This section explains the examples of TACACS+ Configuration.
ISE TACACS+ Server
Cisco ISE is a security policy management platform that provides secure access to network resources. Cisco ISE functions as a policy decision point and enables enterprises to ensure compliance, enhance infrastructure security, and streamline service operations.
To set up an ISE TACACS+ server as a remote authentication and authorization system for NSX Advanced Load Balancer, follow the steps given below:
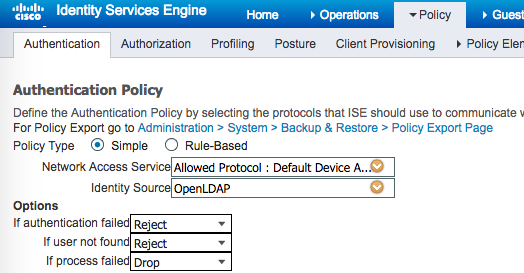

-
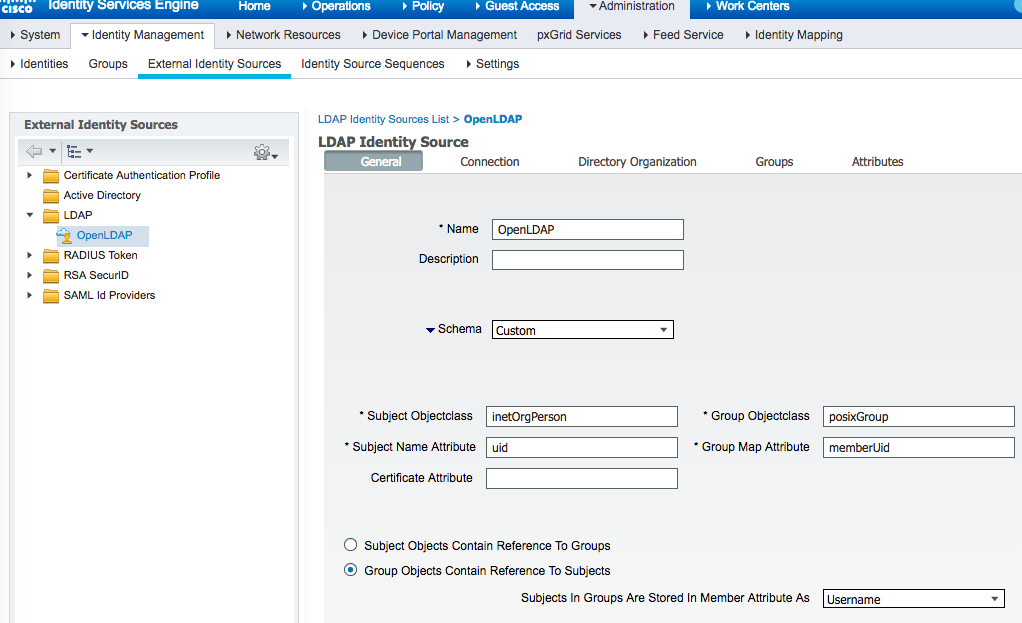
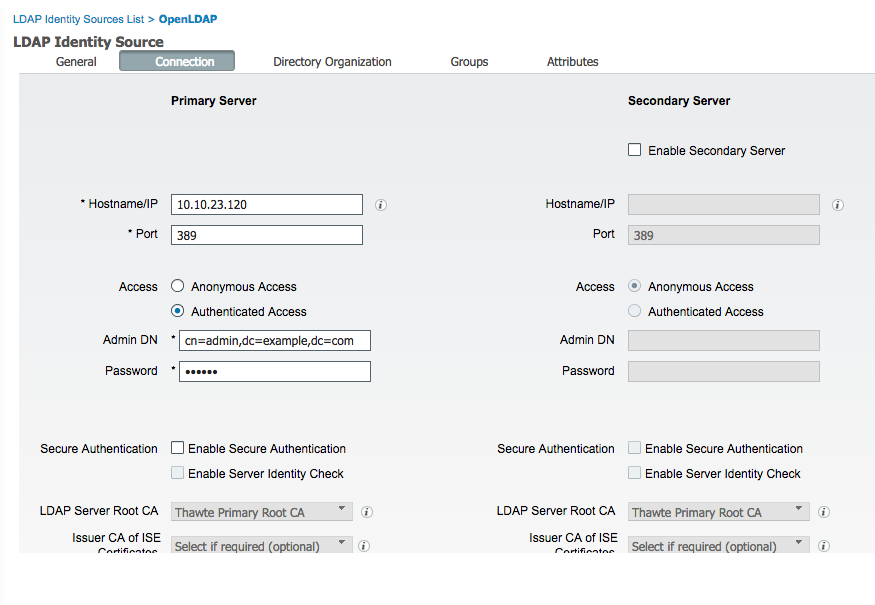
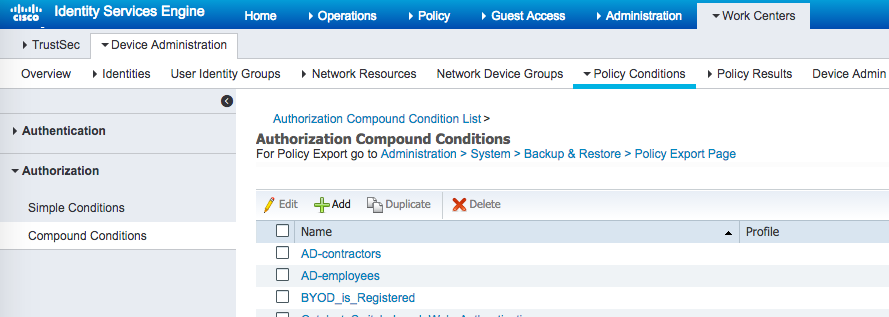
The ISE LDAP settings used to fetch LDAP groups and use them for Authorization conditions are as shown below:
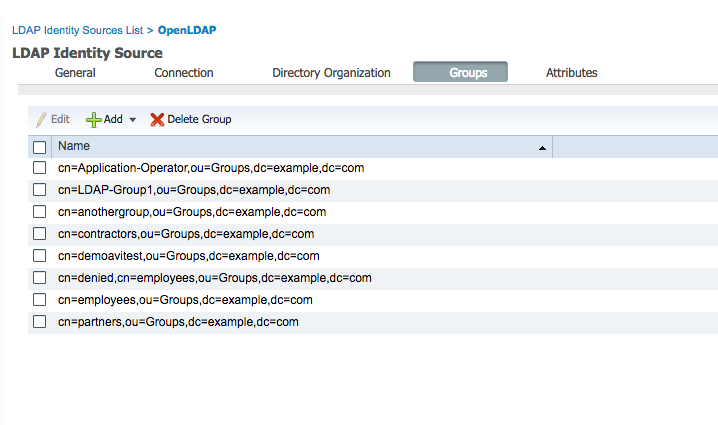
-
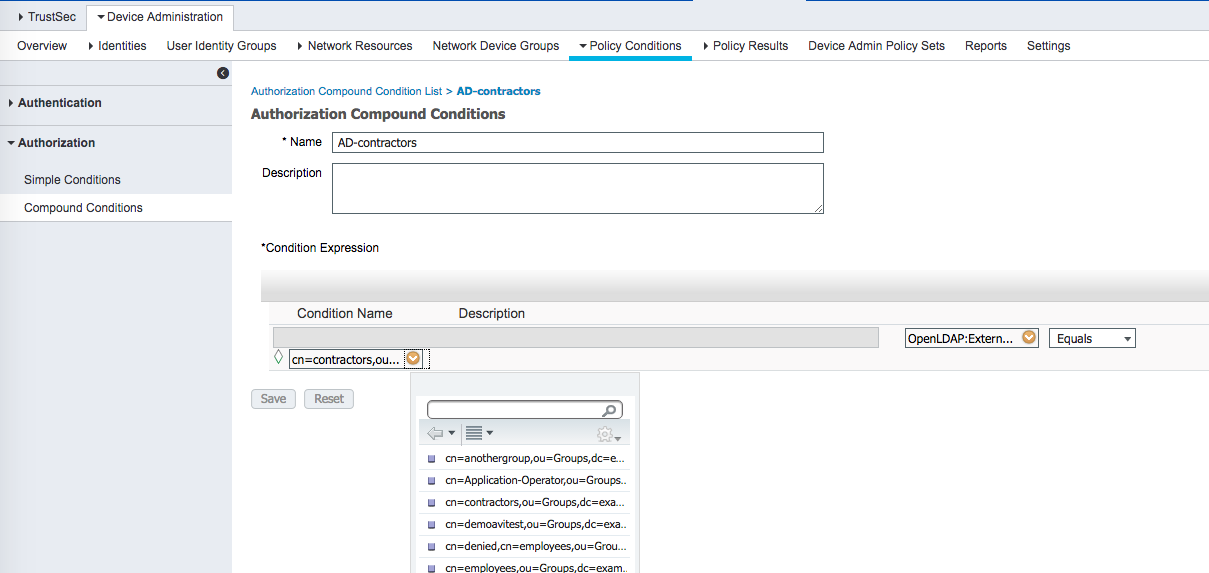
ISE Authorization conditions added for Users in the AD groups.
-
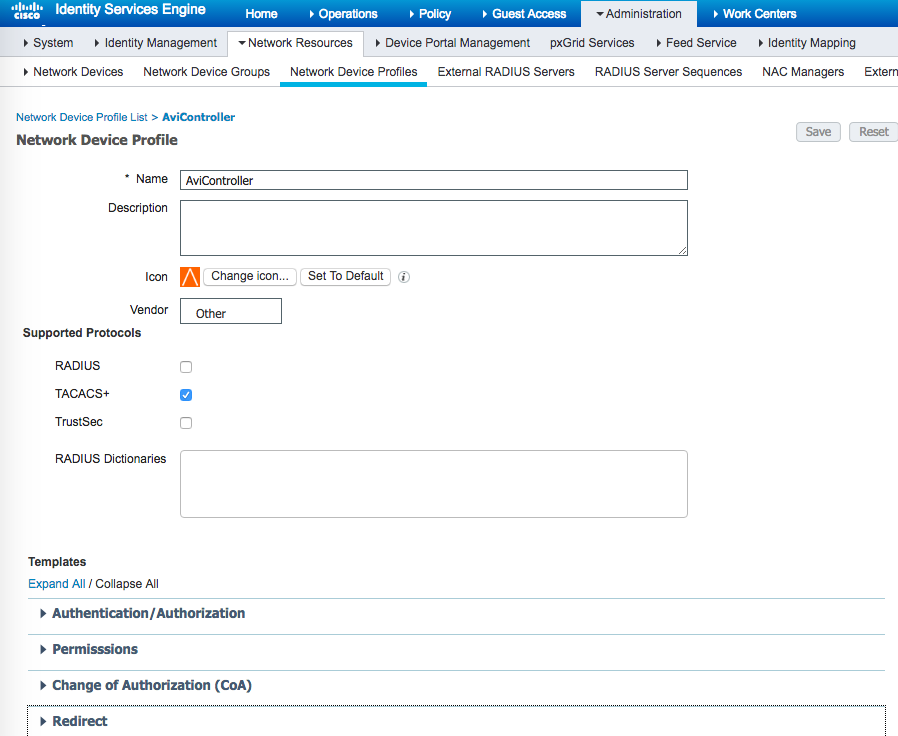
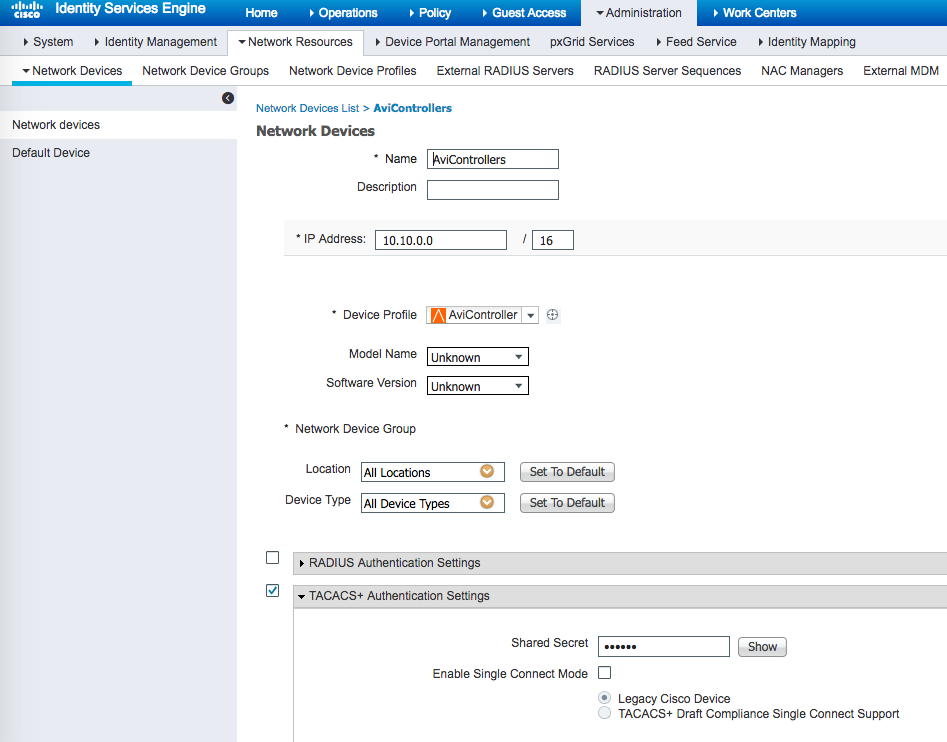
ISE server recognizes all NSX Advanced Load Balancer Controller cluster nodes as valid Network Devices.
-
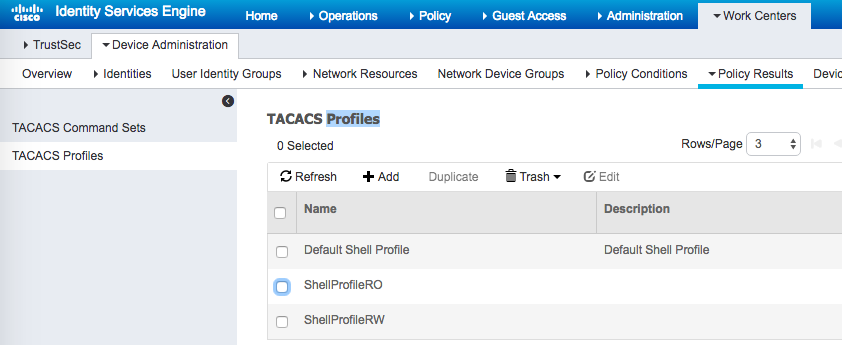
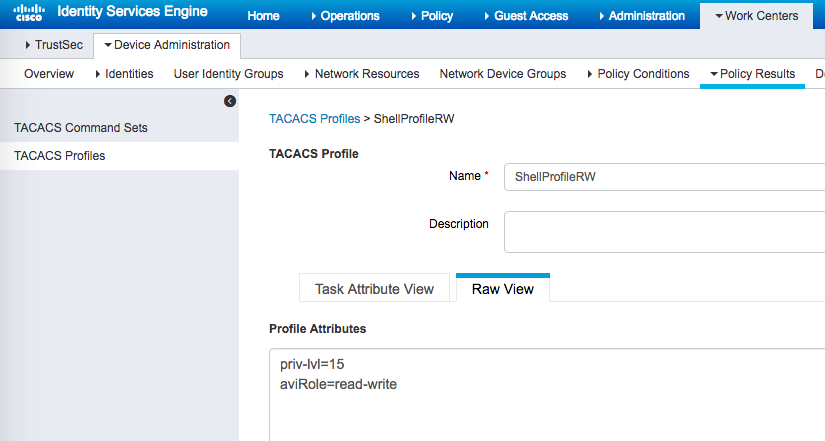
Configuring ISE requires shell profiles and TACACS+ profiles.
-
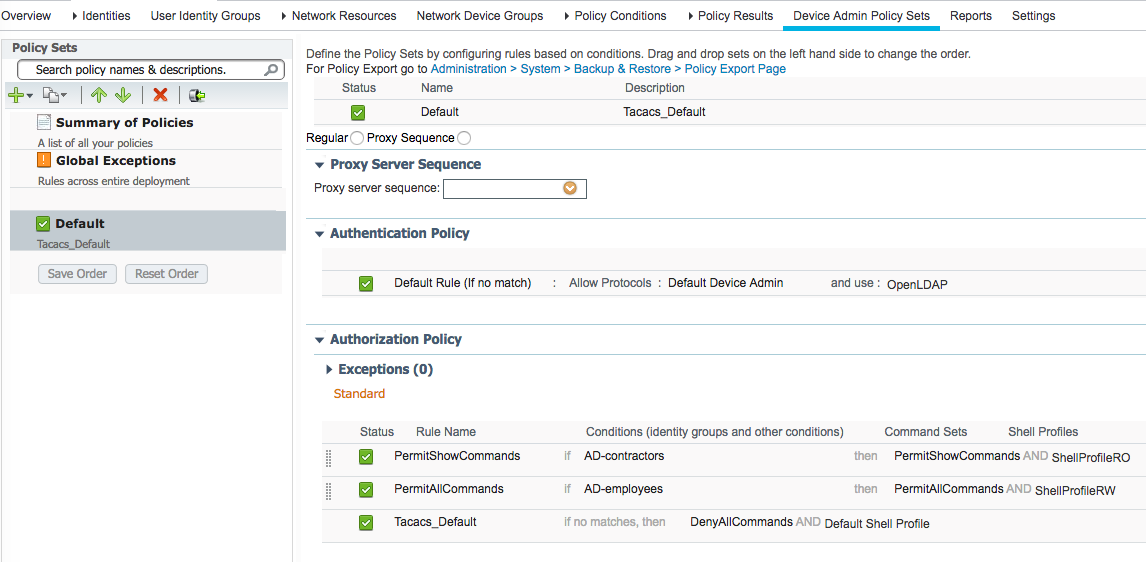
ISE device policy sets default condition updated to assign different shell profiles based on group membership.
The NSX Advanced Load Balancer TACACS+ auth profile must be configured with the same shared secret that was assigned to the device in ISE. The “service” attribute is generally required to identify and authorize a NSX Advanced Load Balancer user. Authorization attributes from a TACACS+ server can be used to map NSX Advanced Load Balancer users to various roles and tenants.
In the case of an ACS server, service=avishell is required for user authorization; while in the case of an ISE server, service=avishell is known to cause authorization failure.
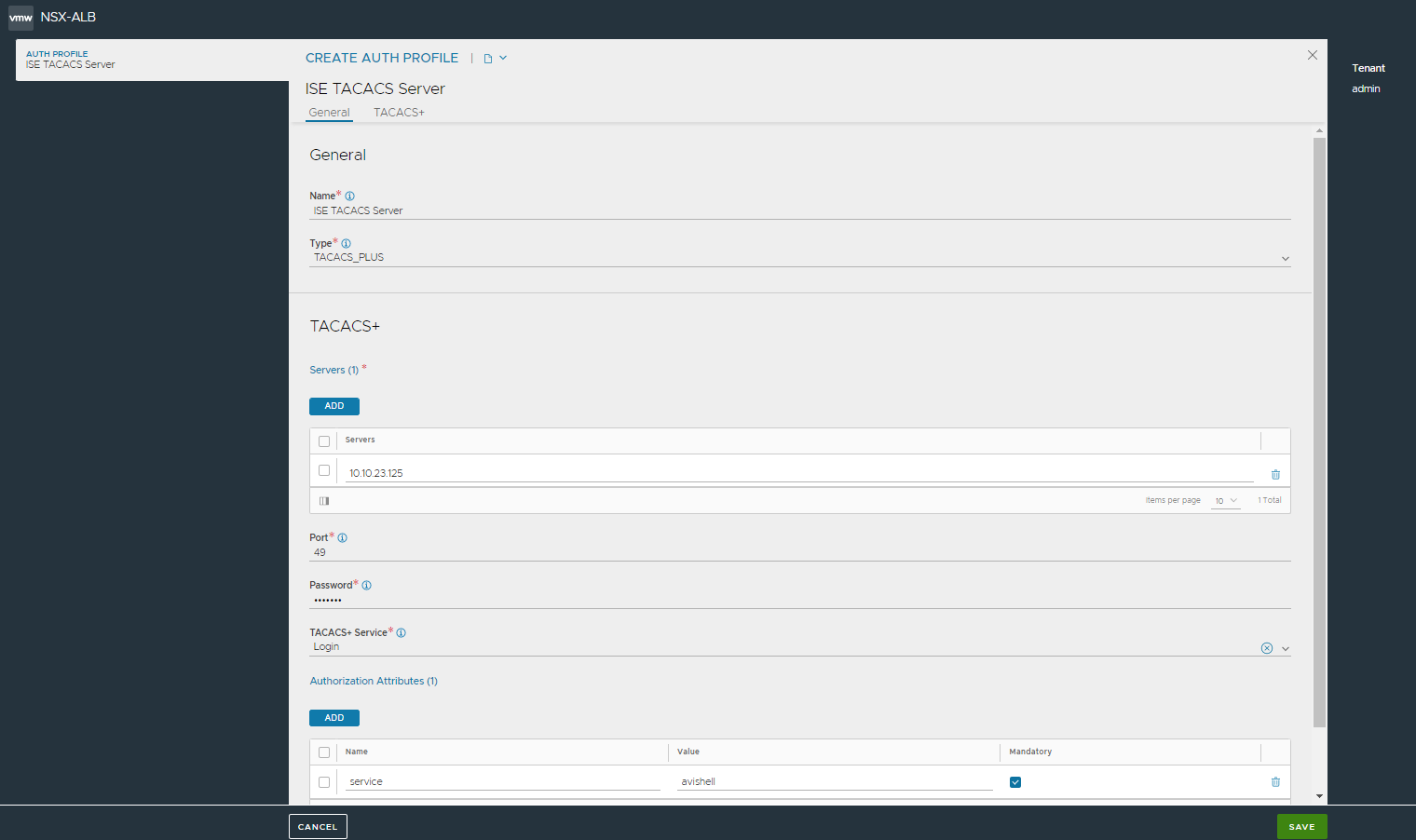
NSX Advanced Load Balancer TACACS+ authorization role and tenant mapping configured to assign different roles based on TACACS+ attribute value.
Shrubbery TAC_PLUS
-
TAC_PLUS server is a much simpler alternative to ISE/ACS. This is relevant in development or testing environments. Conceptually, users are assigned to groups and groups have request and response attributes.
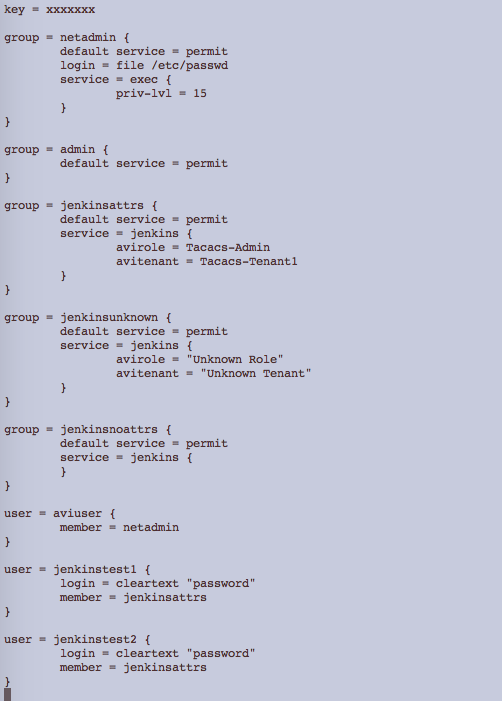
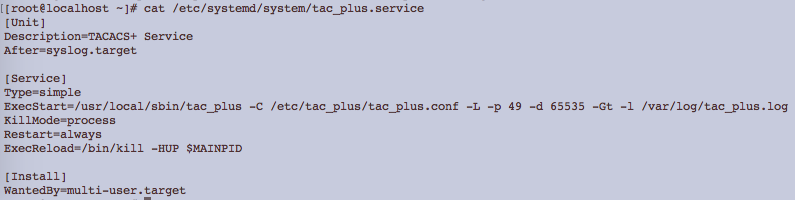
The NSX Advanced Load Balancer TACACS+ auth profile can be configured in the same way as an ISE or ACS.