NSX Advanced Load Balancer supports user authentication using Lightweight Directory Access Protocol (LDAP). LDAP is a commonly used protocol for accessing a directory service. A directory service is a hierarchical object oriented database view of an authentication system. LDAP settings can be configured in an authentication profile.
Creating an LDAP Auth Profile
To create an LDAP Auth Profile, perform the following steps.
Navigate to .
Under the General tab, enter the Name of the profile and select the Type of the Auth Profile as LDAP.
Configure the LDAP settings.
Click Save.
Configuring LDAP Settings
Under the LDAP tab, click Add to enter the LDAP server IPs.
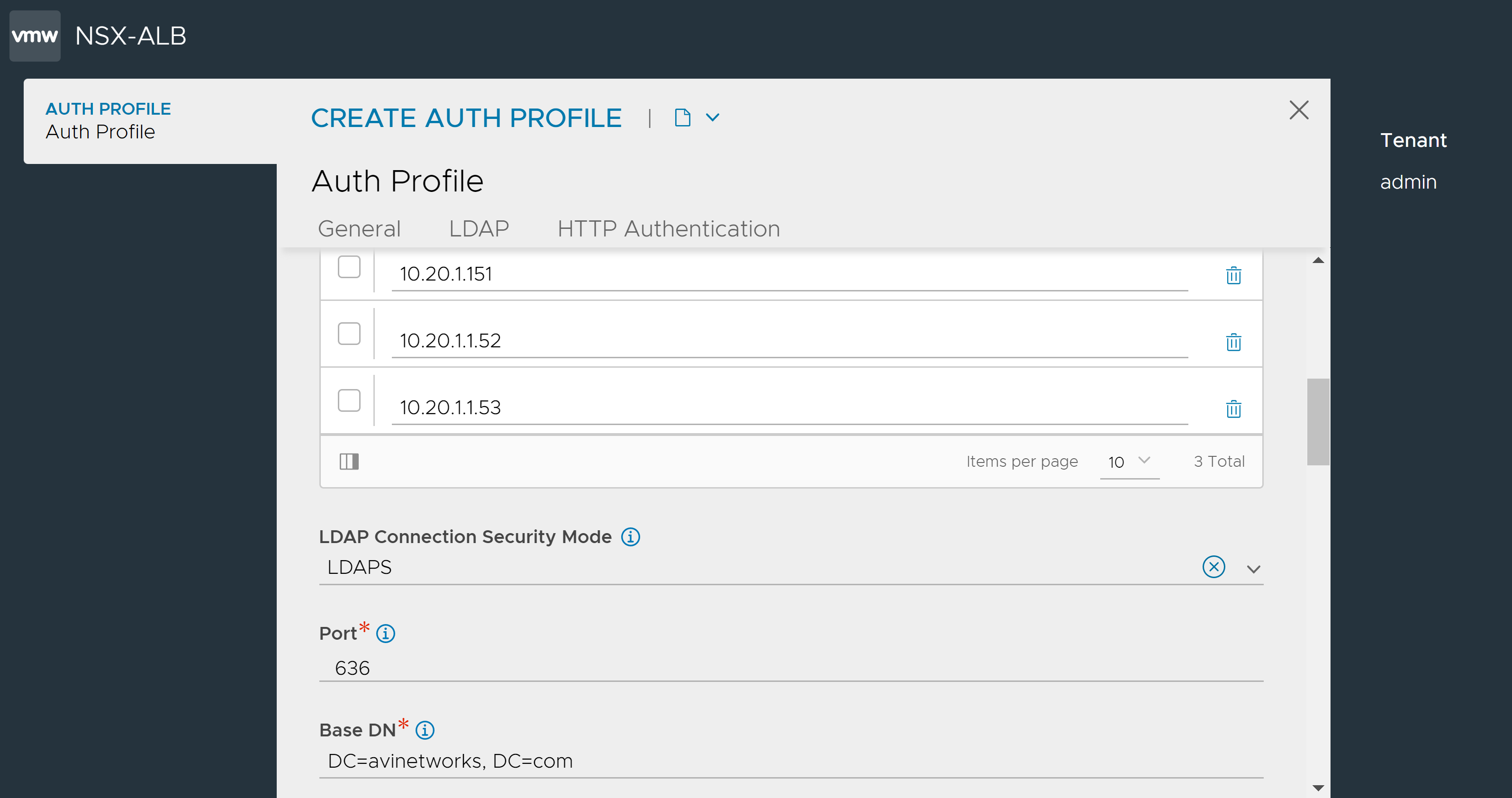
Note:Assume there are three LDAP servers. When a user logs in, the Controller validates the credentials against the first LDAP server. If a match is detected, the Controller stops further checks. However, if no match is found, the Controller continues to validate against the remaining LDAP servers in the configured order until a match is found. If no match is identified across all servers, an error is displayed.
Select LDAPS or None from the LDAP Connection Security Mode drop-down menu as required. Selecting None defaults to LDAP.
Enter the Port on which NSX Advanced Load Balancer queries the LDAP servers. Use port
389for LDAP and636for LDAPS (SSL).Note:Configuring the port does not determine if the LDAP security mode is LDAPS. Hence, explicitly select LDAPS as the LDAP Connection Security Mode to ensure secure connection between an LDAP client and server.
In the Base DN field, enter the top level path in the directory server object hierarchy.
Select the LDAP Bind Settings.
- Administrator Bind
-
The administrator account provided will be used to search for users and user group memberships across the LDAP server.
Note:Administrator Bind is the recommended LDAP Bind option.
An LDAP Admin Bind DN (Distinguished Name) is a unique identifier used to authenticate an administrative user to an LDAP server. It is typically set up during the initial configuration of the LDAP server and is used to perform administrative tasks:
Managing the directory structure.
Adding or modifying user entries and configuring the server itself.
The Admin Bind DN is essential for performing administrative tasks. It is important to safeguard the associated credentials to prevent unauthorized access and maintain the security of the LDAP directory. It is also important to ensure that the Admin Bind DN has sufficient privileges to perform the required operations, for example, in OpenLDAP, the Admin Bind DN is often set to
cn=admin,dc=example,dc=com.where,
dc=example
dc=com is the base DN of the LDAP server
The Admin Bind DN and Admin Bind Password are the credentials used to authenticate the administrative user to an LDAP server. The Admin Bind Password is associated with an administrative user's DN. The account used must have access to search the directory tree for both users and user groups.
NSX Advanced Load Balancer uses the configuration to search for users or groups. An LDAP search typically requires:
Top-level directory hierarchy (search DN) to start the search.
The scope value limits the search to one of the following: base (one-level deep) or entire subtree.
Filter to match only on entries of a given class or category.
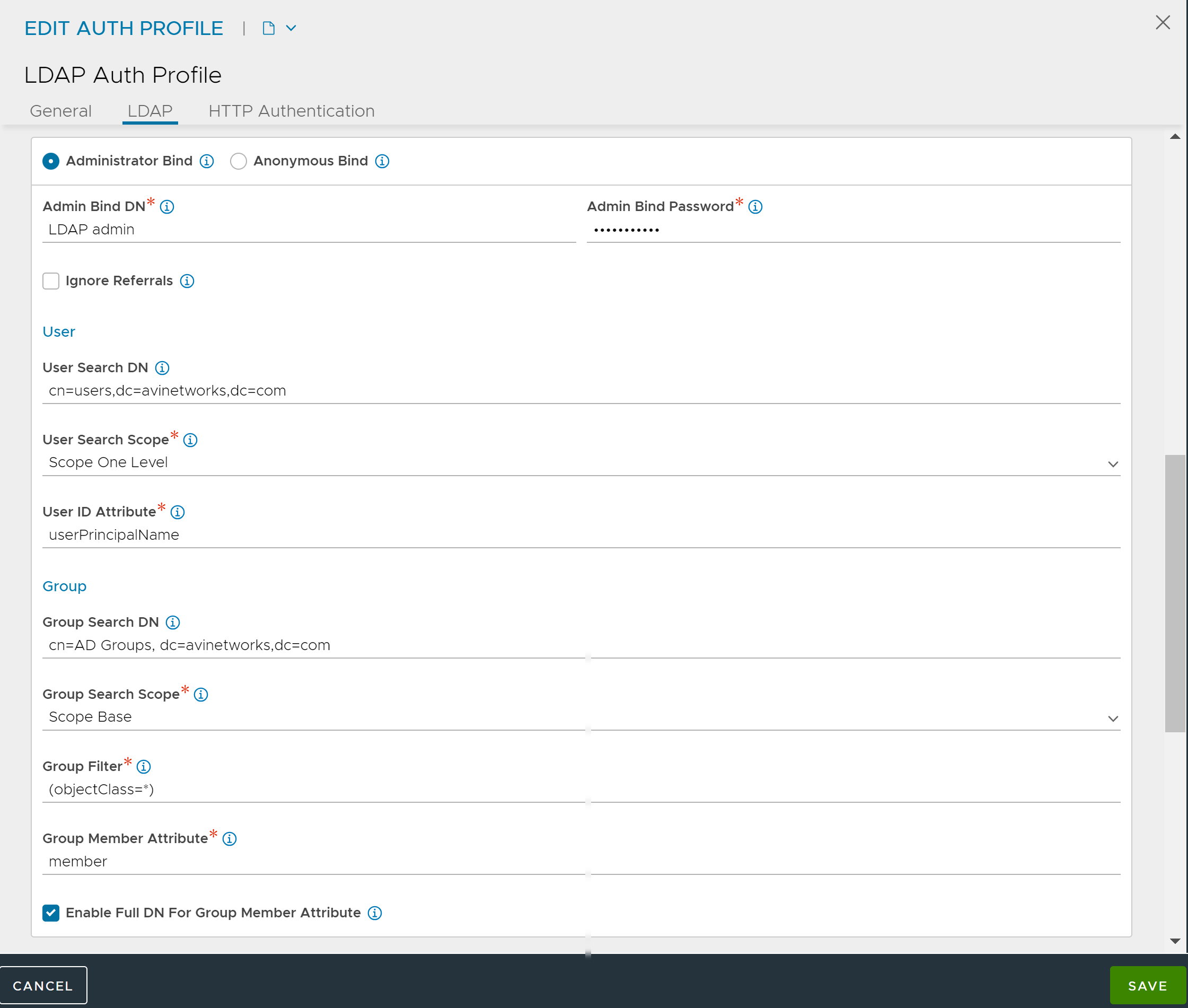
To configure Administrator Bind, enter the following:
Field
Description
User Search DN
LDAP User Search DN is the root of search for a given user in the LDAP directory. It helps ensure that the search is efficient and focused only on the relevant part of the directory tree where user information is stored. Only user records present in this LDAP directory sub-tree are allowed for authentication. Base DN value is used if this value is not configured.
User Search Scope
LDAP User Search Scope determines the extent of search for the user starting from user search DN.
The different levels of user search available are:
Base - The search is limited to the specified base DN.
One Level - The search is limited to the specified base DN and its immediate child entries.
Subtree - The search is performed on the entire tree, starting from the specified base DN.
User ID Attribute
LDAP User ID Attribute is the login attribute that uniquely identifies a single user record. The value of this attribute must match the user name used at the login prompt.
Group Search DN
LDAP Group Search DN is the root of search for a given group in the LDAP directory. Only matching groups present in this LDAP directory sub-tree will be checked for user membership. If this value is not defined, the base DN value is used.
Group Search Scope
Define the LDAP Group Search Scope using filters for the group starting from the group search DN.
The different levels of group search available are:
Scope Base
Scope One Level
Scope Subtree
Group Filter
LDAP Group Filter is a search filter used to focus the search results to specific group entries within the directory. A search can find many different types of objects under the search DN. Specify the Group Filter to pick up objects specific to the group only. The default group filter is (objectClass=*).
NSX Advanced Load Balancer appends a user-specific group membership filter to the configured group filter to check a specific user’s group membership.
Group Member Attribute
LDAP Group Member Attribute is a multi-valued attribute that can store the DNs of the users who are members of the group. It is used for retrieving data about group members and managing group membership.
For example, member and memberUid are commonly used attributes.
Enable Full DN For Group Member Attribute
Enable this option if the group member entries have full DNs instead of just user ID attributes.
For example, a configured group filter (objectClass=group) is extended by NSX Advanced Load Balancer to a full filter when user “bob” logs in to something such as the following: (&(objectClass=group)(member=bob)).
- Anonymous Bind
-
Anonymous Bind is a method of connecting to an LDAP server without providing any credentials. It is useful when the user has no access to an administrator account on the LDAP server(s). However, the level of access granted to an anonymous bind is typically limited and depends on the configuration of the LDAP server.
To configure Anonymous Bind, enter the following:
Field
Description
User DN Pattern
User DN Pattern is used to bind an LDAP user after replacing the user token with the real user name. The pattern must match the user record path in the LDAP server.
User Token
User Token is replaced with the real user name in the user DN pattern.
For example, a User DN Pattern could be
uid={0},ou=Users,dc=example,dc=com.where,
{0}=Username
User ID Attribute
User ID Attribute is the unique property that identifies a single user record. This value must match with the user name used at the login prompt.
Note:Authentication profiles that use anonymous bind cannot be used for role or tenant mapping.
An LDAP profile configured with Administrator Bind is as shown below:
Enable Ignore Referrals for the group search to skip referrals links that connect to another LDAP server. This option is deselected by default.
Note:Enabling the option Ignore Referrals can quicken the group searches by preventing delay in LDAP group search due to unnecessary referral searches. For more information, see RFC4511.
Under User, define the scope of search for users who log into NSX Advanced Load Balancer.
Click SAVE.