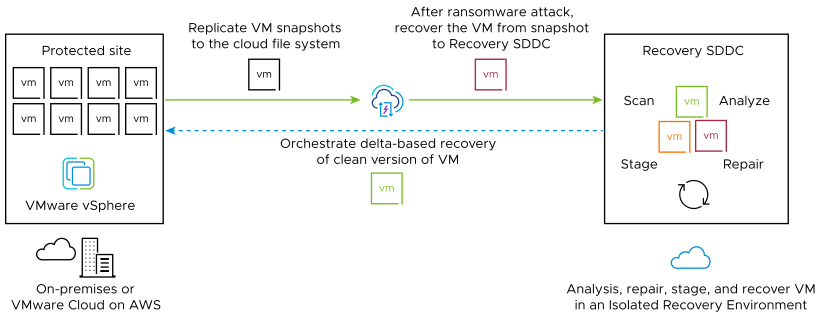
VMware Ransomware Recovery provides an on-demand, cloud-based isolated recovery environment (IRE) with integrated security and behavior analysis tools that help you recover from a ransomware attack using cloud backups (snapshots).
The Problem
Ransomware has emerged as a dominant threat to enterprise IT, with Gartner estimating that 75% of organizations will be affected by ransomware by 2025. Businesses affected by ransomware can often recover data from backups, although the cost of recovery in terms of time, loss of business, and partial data loss remains high.
Traditional backup and restore solutions are not designed to easily recover from a ransomware attack, and the process is costly and time consuming. After a ransomware attack, it is nearly impossible to be certain that backups are not infected without explicit validation. In many cases, the most recent backup data is likely compromised.
The ransomware recovery administrator must assume that malware is embedded in the backup data. Unlike disaster recovery, backups must be either validated or cleansed during the ransomware recovery process to avoid reintroducing ransomware into a production environment.
What the ransomware administrator needs is an air-gapped staging area for infected VMs that is isolated from other networks, so the forensic and remediation processes can occur without external ransomware triggers and without the risk of infecting other workloads in production.
The Solution
- On-demand, cloud-based (IRE) with predefined network isolation levels. The VMware Live Cyber Recovery recovery SDDC provides a network-restricted IRE on VMware Cloud on AWS as a cost effective solution which does not require building an environment from scratch and patching together different tools and hardware. After a ransomware attack, you can launch a recovery plan and select VMs from a deep snapshot history to be placed into an IRE for forensic analysis and validation. For more information, see Configuring the Ransomware Recovery Isolated Recovery Environment (IRE).
- Use the recovery SDDC ro recover and run cleansed production workloads. You can create separate VMware Cloud Gateways on the recovery SDDC for recovering and running production VMs. For those cases where the original protected site is unavailable, creating a separate gateway on the recovery SDDC allows you to perform ransomware recovery and cleanse infected VMs, and then recover clean VMs to a production network environment on the same recovery SDDC. These production VMs can be failed back to a protected site once it becomes available.
- Deep integrated security and vulnerability analysis. VMware Ransomware Recovery provides access to continuous cloud scanning systems that analyze each VM in recovery for suspicious OS behaviors, malware file signatures, and known vulnerabilities.
- Recovery orchestration. You can configure recovery plans to automatically move protected VMs to the recovery SDDC for analysis and validation. When you have succeeded in finding clean VMs, you can orchestrate those VMs back to a protected production site.
For more information, see Ransomware Recovery.