VMware Edge Network Intelligence supports Single Sign-On and Single Sign-off capabilities for organizations by providing SAML integration with third-party Identity Providers (IdPs). VMware Edge Network Intelligence supports integration with SaaS-based IdPs such as OneLogin and Azure AD, as well as integration with on-prem directories using SAML v2.0.
SSO Setup for Azure AD
If you are using Microsoft Azure AD as the Identity Provider for SSO, follow the instructions in the tutorial link below to set up SSO for accessing VMware Edge Network Intelligence. VMware Edge Network Intelligence is listed in the Azure Marketplace as one of the approved application vendors that supports Azure AD for SSO.
Tutorial: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-saas-voyance-tutorial
Setting up SSO using SAML
VMware Edge Network Intelligence supports SAML v2.0-based SSO that allows you to use your corporate identity to log in. Your company has a customized subdomain. For example, https://yourdomain.nyansa.com. If you cannot find your subdomain, visit http://app.nyansa.com and request a link to your company's login URL. You will receive an e-mail with your subdomain.
To set up SSO using SAML:
Login to the VMware Edge Network Intelligence application using your Admin credentials.
Go to My Account > Admin Settings > User access.
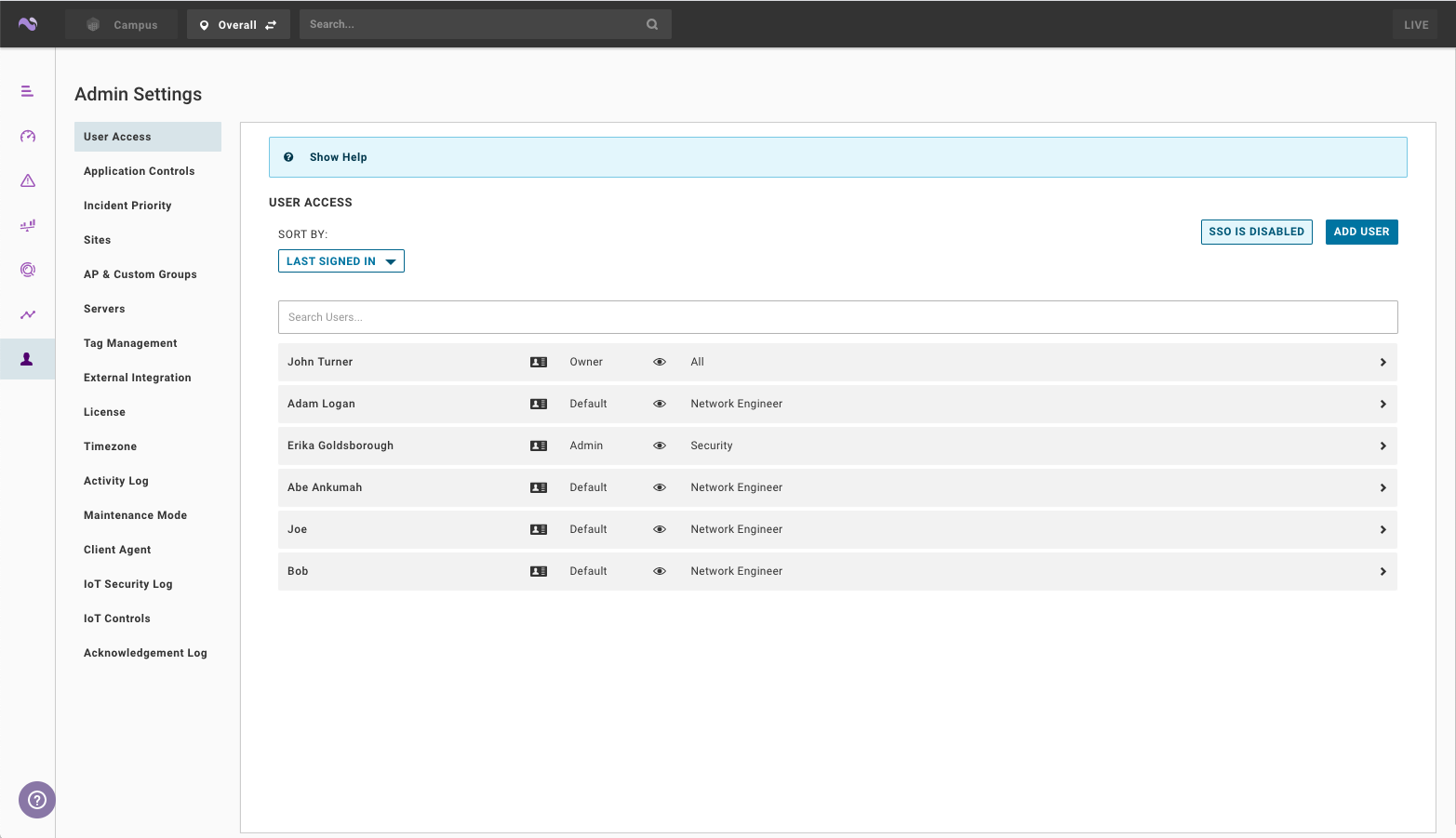
Click SSO is Disabled.
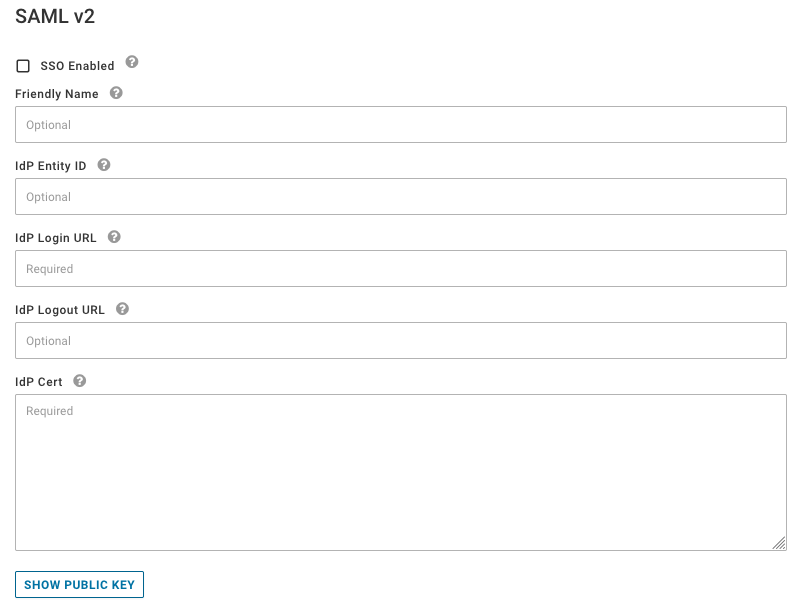
Configure the following parameters to setup your SAML connection:
Friendly Name (optional) - Customize your login experience. This text will appear on the login button as "Login via (friendly name)".
IdP Entity ID (optional) - The URL that describes an entity that is expected to receive the SAML message.
IdP Login URL (required) - Enter the SAML 2.0 Endpoint URL (HTTP) for your identity provider.
IdP Logout URL (optional) - Enter the logout URL for the IdP. If you do not specify one, you will not be logged out of the IdP when you logout of the application.
IdP Cert (required) - Copy the entire x.509 Certificate from your identity provider and paste it into the IdP Cert box.
Configure Role-based access with SSO. For information, see Role Management.
Click Save.
If your IdP needs access to the SP metadata, you can find it by logging into VMware Edge Network Intelligence using your customized domain name. For example, https://yourdomain.nyansa.com/saml/metadata.
Required SAML Parameters
First Name |
firstName, first_name, firstname, http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname |
Last Name |
lastName, last_name, lastname, http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname |
User Roles |
role, roles (see Role Management for additional information on passing roles) http://schemas.microsoft.com/ws/2008/06/identity/claims/role |
Allowed Sites |
site, sites (separate multiple sites with white space, case insensitive) |
Role Management
VMware Edge Network Intelligence supports flexible role assignment options for synchronizing roles between your SSO provider and VMware Edge Network Intelligence.
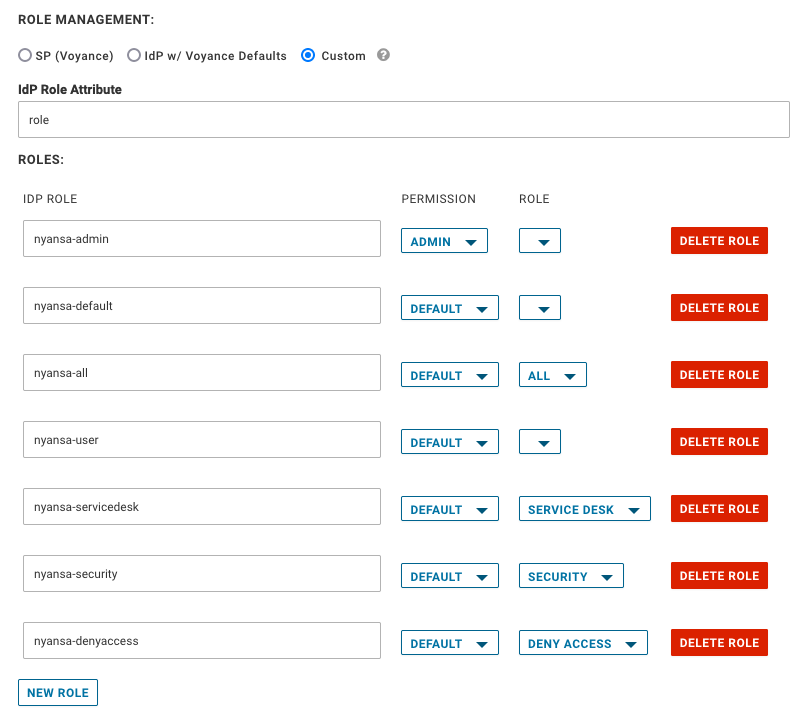
SP (Voyance) |
When this option is selected, VMware Edge Network Intelligence uses the roles that are currently assigned within the application for users logging in via SSO. This implies that any role information that is passed along with your SAML token is ignored and overwritten by the role defined with the VMware Edge Network Intelligence application. New users will automatically be assigned a "User" role. |
IdP w/ Voyance Defaults |
When this option is selected, VMware Edge Network Intelligence uses the roles that are passed with the SAML token. Roles are case sensitive and have to match one of the supported IdP roles:
|
Custom |
When this option is selected, you can pass custom strings for roles and map them to one of the VMware Edge Network Intelligence supported roles. You can also change the default role that is assigned to a user. |
Users with the role of "nyansa-denyaccess" will be denied access to VMware Edge Network Intelligence, even if your IdP authenticated the user.
For more information about Role-based access, see Role-Based Access and Site Restrictions for Users.
SSO Verification
Once you enter all of the required parameters to set up SSO using SAML and click the Save button. A pop-up appears asking you whether you want to test your connection to the IdP.
If you accept and continue, VMware Edge Network Intelligence will open a new tab with the IdP login URL. Make sure that you can authenticate with your IdP before activating SSO for all users. If you are unsure about any of the settings, deactivate SSO at the top of the page, so you can still login using your VMware Edge Network Intelligence credentials.
After you have finished setting up single sign-on for your team, each member will receive a notification email letting them know about the change. Your team members can login to VMware Edge Network Intelligence either by visiting the IdP's dashboard or going directly to http://yourdomain.nyansa.com, where they will see a login page.
If you have trouble setting up SAML connection to your directory, contact your VMware Edge Network Intelligence Support team. Once SSO is activated, you can no longer sign in or create users in the user admin section. To deactivate SSO, open a support ticket.