Horizon Cloud on Microsoft Azure simplifies the delivery of virtual desktops and apps. With a single solution, organizations can easily deploy and manage virtual applications and desktops on Microsoft Azure while leveraging cloud resources. IT can save time getting up and running with an easy deployment process, simplified management, and an architecture built for the cloud.
The Horizon Cloud on Azure is offered in a Bring-your-own subscription model. In this,
-
VMware manages the Horizon Cloud deployment on Azure, including provisioning and lifecycle management of all components.
-
The provisioning is done in a customer-owned, but VMware-managed Azure Subscription.
For more information on the Horizon Cloud, see Horizon Cloud - A Cloud-Native Virtual Desktop Platform.
NSX Advanced Load Balancer on Microsoft Azure
NSX Advanced Load Balancer provides an enterprise grade, full featured load balancing, WAF with 100% REST API automation, and analytics that can be deployed in Microsoft Azure.
For more information, see Installing NSX Advanced Load Balancer in Microsoft Azure topic in the VMware NSX Advanced Load Balancer Installation Guide.
NSX Advanced Load Balancer for Horizon Cloud on Azure
NSX Advanced Load Balancer can be used to provide application delivery features (load balancing, WAF, and GSLB) for Horizon Cloud on Azure deployments.
The key benefits of using NSX Advanced Load Balancer are:
-
Consistent application delivery policies in multi-cloud Horizon deployments, spanning on-premises and public cloud pods.
-
Ability to leverage NSX Advanced Load Balancer analytics capabilities such as metrics and per-request logs for better visibility and troubleshooting.
-
Elastic scale-out of load balancing capacity when required.
Reference Design
Currently, NSX Advanced Load Balancer is provided as a customer-managed installation for Horizon Cloud on Azure.
In this scenario,
-
VMware manages the Horizon Cloud deployment on Azure, including provisioning and lifecycle management of all components.
-
The provisioning is done in a customer-owned, but VMware-managed Azure Subscription.
In addition,
-
NSX Advanced Load Balancer is deployed by the customer in the same subscription, sharing the Azure Virtual Network (VNet) with the Horizon Cloud objects.
-
While provisioning the cloud pod, some configurations have to be included/ modified, as detailed in the guide below.
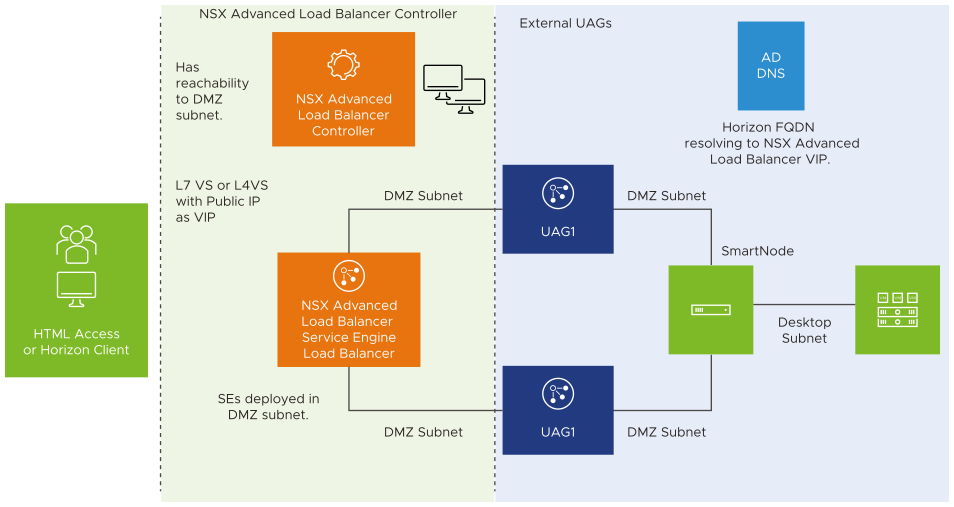
Provisioning the Horizon Pod with NSX Advanced Load Balancer
For a new deployment, follow the steps below to provision a Horizon Pod with NSX Advanced Load Balancer:
-
Deploy the NSX Advanced Load Balancer Controller and configure an Azure Cloud in the Controller
-
Create the Horizon Cloud Pod
-
Modify Network Security Group for External UAGs on Azure
-
Configure the virtual service on the NSX Advanced Load Balancer Controller
Deploying and Configuring the NSX Advanced Load Balancer Controller on Azure
Follow the steps given in Installing NSX Advanced Load Balancer in Microsoft Azure topic in the VMware NSX Advanced Load Balancer Installation Guide to install and configure an NSX Advanced Load Balancer Controller Cluster.
Installing the NSX Advanced Load Balancer Controller
For detailed steps on installing an NSX Advanced Load Balancer Controller, see Installing NSX Advanced Load Balancer in Microsoft Azure topic in the VMware NSX Advanced Load Balancer Installation Guide.
-
The NSX Advanced Load Balancer Controller is a control-plane entity. Operators can connect to the Controller for configuration, operations, and analytics.
-
The Controller can be instantiated in a separate resource group within the subscription, and provided an IP address from the same VNet as being used for Horizon Cloud.
-
The NSX Advanced Load Balancer Controller can alternately be installed on-premises, or in another Subscription / VNet. In such cases, the Controller must have IP connectivity to the Azure end-points and peering to the Horizon Cloud Pod VNet.
Configuring the Azure Cloud
For details on initializing the Controller, and configuring an Azure Cloud within the Controller so that it can provision NSX Advanced Load Balancer Service Engines, see Installing NSX Advanced Load Balancer in Microsoft Azure topic in the VMware NSX Advanced Load Balancer Installation Guide.
-
It is recommended that a separate Resource Group be used for the Azure Cloud connector being configured.
-
The VNet must be the same as being used for Horizon Cloud.
-
Dedicated management network must be enabled. This ensures that a separate NIC is used for Controller - to - Service Engine communication.
The following Azure-related steps must be performed before creating the NSX Advanced Load Balancer virtual service.
Deploying the Horizon Cloud Pod
The Horizon Cloud pod can be provisioned from the Horizon Application Home Page.
For steps to deploy the Horizon Cloud pod, see VMware Horizon Cloud Service Documentation.
By default, the Horizon Cloud on Azure provisions a fresh public IP from the Azure IP address space for load balancing external UAGs. This IP is configured on an Azure Load Balancer which is provisioned as part of the standard pod deployment. This IP is also configured on the UAGs as the PCoIP URL.
To use NSX Advanced Load Balancer instead, deactivate the automatic allocation during pod deployment, and instead provide a public IP (which will be hosted on the NSX Advanced Load Balancer virtual service).
In the external UAG configuration setting,
-
Deactivate the option Enable Public IP.
-
Enter any unused IP.
Note:Replace this IP with the actual virtual service IP from the NSX Advanced Load Balancer virtual service once the virtual service has been created.
Modifying Network Security Group for External UAGs
Modify the Azure Network Security Group associated with the external UAGs. The Horizon Cloud configures Azure Network Security Groups (NSG) to restrict access to the UAGs. The default NSG for external UAGs allows traffic from control and data ports, originating from the internet.Modify the NSG to allow incoming traffic on the same ports, but originating in the DMZ subnet.
Creating Virtual Services on NSX Advanced Load Balancer
There are two options to deploy NSX Advanced Load Balancer for UAG load balancing in Azure.
-
Single VIP with two virtual services
-
Single L4 virtual service
For more information on these design options, see Reference Architecture for Horizon.
Single VIP with Two Virtual Services
To configure single VIP with two virtual services, follow the steps given below:
-
Create an IP group with UAG as members
-
Create custom Health Monitor for UAG
-
Create pools
-
Create SSL profile and install SSL certificate
-
Create an L7 virtual service
-
Create an L4 virtual service using the L7 virtual service as shared VIP and specify all the ports required for secondary protocols
The steps are explained in detail in the following sections.
Creating an IP Group
IP groups are comma-separated lists of IP addresses that may be referenced by profiles, policies, and logs. Since the same UAG servers are used as pool members in two different pools, IP groups can be attached to the pool instead of directly attaching servers to the pool. Any configuration change to the pool members like addition or removal of servers needs to be done at the IP Group level.
To create an IP group,
-
From the NSX Advanced Load Balancer UI, navigate to .
-
Click Create IP Group.
-
In the New IP Group screen, enter the IP Group Name.
-
Click the option Select by IP Address.
-
Enter the IP addresses of the UAG servers to which traffic is load balanced.
-
Click Save.
The IP addresses of the UAG will be available on the Azure portal once the UAGs are deployed.
Creating Custom Health Monitor for Horizon
To create a custom health monitor,
-
From the NSX Advanced Load Balancer UI, navigate to .
-
Click Create.
-
Select the Azure cloud that was created for Horizon.
-
Enter the following details in the New Health Monitor screen.
-
Field
Value
Send Interval
30
Receive Timeout
10
Client Requested Data
GET /favicon.ico HTTP/1.0Response Code
2xx
-
-
Click Save.
Creating SSL Profile for UAG Pool
Create an SSL Profile for the UAG pool with the configuration given below:
-
Navigate to .
-
Select Application Profile.
-
Enter the details as shown below:
-
Accepted Versions: 1.2
-
Click Ciphers tab and select the following from the cipher list:
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
-
-
Click Save.
Creating Pools
Pools maintain the list of servers assigned to them and perform health monitoring, load balancing, persistence, and functions that involve NSX Advanced Load Balancer-to-server interaction.
A pool includes the IP address of the UAG servers that is, UAG server01 and UAG server02.Create two pools:
-
For L7 (HTTPS) that is, Horizon-L7-pool
-
For secondary protocols named as Horizon-L4-pool
These two pools are required to attach to the two virtual services which will be created.
Consistent hash, with source IP address as the key, must be configured as the hash algorithm to maintain source IP affinity.
To create the pool,
-
Navigate to .
-
Select the Azure cloud created from the Select Cloud sub-screen.
-
Click Next.
-
Click Create Pool.
-
In the New Pool: screen, under Step 1: Settings, select the Load Balance algorithm as Consistent Hash with the Source IP Address as the hash key.
-
To bind the monitor, click Add Active Monitor and select the Custom Health monitor that was created.
-
Click Next.
-
Click Enable SSL and select the appropriate SSL profile.
-
Click Next.
-
In the Step 2: Servers tab, under Select Servers click the option IP Group.
-
Select the IP Group of the UAG servers created earlier.
-
Click Next.
-
Navigate to .
-
Click Next and Save.
Creating the Horizon L4 Pool
Follow the same steps as creating the Horizon L7 pool and create another pool with the name Horizon-l4-pool.
Configure the default server port to 443 and the load balancing algorithm as Consistent Hash with Source IP Address.
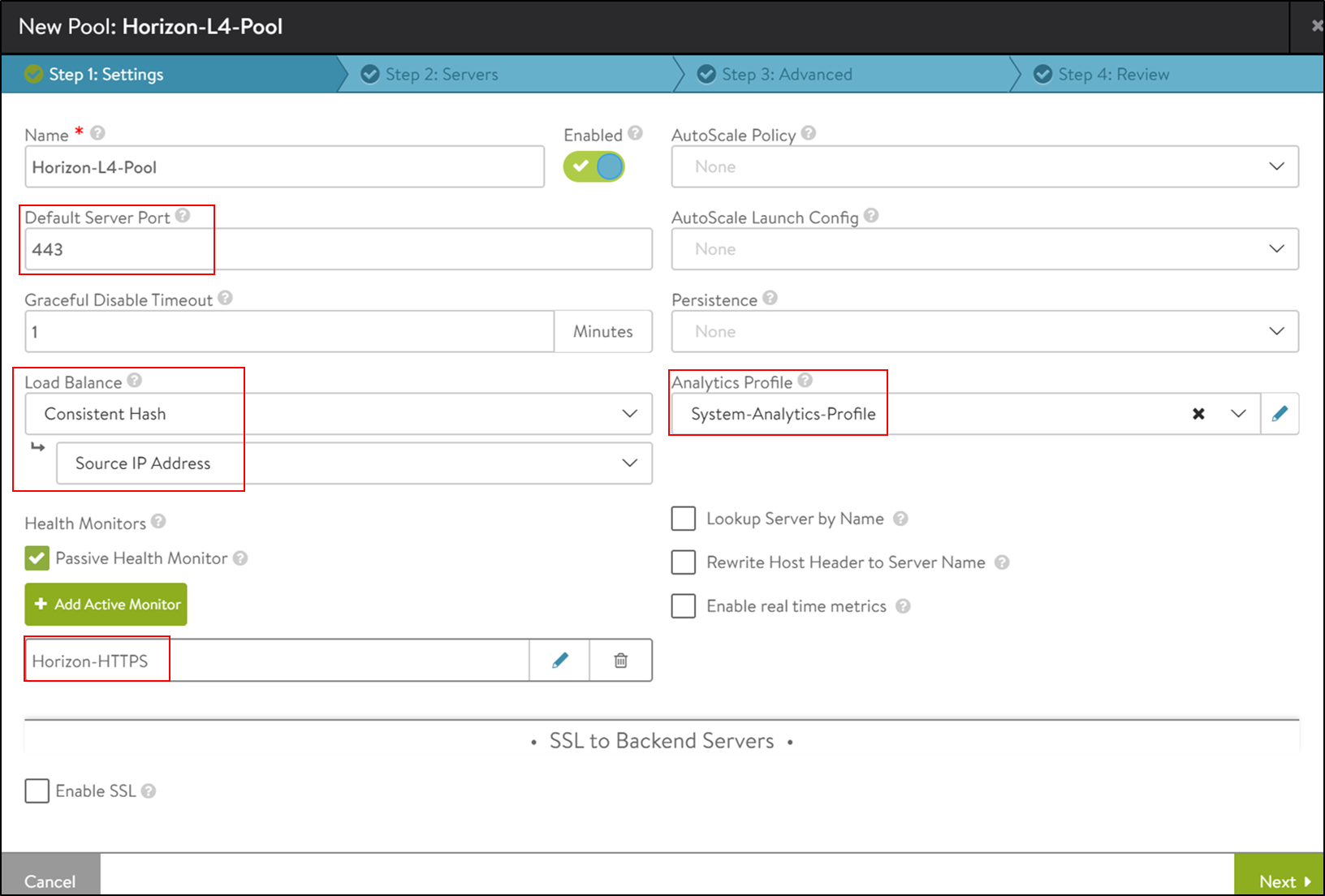
Under the Step 2: Servers tab, add the IP Group of the UAG servers created earlier.
Under the Step 3: Advanced tab, select Disable Port Translation to ensure that the destination port of the traffic does not change to the default server port set in the first pane(443).
Installing the SSL Certificate Required for L7 VIP
The SSL connection is being terminated at NSX Advanced Load Balancer virtual service. Therefore, the SSL certificate must be assigned to the virtual service. It is advised to install a certificate which is signed by a valid certificate authority instead of using self-signed certificates.
Install the certificate in NSX Advanced Load Balancer, and ensure the CA certificate is imported and linked. For instructions, see SSL Certificates topic in the VMware NSX Advanced Load Balancer Installation Guide.
For this set up, a certificate named Horizon_Certificate has been installed.
Creating a New SE Group
Create a new SE group for load balancing the External UAGs.
-
Go to and select the Azure cloud that was created.
-
Click Create Service Engine Group.
-
Under the Basic Settings tab, configure the following:
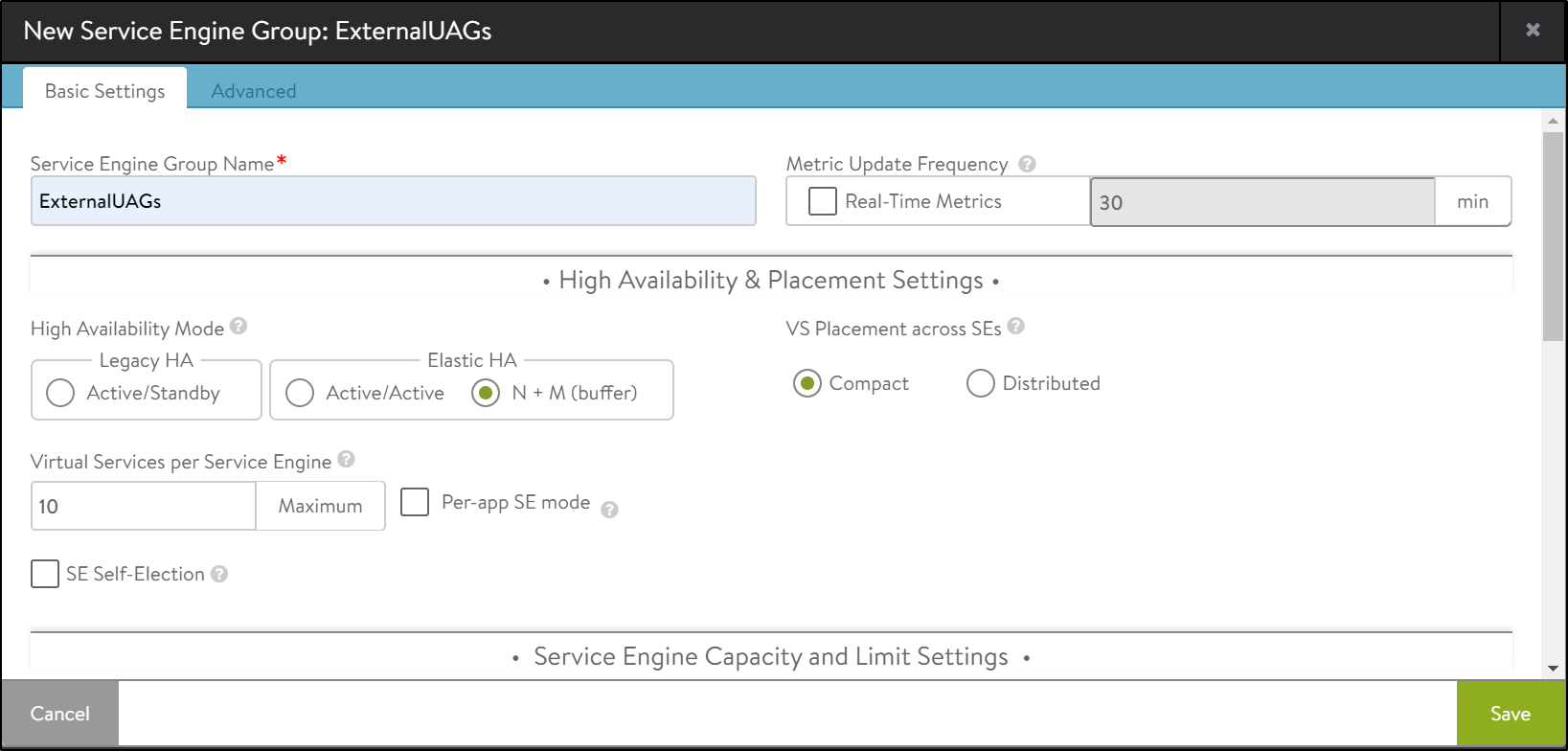
-
Click Advanced tab.
-
Under Override Data Network, select the data subnet that the external UAGs reside in.
-
Click Save.
Enabling Azure Standard ALB
To configure a Service Engine group with the standard ALB flag override,
[admin:10-52-0-71]: > configure serviceenginegroup ExternalUAGs [admin:10-52-0-71]: serviceenginegroup> use_standard_alb [admin:10-52-0-71]: serviceenginegroup> save
Creating SSL Profile for Virtual Service
Create an SSL Profile for the virtual service with the configuration given below:
-
Navigate to .
-
Select Application Profile.
-
Enter the following details:
-
Accepted Versions: TLS 1.1, 1.2
-
Click Ciphers tab and select the following from the cipher list:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
-
-
Click Save.
Creating L7 Virtual Service
To create the new L7 virtual service,
-
From the NSX Advanced Load Balancer UI, navigate to .
-
Click .
-
Use the System-Secure-HTTP-VDI as the Application Profile.
-
Configure the virtual service as shown below:
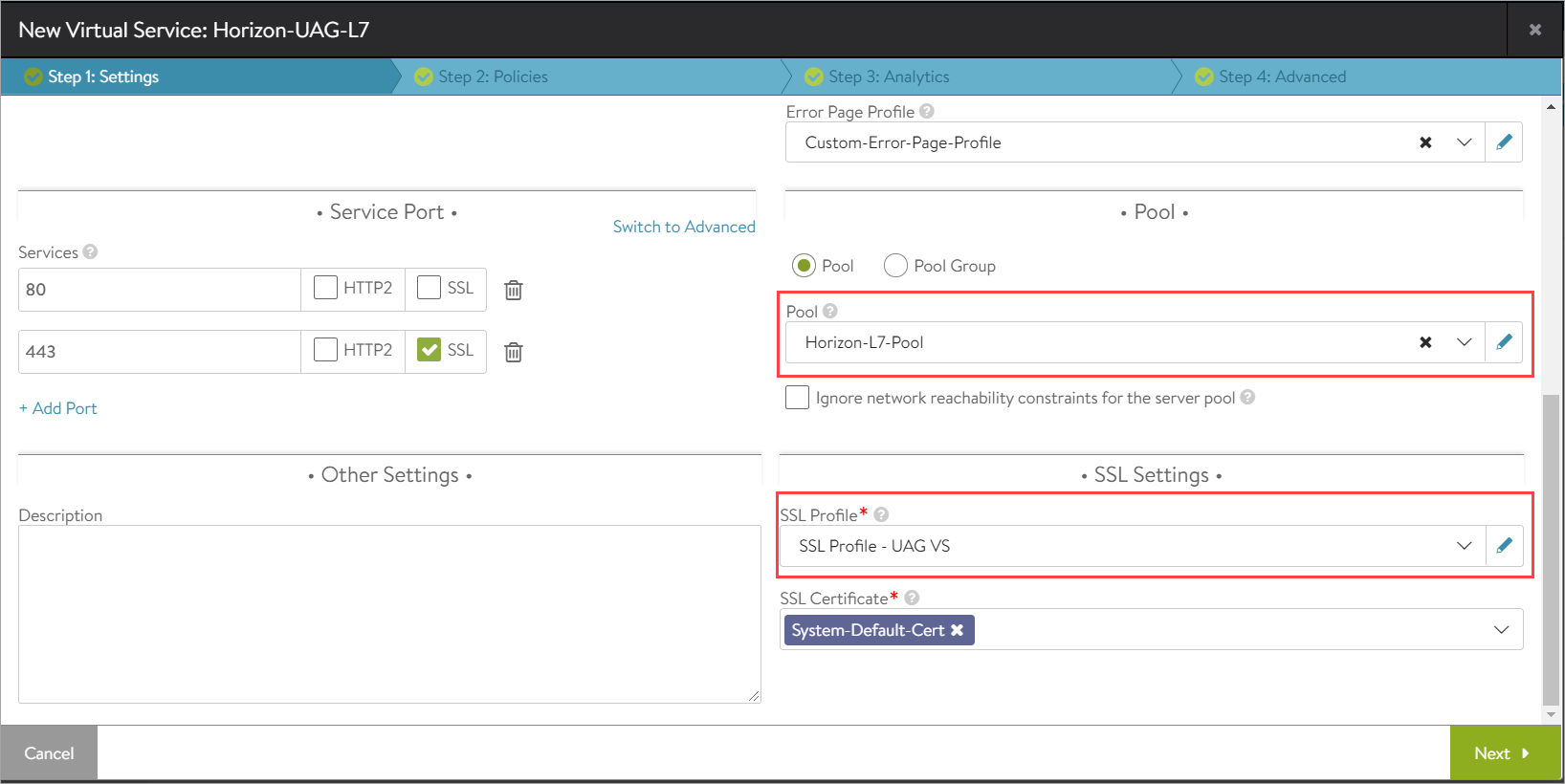
-
Click Next.
-
Navigate to the Advanced tab.
-
Select External UAGs as the SE Group.
-
Click Next and Save.
Creating L4 Virtual Service
Create another virtual service which will share the same IP address as that of the L7 VIP. This will make sure that we need only one virtual IP address for both the primary and secondary protocols. L7 virtual service will handle the primary protocol and the tunnel whereas L4 virtual service will handle other secondary protocols.
To create an L4 virtual service,
-
Click .
-
In the New Virtual Service screen, click Switch to Advanced under VIP Address.
-
Select the L7 virtual service that was created as the Virtual Service for VIP Sharing.
-
Under , click Switch to Advanced.
-
Add the following port numbers for the secondary protocols as shown below:
-
443 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile
-
Add 8443 for Blast
-
Add 8443 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile
-
Add 4172 for PCoIP
-
Add 4172 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile
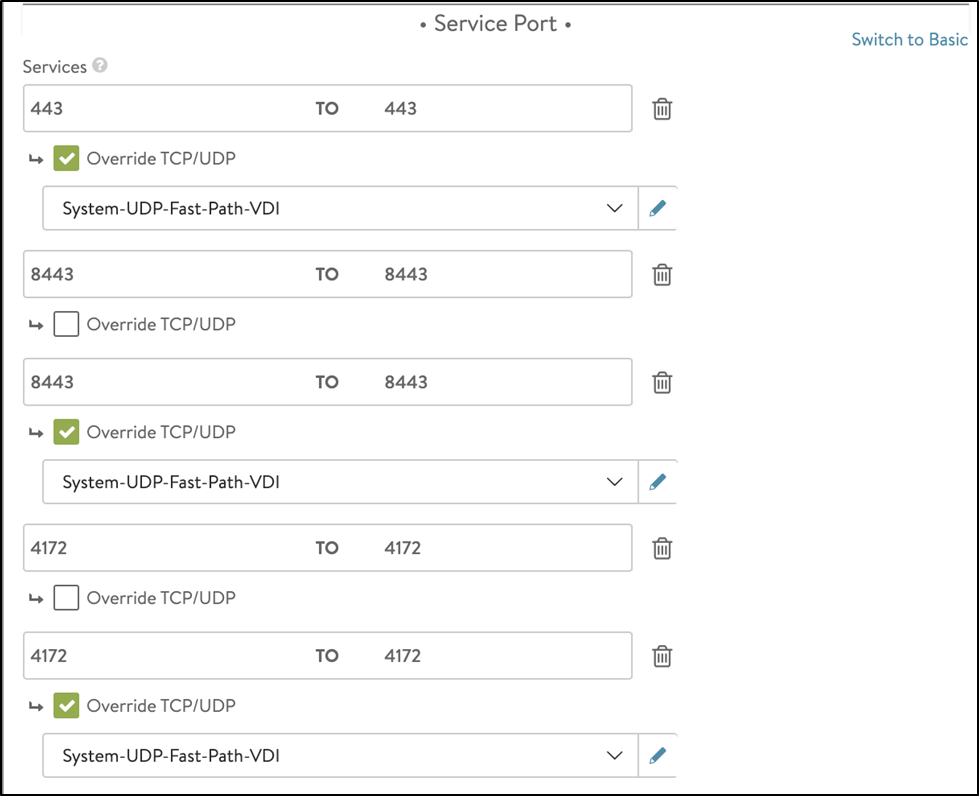
-
-
Select the Pool as Horizon-L4-Pool.
-
Click Next and navigate to the Step 4: Advanced tab.
-
Select External UAGs as the SE Group.
-
Click Save.
Load Balancing Internal UAGs with NSX Advanced Load Balancer
If internal UAGs have been deployed in the pod, another set of NSX Advanced Load Balancer virtual services must be used to load balance these UAGs. To isolate the NSX Advanced Load Balancer Service Engines for internal UAGs from the external UAGs, a separate Service Engine Group must be created and used for the internal UAG virtual services.
In addition, as the internal UAGs have their front-end IPs residing in the data subnet (instead of the DMZ subnet as was the case with external UAGs, the SE Group properties must be modified to reflect this).
Create a new SE group for Internal UAGs as shown below:
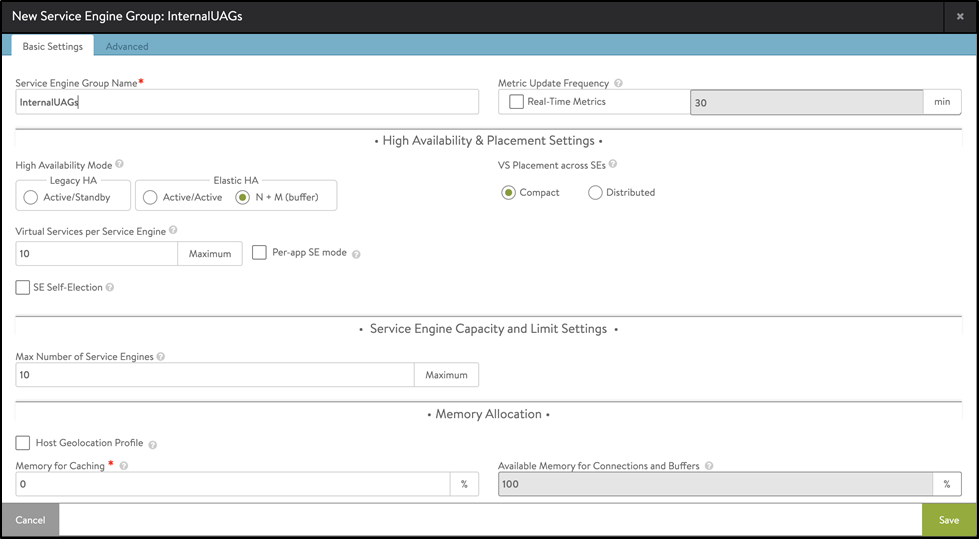
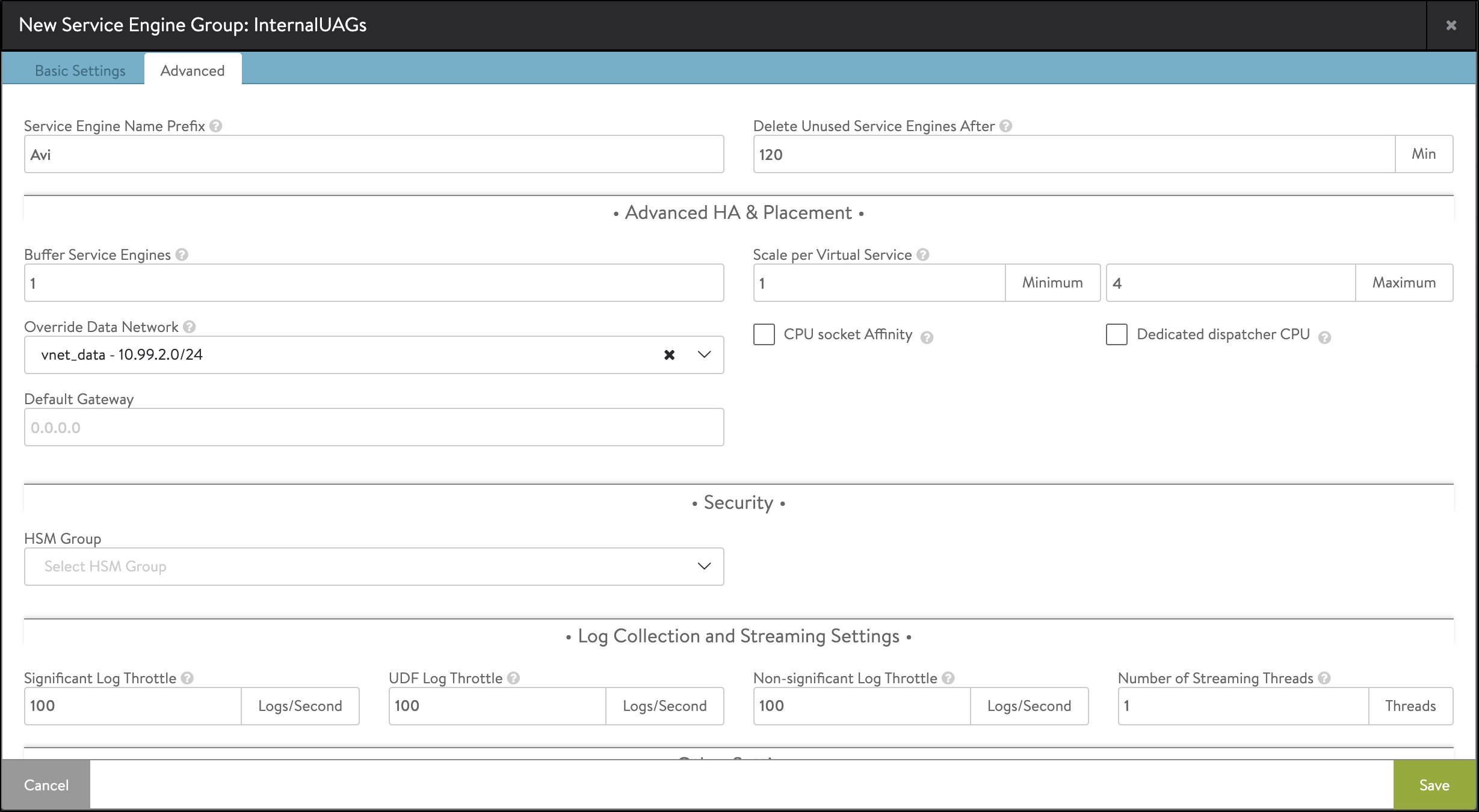
Creating pools, the health monitor, and the virtual service for internal UAGs are similar to that of external UAGs. For more information, see Creating a New SE Group.
Best Practice
It is recommended to create a new SSL profile and bind the same to the virtual service instead of using the default SSL profile for higher security ratings.
To create a new SSL profile,
-
Navigate to .
-
In the New SSL/TLS Profile screen, select the Ciphers and the TLS version.
-
Enable TLS 1.1 and TLS 1.2 for backward compatibility with older Horizon clients.
-
Click Save.
This profile will ensure that there are no issues with backward compatibility with old clients and also avoid security related issues.
Configuring Single L4 Virtual Service on NSX Advanced Load Balancer
In this design, a single virtual service with an L4 profile services all protocols.
Configuring L4 Virtual Service on NSX Advanced Load Balancer
L4 virtual service configuration on NSX Advanced Load Balancer is done in the following steps:
-
Create custom health monitor for UAG.
-
Create a Pool
-
Create an L4 Virtual Service
Creating a Pool
-
From the NSX Advanced Load Balancer UI, navigate to .
-
Click Pool.
-
Configure the pool by adding the necessary details.
-
Click +Add Health Monitor and select Horizon HTTPS Monitor that was created.
-
Navigate to Step 3: Advanced.
-
Select Disable Port Translation.
-
Click Next and Save.
Creating L4 Virtual Service
-
From the NSX Advanced Load Balancer UI, navigate to .
-
Click .
-
In the New Virtual Service: screen, enter the virtual service name and other details.
-
Under Service Port, click Switch to Advanced.
-
Add the following port numbers for both the primary and secondary protocols:
-
443 for primary HTTPS protocol
-
443 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile
-
8443 for Blast
-
8443 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile
-
4172 for PCoIP
-
4172 UDP to override TCP/UDP and use System-UDP-Fast-Path-VDI as the profile

Note:The application profile and the pool (Horizon-L4-pool)are bound to the virtual service.
-
-
Click Next and navigate to the Step 4: Advanced tab.
-
Select ExternalUAGs as the SE Group.
-
Click Save.
With this, the configuration is complete and ready to use the NSX Advanced Load Balancer for Horizon.
Configuring NSX Advanced Load Balancer VIP in the UAG Configuration Setting in Horizon Cloud Pod
Note down the public IP of the NSX Advanced Load Balancer virtual service and configure the same IP as the public IP in the UAG configuration setting in the Horizon Cloud pod. Save the Horizon pod configuration so that the Blast and PCoIP URLs on the UAG now point to the Virtual IP.
-
Ensure that the DNS server is appropriately configured to resolve the Horizon FQDN to the NSX Advanced Load Balancer Virtual IP.
-
Work with the VMware Horizon operations team to provide the NSX Advanced Load Balancer virtual service IP for the VS just created. The operations team will configure this IP as the PCoIP URL.
-
If the PCoIP URL is not updated with the NSX Advanced Load Balancer VS IP for Internal VS, PCoIP connections through the internal clients will fail. Blast protocol will not be impacted.