VMware Cloud Director Container Service Extension 4.1 and later support air-gapped environments and the use of local container registries.
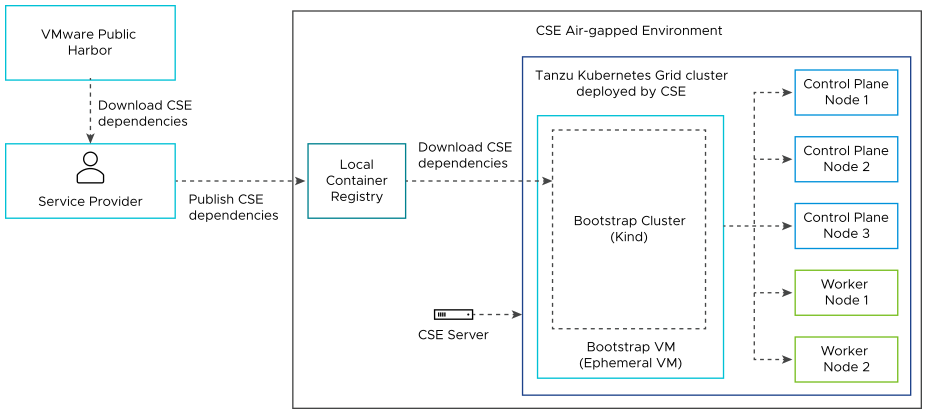
Local Container Registry
Service providers set up system wide local container registries using Harbor that contain image files from VMware Public Harbor, that allow tenant users to operate VMware Cloud Director Container Service Extension in an air-gapped environment. This type of environment means tenant users can operate VMware Cloud Director Container Service Extension fully within the boundaries of their organization data center without the requirement of Internet access.
During the VMware Cloud Director Container Service Extension server configuration workflow, service providers specify the local container registry URL in the Container Registry Settings tab of the Configure Settings for CSE Server section in Kubernetes Container Clusters UI plug-in. Therefore, when tenant users attempt to create a Tanzu Kubernetes Grid cluster in the Kubernetes Container Clusters UI plug-in, it instructs Kubernetes Cluster API Provider for VMware Cloud Director, the Bootstrap VM, control planes, and worker nodes within the cluster to use the specified local container registry. For more information on configuring the local container registry details, see Server Details. Service providers can also tailor private registries for organizations that allow organizations to control what files are published and accessible to their tenant users.