Describes in detail how to configure a Secure Sockets Layer (SSL) Inspection rule for a selected Security Policy.
Before you begin
To configure a Security Policy, users must have first created a Security Policy. For specific instructions on how to create a Security Policy, see Creating a Security Policy.
SSL Inspection Category
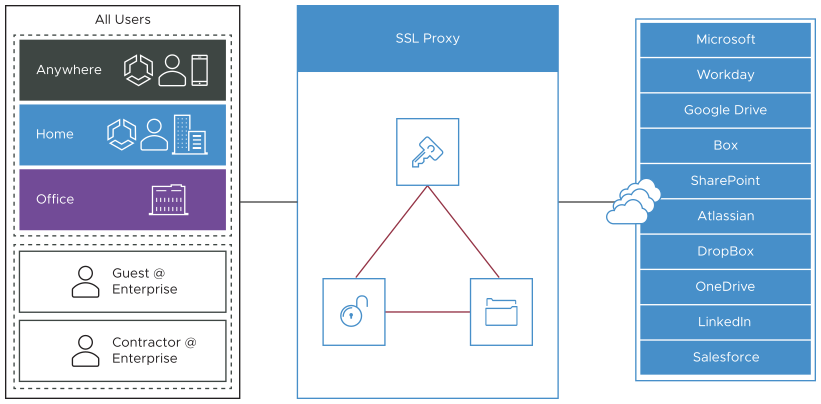
However, some traffic does not like having a “man in the middle” for its traffic in the way that the SSL Inspection works. This includes traffic using certificate pinning, Mutual TLS (mTLS) and some using WebSockets. To ensure Cloud Web Security does not break these kinds of traffic, users can configure exceptions to this default SSL Inspection rule, which would allow the traffic to bypass SSL Inspection.
The SSL Root CA certificate can be downloaded by clicking on SSL Certificate on the left side of the Cloud Web Security > Configure > Enterprise Settings menu.
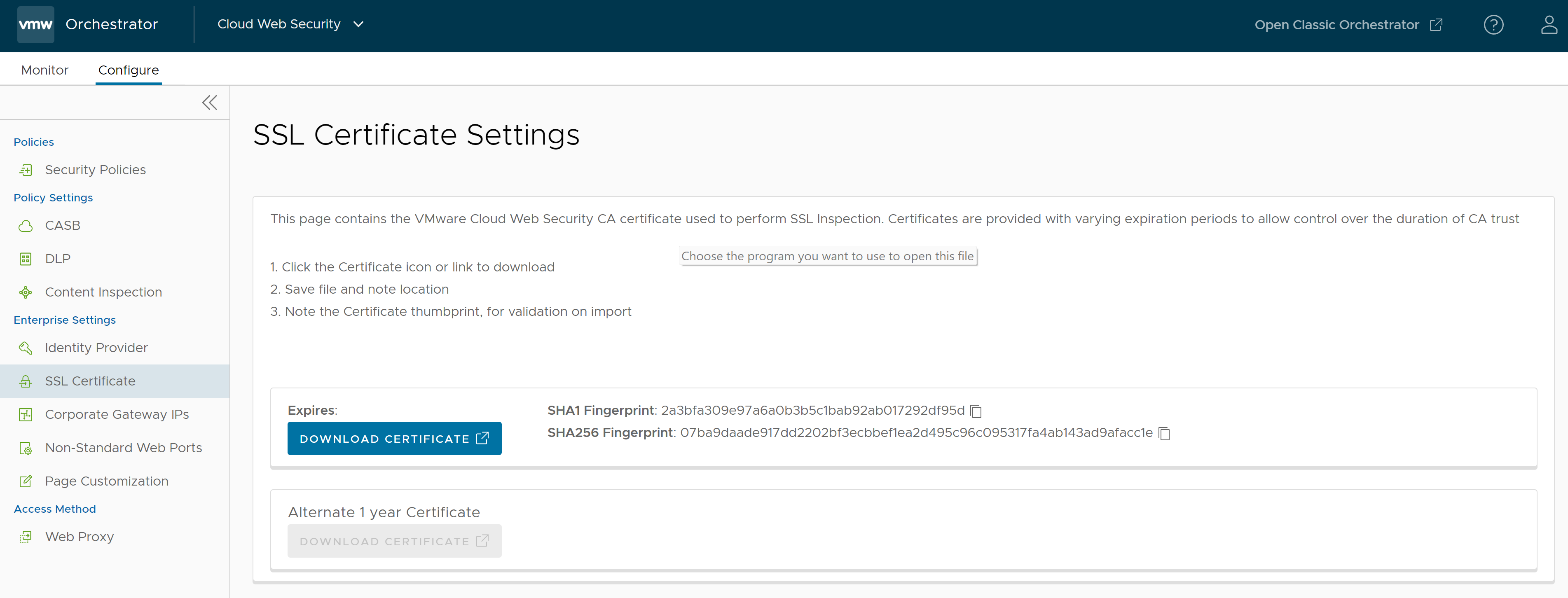
- Click the Certificate icon or link to download.
- Save file and note location.
- Note the Certificate thumbprint, for validation on import.
Configure an SSL Inspection Rule
Manual SSL Bypass
- Navigate to .
- Select a security policy to configure SSL inspection rule and then click the SSL Inspection tab.
- In the SSL Inspection tab of the Security Policies screen, click + ADD RULE to configure an SSL Inspection Exception rule.
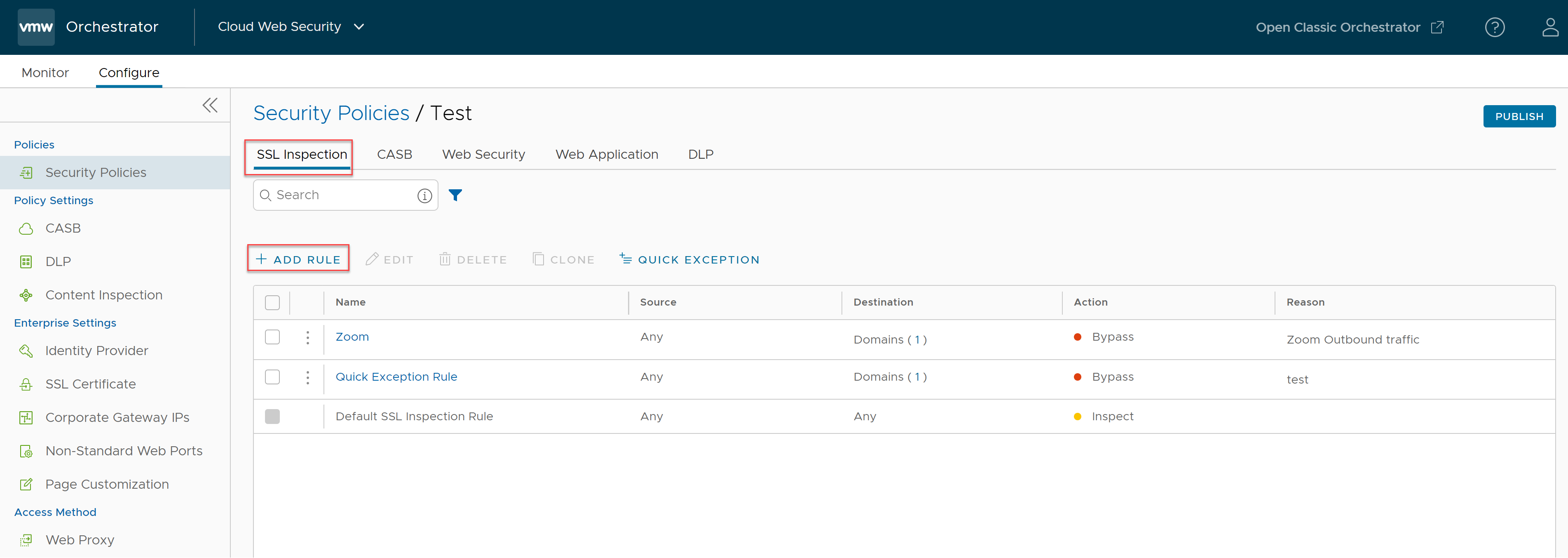
The Create SSL Exception screen appears.
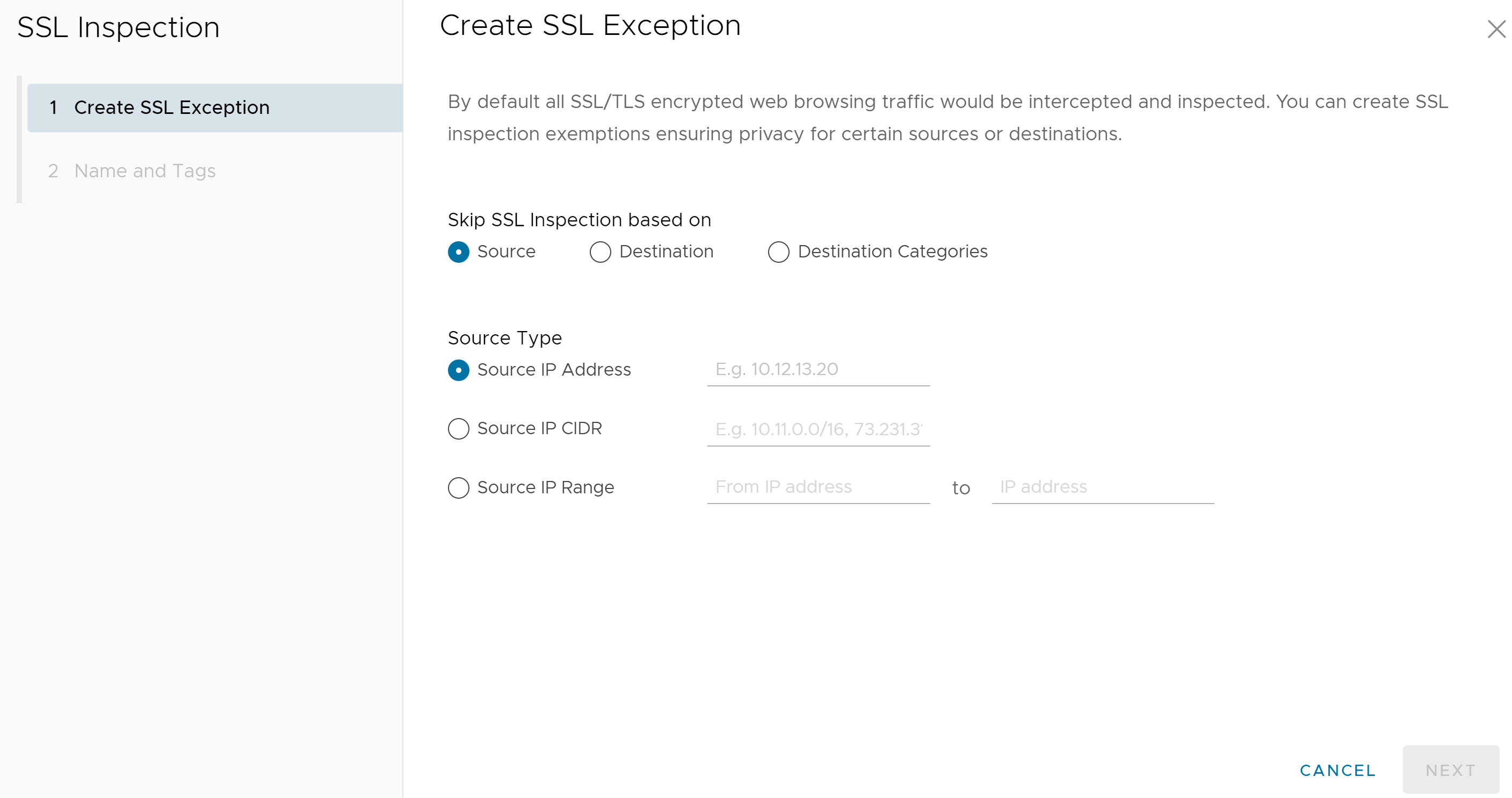
- In the Create SSL Exception screen, users can choose which type of traffic to bypass SSL Inspection by selecting either Source, Destination, or Destination Categories.
For example, users can create a rule that bypassed SSL inspection for all traffic destined for zoom.us, by configuring the rule as a destination rule and then choosing the destination type by either destination IP or host/domain as shown in the following sample screen.
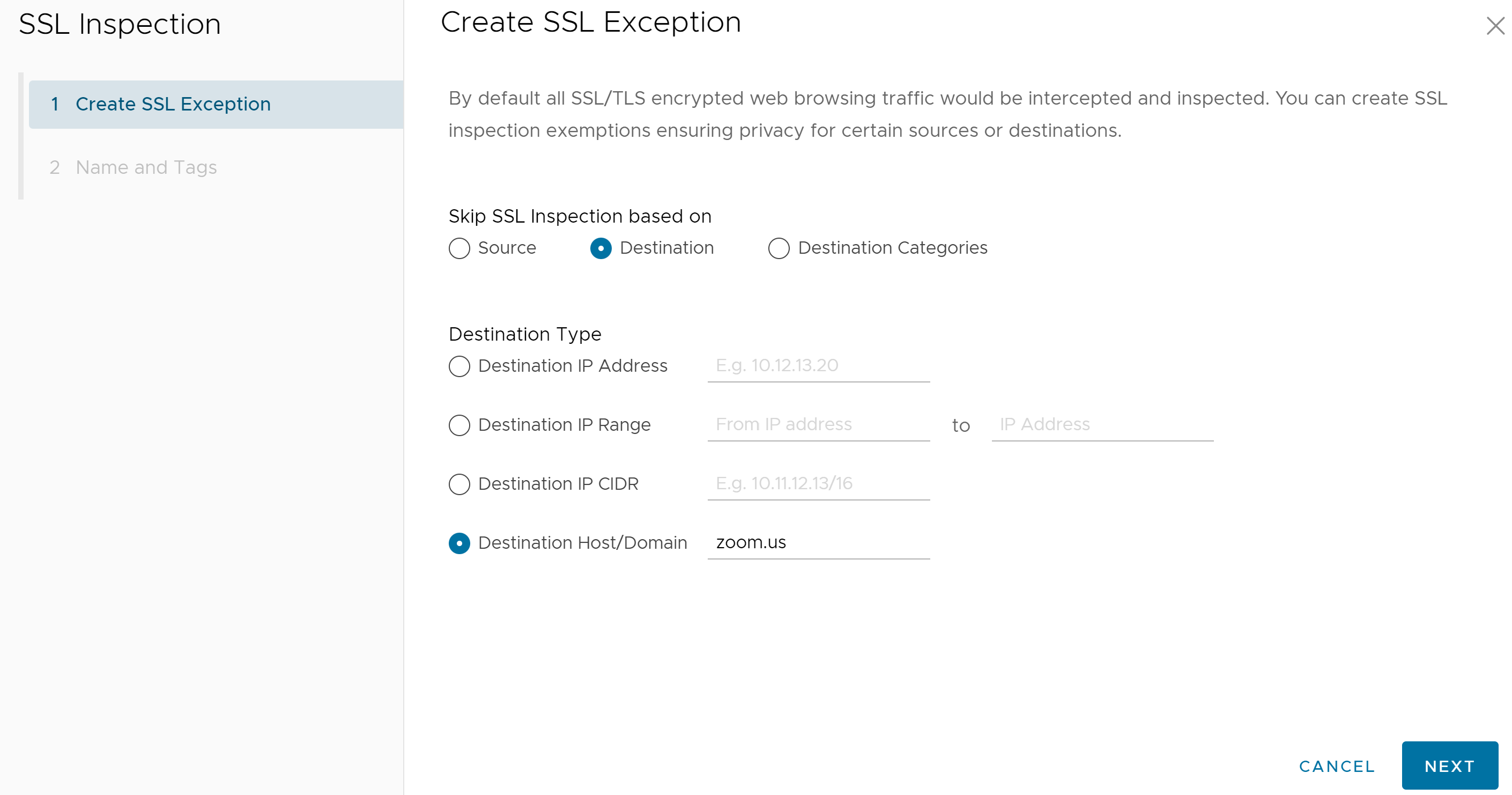
- Click the Next button.
- In the Name and Tags screen, provide the Rule Name, Tags, a Reason (if needed) for why the bypass rule was created, and a Position for the rule on the list of SSL Inspection rules (the options are either 'Top of List' or 'Bottom of List').
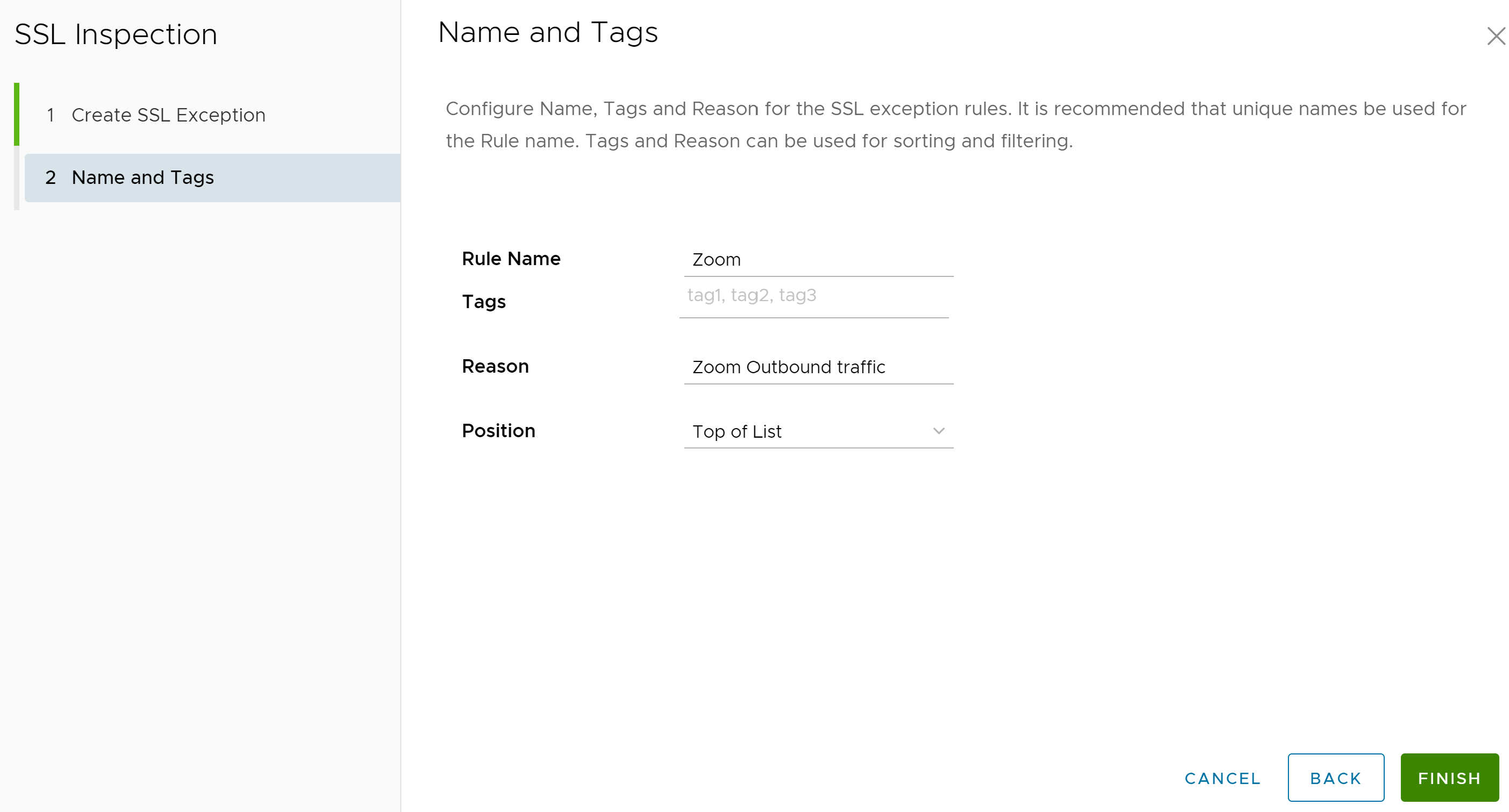
- Click Finish.
The SSL Inspection rule is now added to the Security Policy.
- Users have the following options: configure another SSL Inspection rule, configure a different Security Policy category, or if finished, click the Publish button to publish the Security Policy.
- After publishing the Security Policy, users can Apply the Security Policy.
Easy SSL Inspection Bypass/Quick Exceptions
The Easy SSL Bypass feature allows users to bypass SSL inspection for commonly used Web applications.
- On the SSL Inspection tab of the Security Policies screen, click ADD QUICK EXCEPTION.
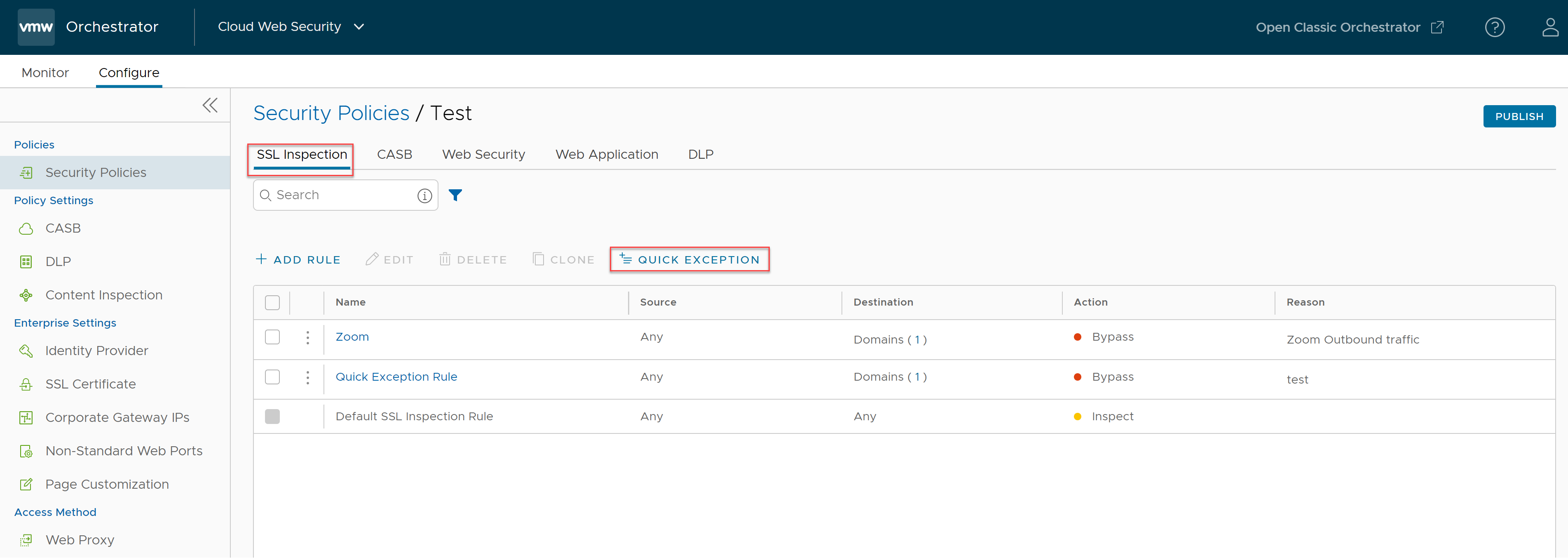
The Quick Exceptions configuration screen appears.
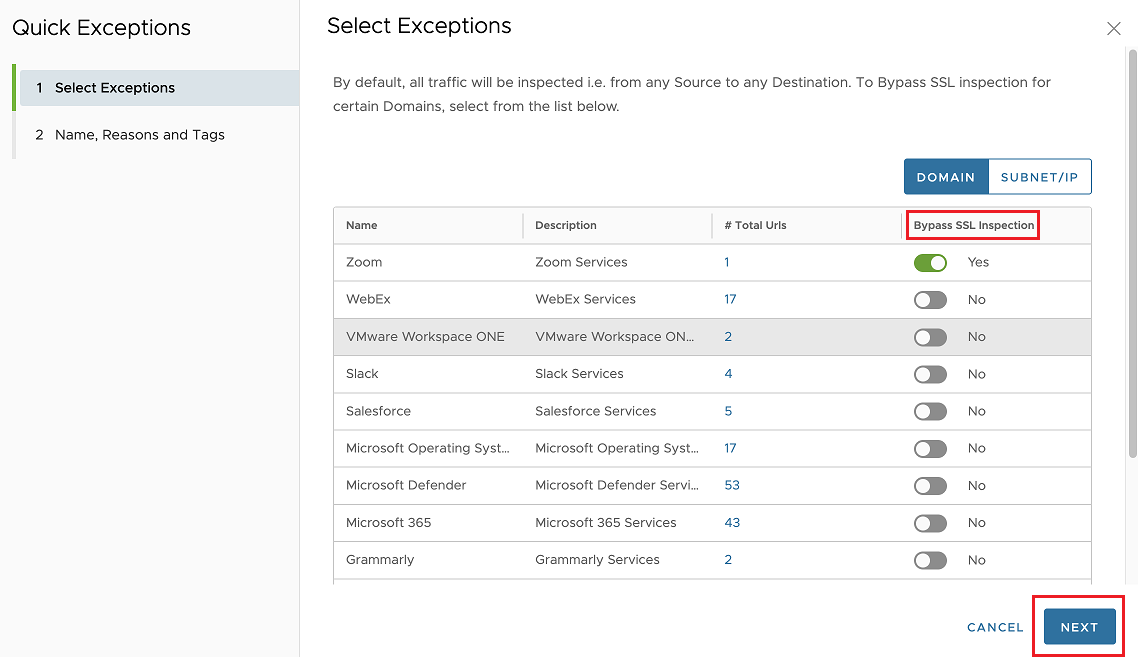
- To bypass SSL inspection for certain domains or subnet IP ranges, in the Select Exceptions page, select one or more applications that user want excepted from SSL inspection by turning on the toggle button, and click Next. When users select an application, all the URLs associated with the selected applications are also excluded from SSL inspection.
- In the Name, Reasons and Tags screen, provide Tags and a Reason (if needed) for why the quick exception rule was created and click Finish.
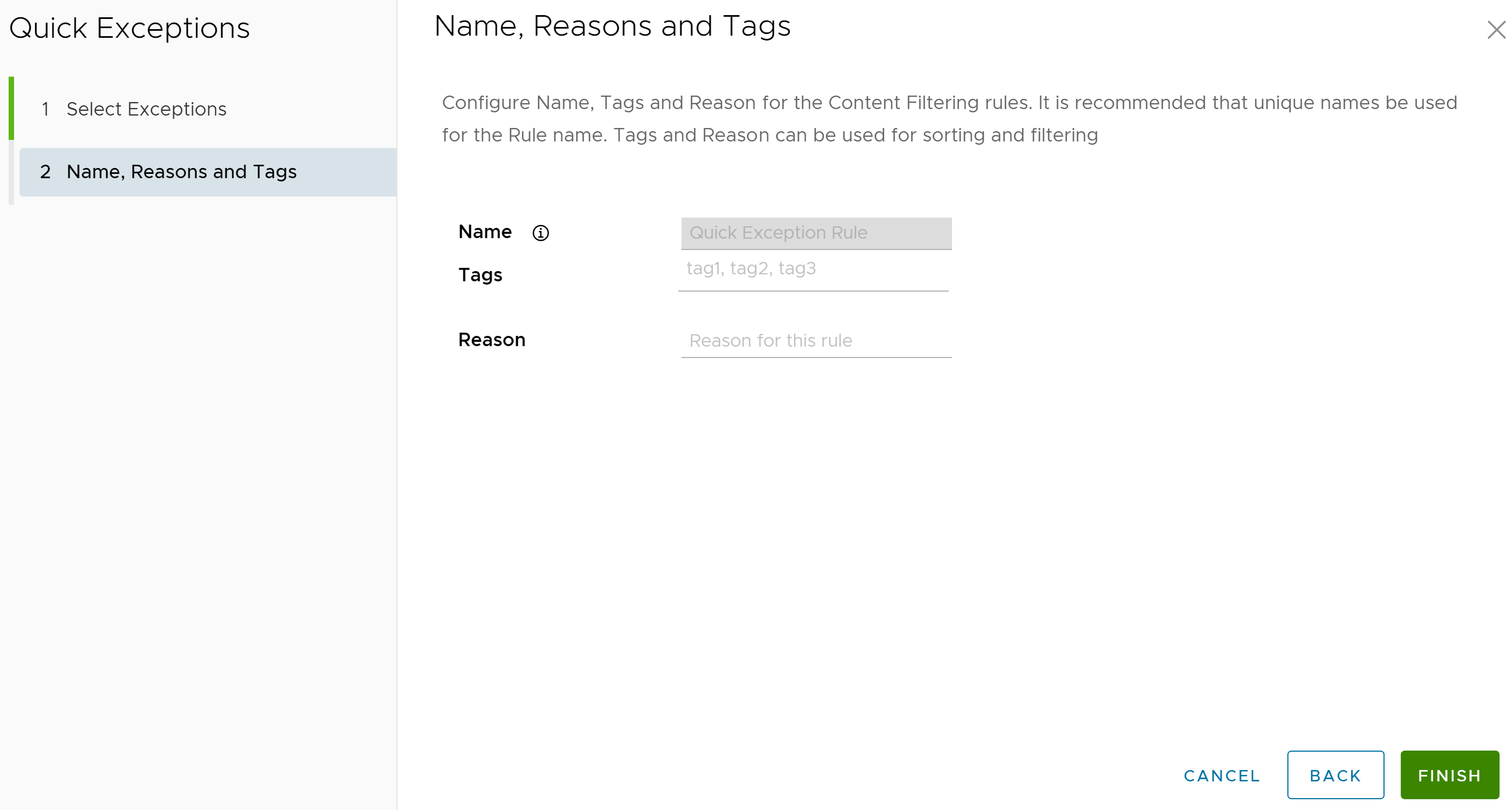
The Quick Exception Rule is created, and it appears in the SSL Inspection Rule listing page as shown in the following screenshot.
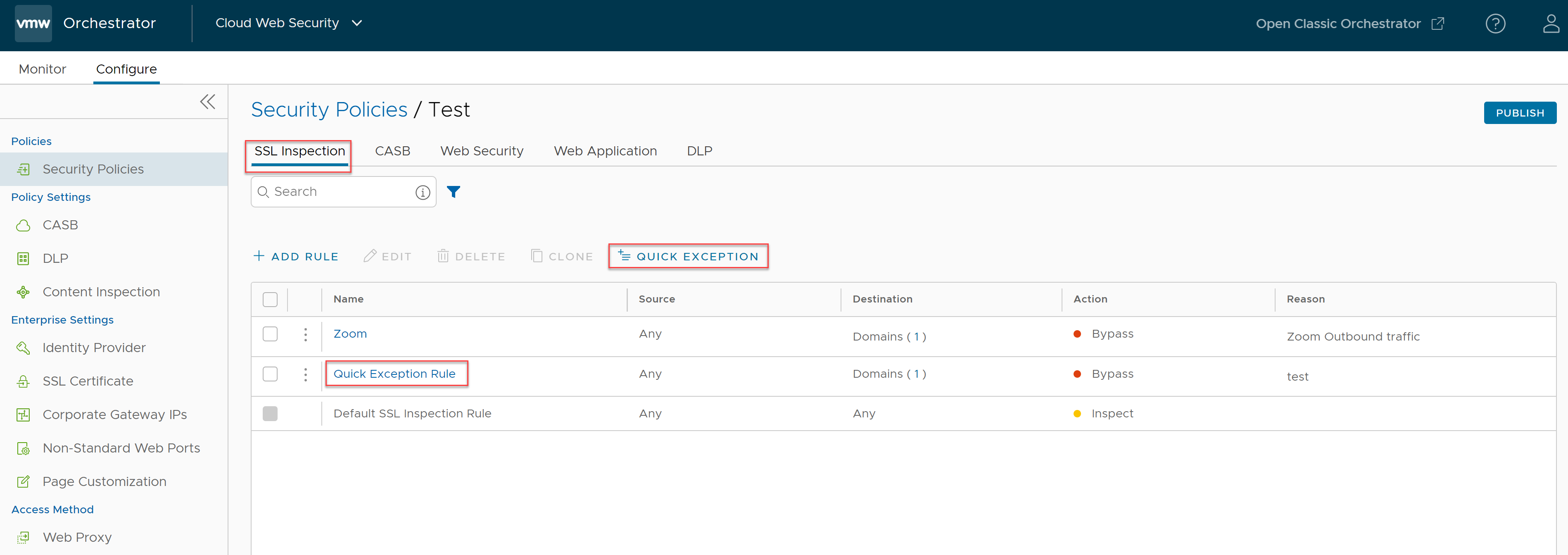 Note: Only one rule is created, and no additional rules can be created. This rule is always named as "Quick Exception Rule" and the name cannot be changed in the Quick Exception wizard.Note: The rule will always be the second to last rule in the SSL Inspection Rule listing page and can quickly be accessed by clicking the Quick Exception Rule name. After the Quick Exception Rule is added, the Add Quick Exceptions button name changes to Quick Exception, indicating there is an existing Quick Exception Rule that can be edited, and no additional rules of this type can be added.
Note: Only one rule is created, and no additional rules can be created. This rule is always named as "Quick Exception Rule" and the name cannot be changed in the Quick Exception wizard.Note: The rule will always be the second to last rule in the SSL Inspection Rule listing page and can quickly be accessed by clicking the Quick Exception Rule name. After the Quick Exception Rule is added, the Add Quick Exceptions button name changes to Quick Exception, indicating there is an existing Quick Exception Rule that can be edited, and no additional rules of this type can be added.