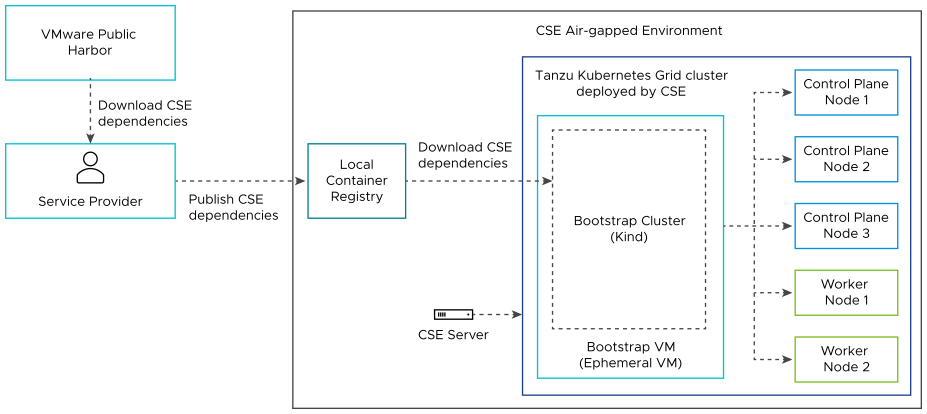
Local Container Registry
Service providers set up system wide local container registries using Harbor that contain image files from VMware Public Harbor, that allow tenant users to operate VMware Cloud Director Container Service Extension 4.1.x in an airgapped environment. This type of environment means tenant users can operate VMware Cloud Director Container Service Extension fully within the boundaries of their organization data center without the requirement of Internet access.
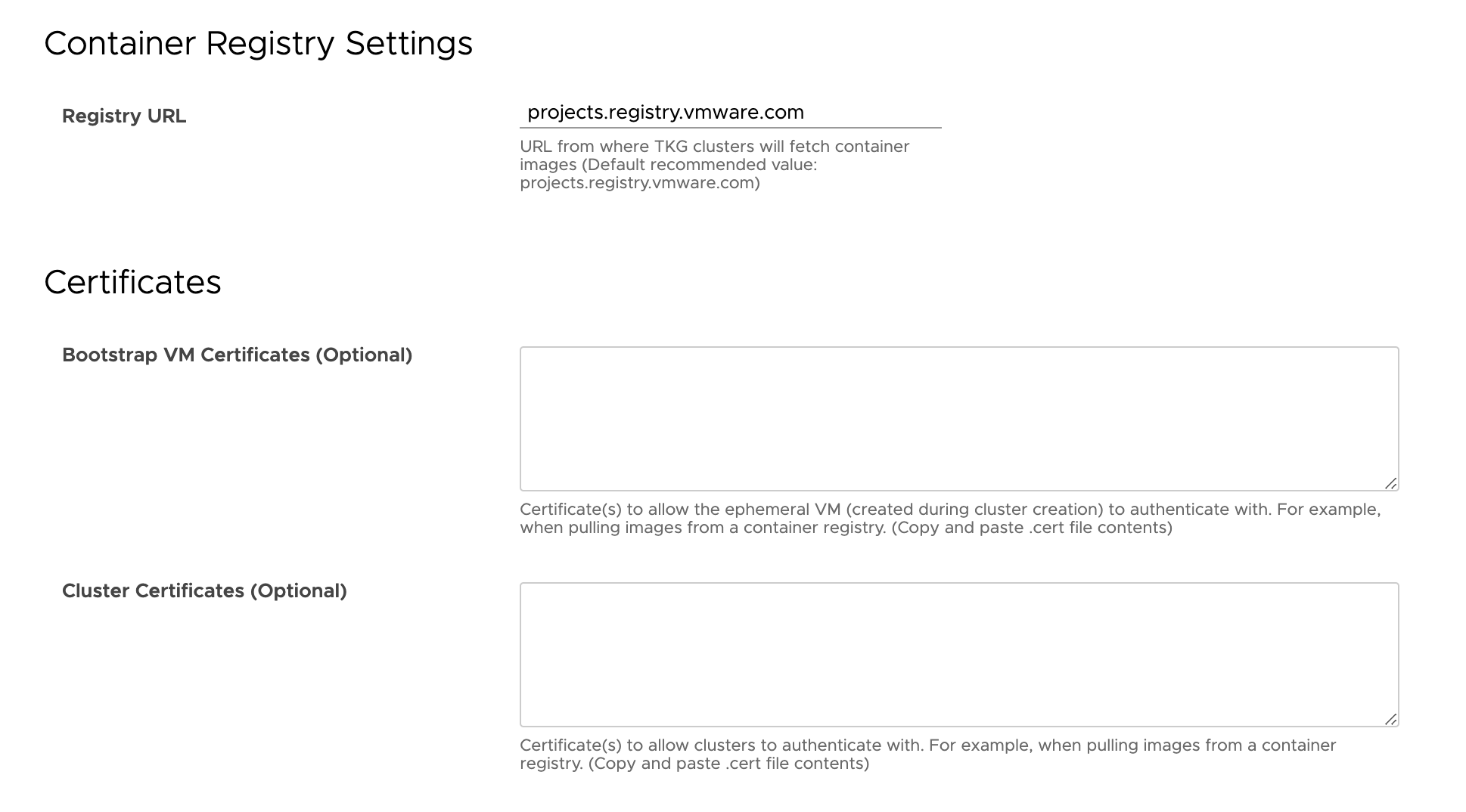
During the VMware Cloud Director Container Service Extension 4.1.x server configuration workflow, service providers specify the local container registry URL in the Container Registry Settings tab of the Configure Settings for CSE Server section in Kubernetes Container Clusters 4.1.x UI plug-in. Therefore, when tenant users attempt to create a Tanzu Kubernetes Grid cluster in the Kubernetes Container Clusters 4.1.x UI plug-in, it instructs Kubernetes Cluster API Provider for VMware Cloud Director, the Bootstrap VM, control planes, and worker nodes within the cluster to use the specified local container registry. For more information on configuring the local container registry details, see Server Details. Service providers can also tailor private registries for organizations that allow organizations to control what files are published and accessible to their tenant users.
Create an Airgapped Environment
As as a service provider, you must perform the necessary steps to set up a VMware Cloud Director Container Service Extension airgapped environment, and create a local container registry for tenant users that contains the dependencies that VMware Cloud Director Container Service Extension requires to operate.
Prerequisites
- Ensure you have Docker engine or cli, and imgpkg installed on your local machine.
- To install Docker, see Docker Desktop
- To install imgpkg, see Carvel: imgpkg
- Ensure the VMware Cloud Director Container Service Extension server, and the desired tenant data centers have access to the VMware Cloud Director public end point. This is necessary as the Bootstrap VM, Kubernetes Cloud Provider for VMware Cloud Director, Kubernetes Cluster API Provider for VMware Cloud Director, and Kubernetes Container Storage Interface driver for VMware Cloud Director make calls to it.
- DNS server to resolve registry and VMware Cloud Director end point.
- Provide a Local Container Registry URL for the Bootstrap VM and all other control plane or worker VM can pull images from. For more information, see Local Container Registry.
- If the private registry is using self-signed certificates, update the Bootstrap VM and the Cluster Certificate section with the self-signed certificates. This step allows cluster virtual machines like Bootstrap VM and node VMs to trust the private registry. For more information, see Server Details.
The following screenshot details the workflow to configure the container registry settings and certificates in Kubernetes Container Clusters UI plug-in for VMware Cloud Director:
- Ensure you have access to the Internet to download the VMware Cloud Director Container Service Extension binaries from http://projects.registry.vmware.com to your local machine.