When you start a recovery plan for ransomware and begin validating VMs on the recovery SDDC, the system analyzes and scans VMs for vulnerabilities, malware signatures, and behavioral anomalies.
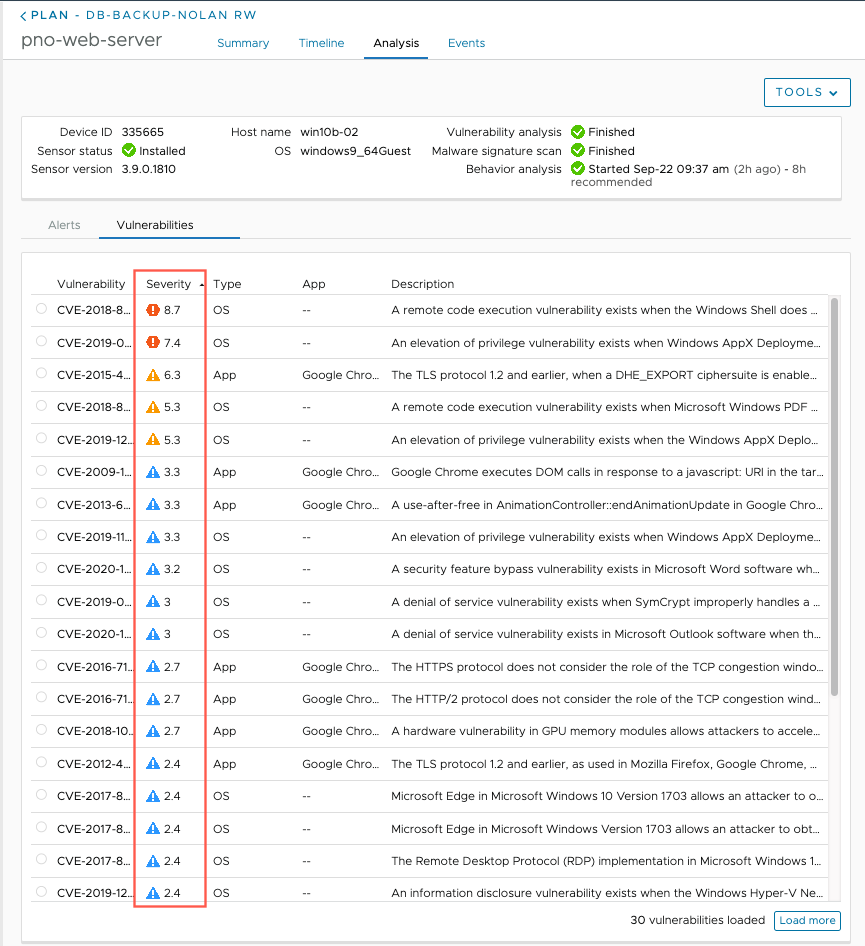
- Vulnerability analysis. Searches for and displays OS and application vulnerabilities discovered on VMs. Results are displayed on the Vulnerabilities tab in a VM validation page:
- Behavior analysis. Continuous analysis of running software and processes on the guest OS, looking for suspicious behavior. Results are displayed on the tab.
- Malware signature scan. Scans VMs for known malware and viruses. Results are displayed on the tab.
Note: Currently, malware signature scans for Linux VMs do not report progress in the UI. The scan still occurs, but the progress indicator remains "in progress" even after the scan is finished.
Vulnerability Analysis
VMware Live Cyber Recovery scans VMs guest OS's for known vulnerabilities (security flaws which can be exploited) to be patched, to close potential vectors of attack and prevent reinfection. You can view the full context of a vulnerability discovered on VMs, including risk score details and how it impacts your environment, so you can fix the issue.
All vulnerabilities found during a scan receive a Risk Score, between 0.0 (no risk) and 10.0 (maximum risk), which accurately represents the risk of a given vulnerability on VMs in your environment. The analysis is performed by combining Common Vulnerability Scoring System (CVSS) information with proprietary threat data and advanced modeling from Kenna Security.
The vulnerability risk score range and severity are defined as follows.
| Score Range | Severity |
|---|---|
| 0.0 - 3.9 |
Low |
| 4.0 - 6.9 |
Moderate |
| 7.0 - 8.9 |
Important |
| 9.0 - 10.0 |
Critical |
The Vulnerability tab shows a list of all found vulnerabilities with their CVE number and a link to the vulnerability article in the National Institute of Standards and Technology (NIST) database. Each vulnerability is identified by its Common Vulnerabilities and Exposure (CVE) name, which consists of the string CVE plus the four digit year and then a number, such as CVE-2022-1234.
You can also view the vulnerability details in the security console (Carbon Black CloudCarbon Black Cloud console), if you have integrated analysis activated. When you select a vulnerability in the list, details of the vulnerability are displayed.
Alerts for Malware Scan and Behavior Analysis
When VMs are started on the recovery SDDC, the system analyzes VMs and their guest files for anomalous behaviors, such as running software that has a bad reputation, running processes that repeatedly make outbound connections, reaching out to known suspicious IP addresses, malicious interference with the Windows Registry, or other system files or processes on VMs.
The system also scans VM guest files for malware and viruses, calculating hashes of binaries, parsing binary components, looking for attributes known as a malware 'signature' so you can remove them.
The results of the malware scan and behavior analysis displayed in the Alerts tab and ranked according to severity, with a higher score being worse than a lower score:
| Score Range | Severity |
|---|---|
| 1 - 2 |
Activities such as port scans, malware drops (installation of malware), changes to system configuration files, persistence of malware, and more. |
| 3 - 5 |
Activities such as running malware, generic virus-like behavior, monitoring user input, potential memory scraping, password theft, and more. |
| 6 - 10 |
Activities such as reverse command shells, process hollowing, destructive malware, hidden processes and toolsets, applications talking on the network that should not be, and more. |
If you find vulnerabilities or malware, or observe suspicious behavior, you can use some of the tools provided on the VM ransomware page, such as copying the IP address of a VM, open the VM in vCenter, or perform guest file recovery:
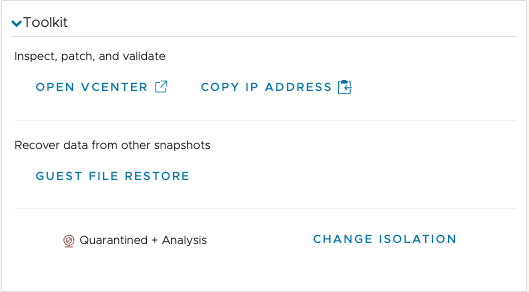
You can also view VMs in the Carbon Black Cloud console for further analysis and remediation, from the Tools drop-down menu when you select the tab. The, from the Tools menu, select Open in security console.