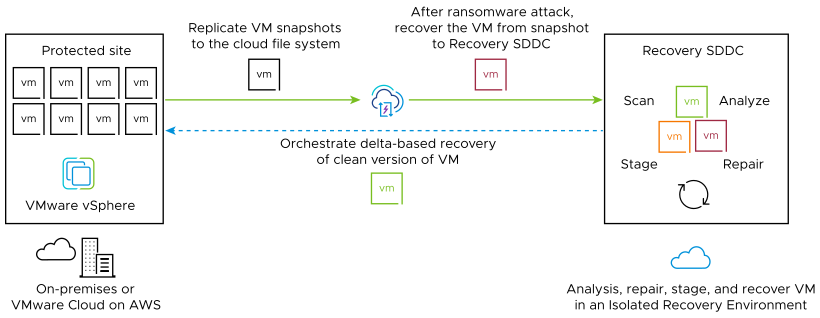
VMware Live Cyber Recovery ranswomare recovery provides an on-demand, cloud-based isolated recovery environment (IRE) with integrated security and behavior analysis tools that help you recover from a ransomware attack using snapshots.
VMware Live Cyber Recovery offers a hosted, on-demand IRE, or cyber recovery 'clean room', to provide a cost-effective solution that reduces your infrastructure costs.
Ransomware recovery comes with a dedicated workflow to guide you through the remediation process. VMware Live Cyber Recovery embeds next-generation anti-virus directly into the recovery workflow, so you can more easily find modern, fileless-based malware in VM recovery backups to prevent reinfection.
More specifically,
VMware Live Cyber Recovery provides these capabilities for
VMware Ransomware Recovery:
- On-demand, cloud-based (IRE) with predefined network isolation levels. The VMware Live Cyber Recovery recovery SDDC provides a network-restricted IRE on VMware Cloud on AWS as a cost effective solution which does not require building an environment from scratch and patching together different tools and hardware. After a ransomware attack, you can launch a recovery plan and select VMs from a deep snapshot history to be placed into an IRE for forensic analysis and validation. For more information, see Configuring the Ransomware Recovery Isolated Recovery Environment (IRE).
- Use the recovery SDDC ro recover and run cleansed production workloads. You can create separate VMware Cloud Gateways on the recovery SDDC for recovering and running production VMs. For those cases where the original protected site is unavailable, creating a separate gateway on the recovery SDDC allows you to perform ransomware recovery and cleanse infected VMs, and then recover clean VMs to a production network environment on the same recovery SDDC. These production VMs can be failed back to a protected site once it becomes available.
- Deep integrated security and vulnerability analysis. VMware Ransomware Recovery provides access to continuous cloud scanning systems that analyze each VM in recovery for suspicious OS behaviors, malware file signatures, and known vulnerabilities.
- Recovery orchestration. You can configure recovery plans to automatically move protected VMs to the recovery SDDC for analysis and validation. When you have succeeded in finding clean VMs, you can orchestrate those VMs back to a protected production site.