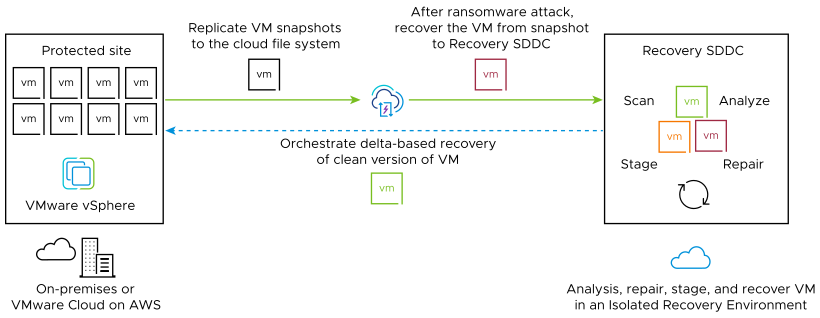
VMware Ransomware Recovery provides an isolated recovery environment (IRE) on a VMware Cloud recovery SDDC that allows you to inspect, analyze, and recover infected VMs before restoring them to a production environment.
Because VM snapshots are likely to be infected after a ransomware attack, you can use the recovery SDDC as a network-restricted IRE to perform analysis, remediation, and validation of compromised VMs without the risk of infecting other workloads in production. Once you validate clean VMs, you can recover them back to production.
You can also
create separate VMware Cloud Gateways to use the
recovery SDDC for
recovering and running production VMs. Creating separate gateways on the
recovery SDDC allows you to perform ransomware recovery to cleanse infected VMs, and then recover clean VMs to a production network environment in
VMware Cloud in cases where the original protected site is unavailable. These production VMs can be failed back to a protected site once it becomes available.
Note: For more detailed information about setting up the IRE, see
Configuring the Ransomware Recovery Isolated Recovery Environment (IRE).
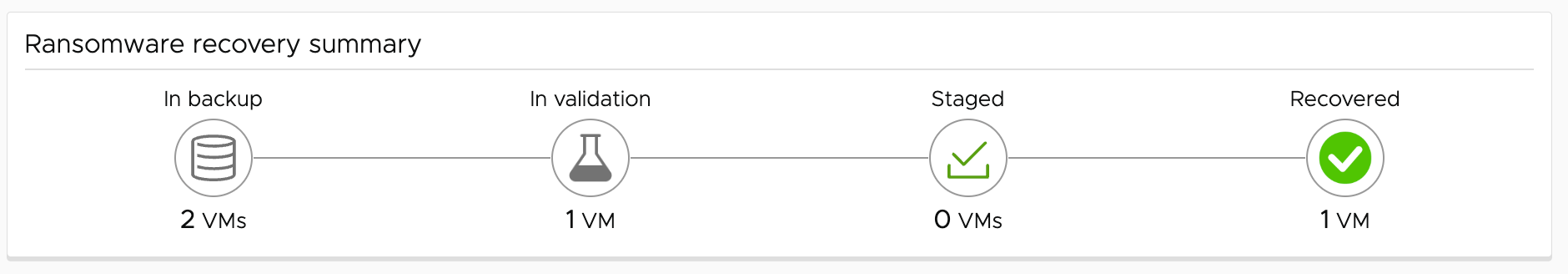
The journey of VMs in a recovery plan for ransomware recovery go through these four states: backup, validation, staged, and recovered.
Note: Uninstall any existing third party security software on VMs before running them in a
recovery plan for ransomware, including any pre-existing
Carbon Black security sensors.
Ransomware recovery states are defined as follows:
- In the In backup state, VMs have been replicated to a cloud file system and are available in a running recovery plan for validation on the recovery SDDC. You can choose to recover VMs based on the snapshot history of the protection groups to which the VM belongs.
- In the In validation state, VMs are moved to a recovery SDDC and powered on. Security sensors are installed on VMs so vulnerability and behavioral analysis and malware signature scanning can begin. You can patch VMs in the validation stage to address discovered vulnerabilities. You can also remove malware using security tools when VMs are in this stage. (You can also start VMs on the recovery SDDC with no sensors installed, if you want to use your own security software for analysis.)
- In the Staged state, you can start recovering VMs. VMs in this state have been validated and powered off. Staged VMs can be recovered to a protected site, to a different gateway on the recovery SDDC (for running production workloads), or returned to validation to find a better recovery candidate.
- In the Recovered state, VMs have been recovered to the original protected site, or a different protected site.