To configure an LDAP connection, you set the details of your LDAP server. You can test the connection to make sure that you entered the correct settings and the user and group attributes are mapped correctly. When you have a successful LDAP connection, you can synchronize the user and group information with the LDAP server at any time.
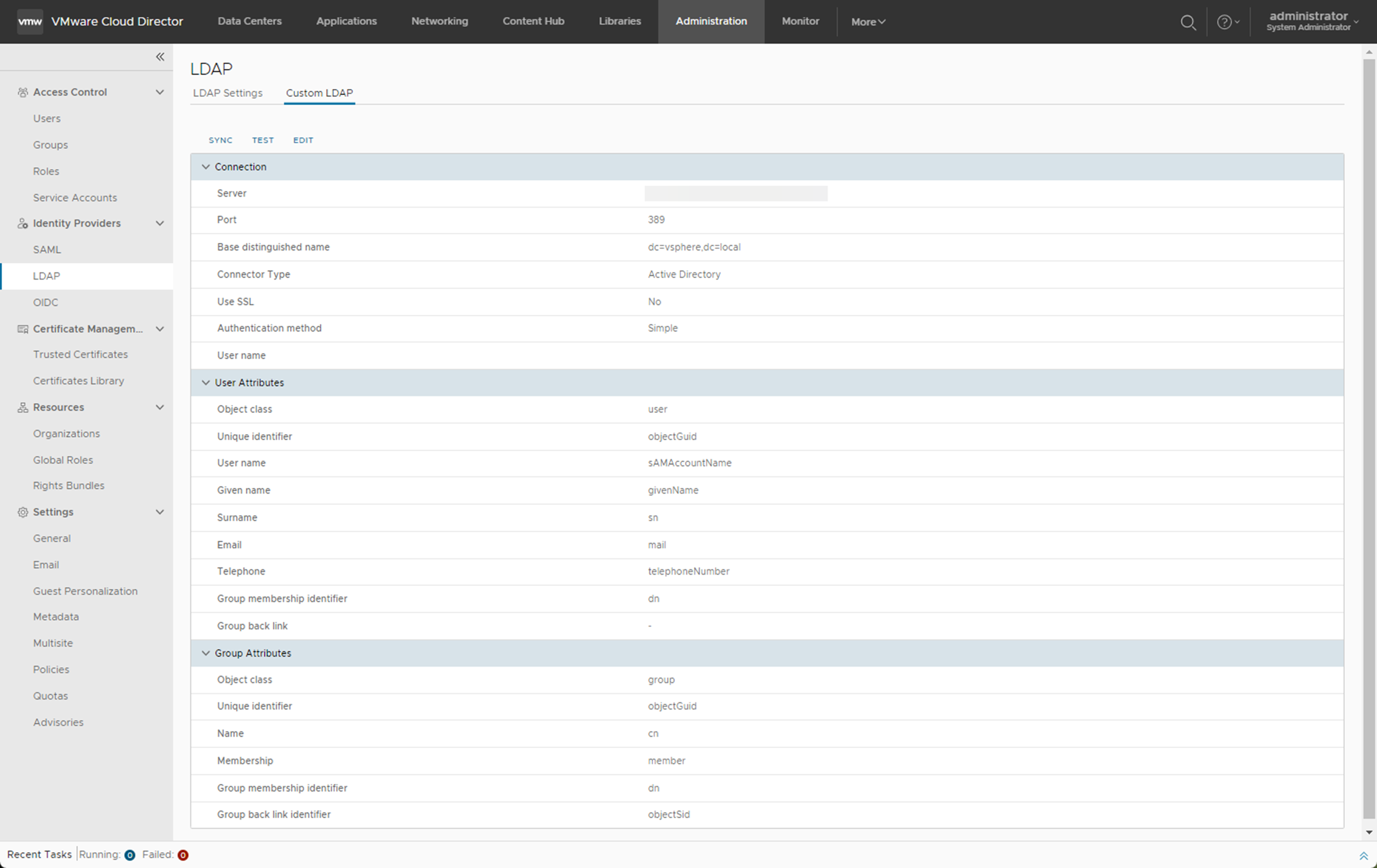
Prerequisites
-
If you plan to connect to an LDAP server over SSL (LDAPS), verify that the certificate of your LDAP server is compliant with the Endpoint Identification introduced in Java 8 Update 181. The common name (CN) or the subject alternative name (SAN) of the certificate must match the FQDN of the LDAP server. For more information, see the Java 8 Release Changes at https://www.java.com.
Verify that you are logged in as an organization administrator or a role with equivalent set of rights.
- If you want to use SSL, you can test the connection to the LDAP server and establish a trust relationship with it. See Test the VMware Cloud Director Connection to a Remote Server and Establish a Trust Relationship Using the Tenant Portal.