NSX Advanced Load Balancer supports authentication and authorization of NSX Advanced Load Balancer users with Terminal Access Controller Access Control System (TACACS+). TACACS+ is an open standards protocol that handles authentication, authorization, and accounting.
Creating a TACACS Plus Profile
In NSX Advanced Load Balancer, TACACS+ settings are configured in an auth profile. To create a TACACS+ auth profile, complete the following steps.
Navigate to the .
Click Create to view the CREATE AUTH PROFILE screen.
Select the Type as TACACS_PLUS.
Under the TACACS+ tab, click Add to enter TACACS+ server IP address.
Note:You can add multiple servers. If the first server does not respond, NSX Advanced Load Balancer tries the next server. If there is no response from this server as well, NSX Advanced Load Balancer tries to connect to the next server. Each server is tried once. If all the servers fail or timeout, the request is failed.
Enter the TACACS+ server Port. By default, the value is 49.
Enter the TACACS+ server shared secret as Password.
Select the TACACS+ Service type used in all authentication and authorization queries.
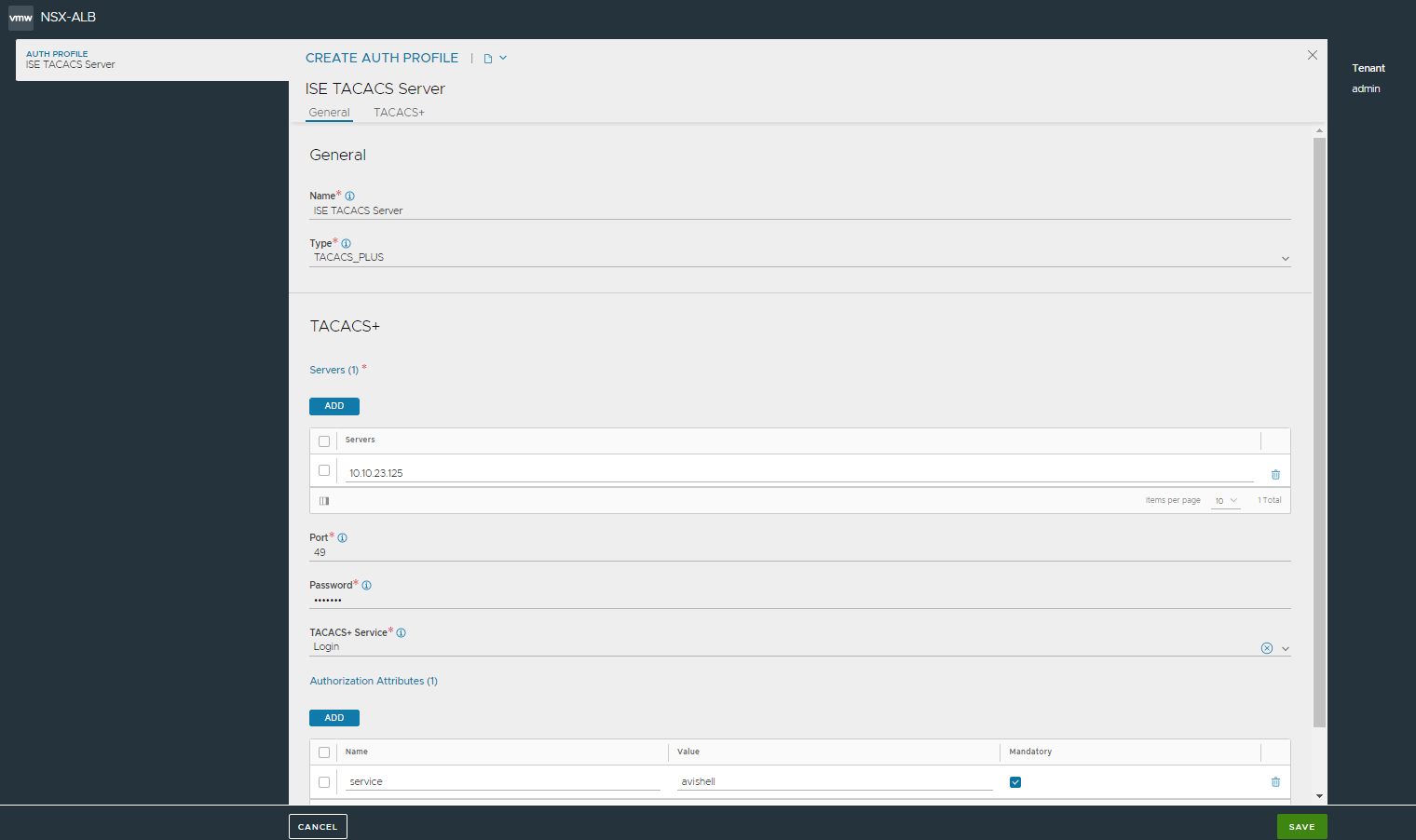
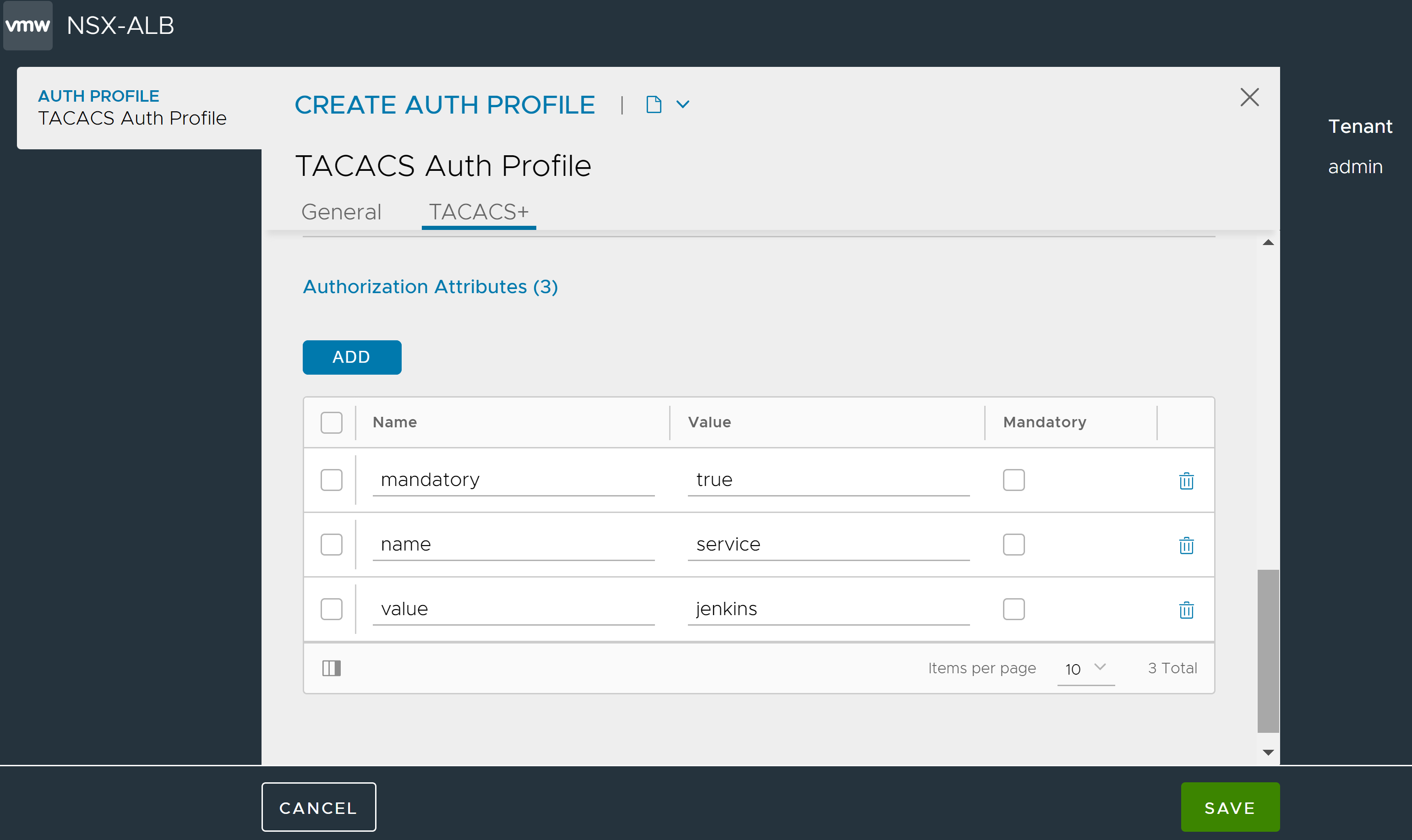
Under Authorization Attributes, click Add and enter the set of attribute value pairs under Name and Value to identify the host. The TACACS+ server configures user-level authorization based on these attributes. For example, Cisco Access Control Servers (ACSs) typically expect authorization attribute values for “service” and “protocol” to be populated to identify and authorize an NSX Advanced Load Balancer user. Authorization attributes from a TACACS+ server can be used to map users to various roles and tenants.
If the attribute is required, check Mandatory.
Click Save.
Authentication and Authorization
Authentication and authorization of an NSX Advanced Load Balancer user with TACACS+ takes place as follows:
AUTHEN START packet from NSX Advanced Load Balancer to TACACS+ server. Contains:
action=login
authen_type=ascii
service=
user=
remote_addr=
AUTHEN REPLY packet from TACACS+ server to NSX Advanced Load Balancer. It contains status of type GETPASS indicating that password needs to be supplied for the user message field with text “Password.”
AUTHEN CONTINUE packet from NSX Advanced Load Balancer to TACACS+ server. It contains user message field with actual password from user.
AUTHEN REPLY packet from TACACS+ server to NSX Advanced Load Balancer. Contains:
SUCCESS status if password is valid and user is allowed
FAILED status
AUTHOR START packet from NSX Advanced Load Balancer to TACACS+ server. Contains:
User name of the user
Remote address of the user
Authorization attribute name, value and whether or not they are mandatory
An authorization attribute string “abc=xyz” that indicates an attribute named “abc” is mandatory and has value “xyz”
An authorization attribute string “abc*xyz” that indicates an attribute named “abc” is optional and has value “xyz”
AUTHOR REPLY packet from TACACS+ server to NSX Advanced Load Balancer. It contains one of the following:
PASS_ADD or PASS_REPL status, which authorizes the successfully authenticated user with attribute value pairs to be added or replaced.
FAIL status, indicating the user is not authorized.
Encryption
All TACACS+ packets are encrypted, whereas the 12-byte header is passed in the clear. Encryption is part of the TACACS+ standard and is compatible with all TACACS+ servers.
Error Handling
If an error is indicated in the Status field of any reply packet during this process, the user login is rejected and results in a failure.