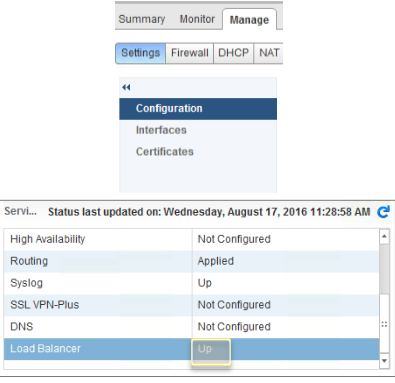
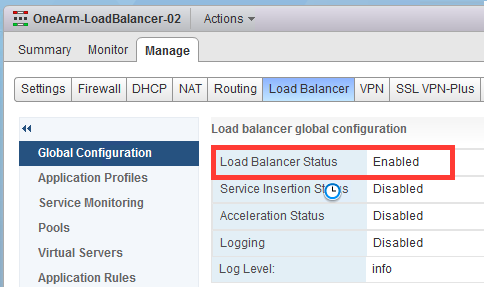
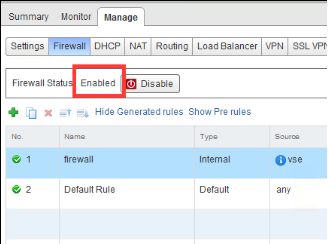
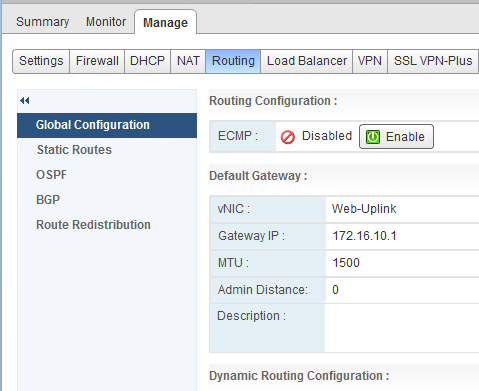
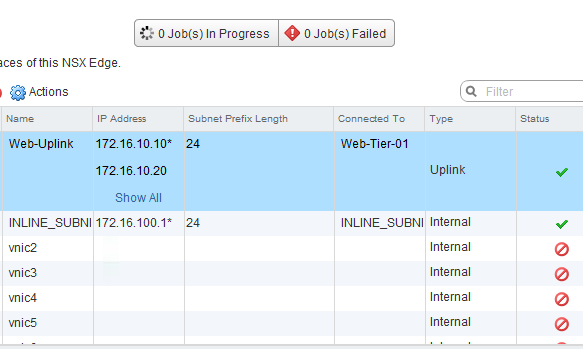
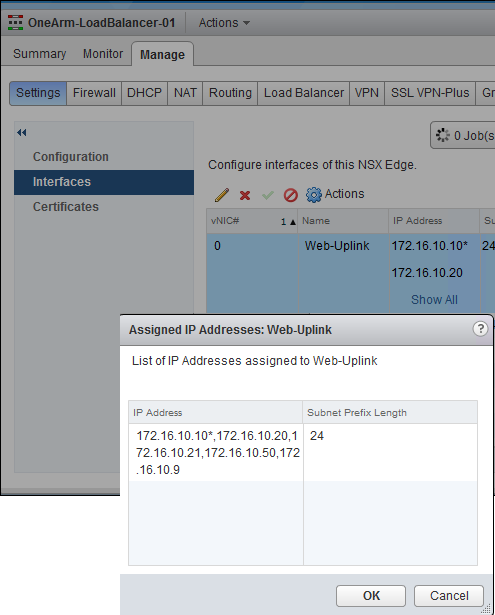
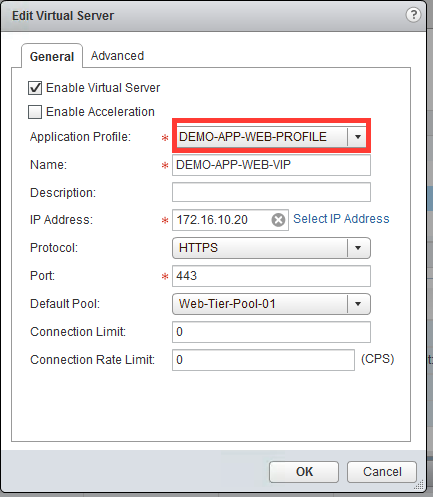
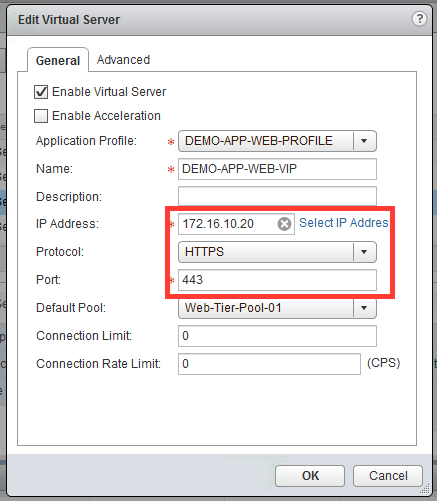
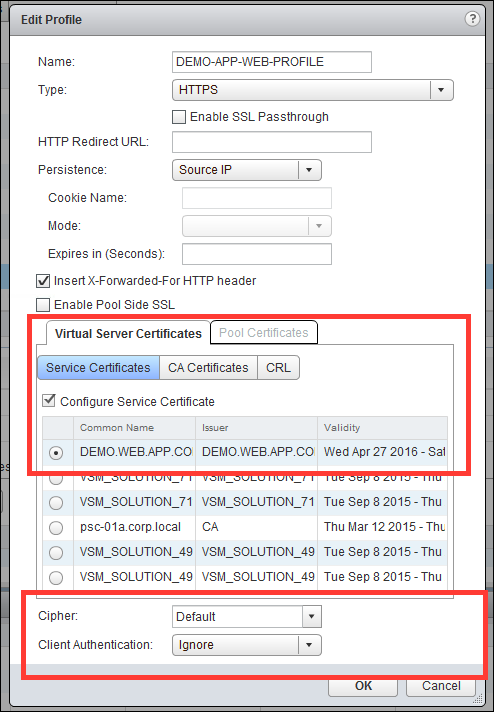
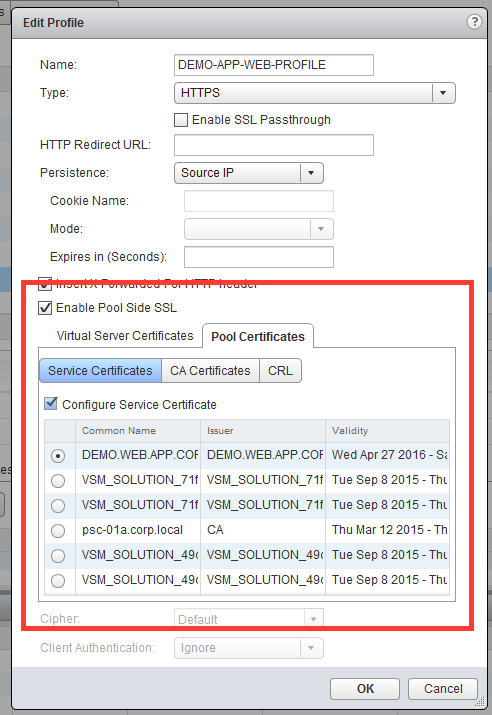
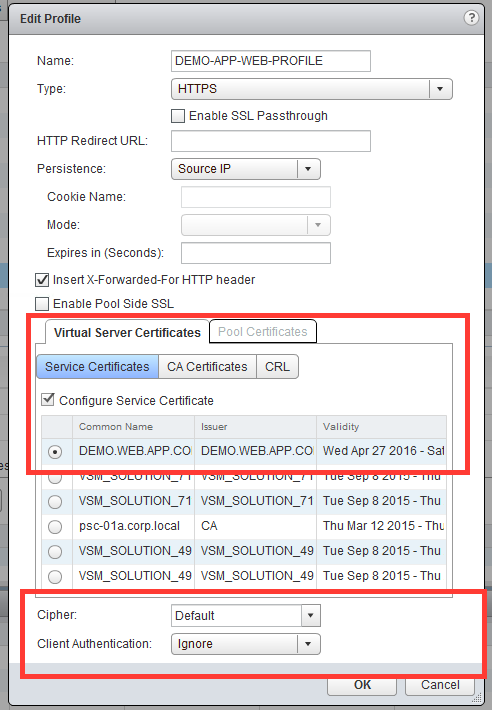
You can verify the load balancer configuration through the vSphere Web Client. You can use the UI to do some load balancer troubleshooting.
After understanding what should be functioning and defining a problem, verify the configuration through the UI as follows.
Problem
Load balancer is not working as expected.
Prerequisites
Note down the following details:
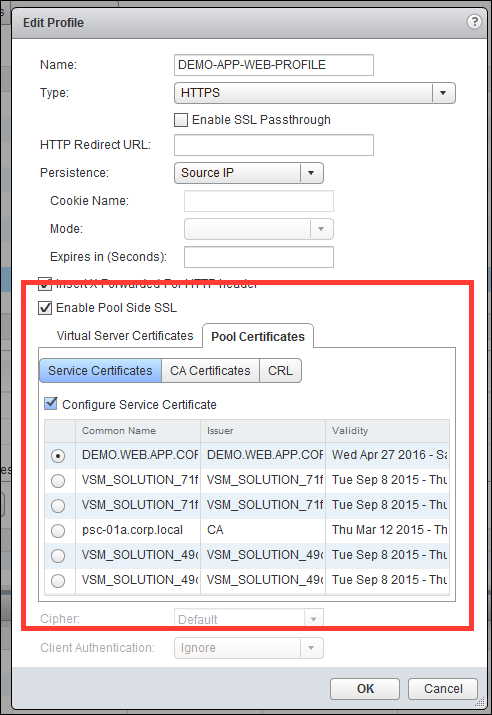
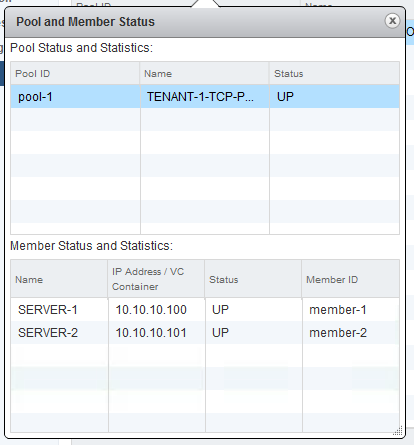
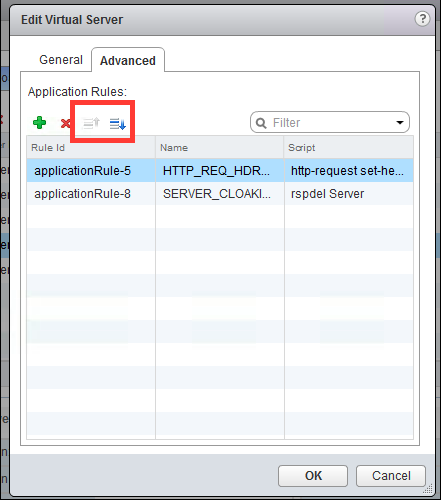
- The IP, protocol, and port of the virtual server.
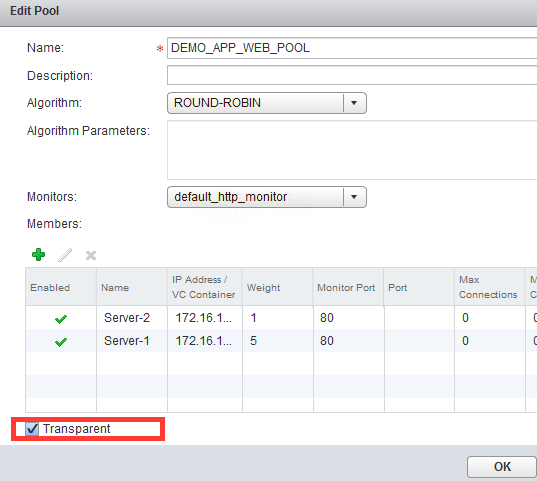
- The IP, and port of the backend application servers.
- The topology that was intended - inline or one-armed. For details, refer to the Logical Load Balancer topic in NSX Administration Guide.
- Verify the trace route and use other network connectivity tools to see that the packets are going to the correct location (edge services gateway).
- Verify any upstream firewalls are allowing the traffic correctly.
- Define the problem that you are facing. For example, DNS records for the virtual server are correct, but you are not getting back any content, or incorrect content, and so on.
Solution
What to do next
If you could not find the problem, you may need to use the CLI (Command Line Interface) to find out what is happening. For more information, refer to Load Balancer Troubleshooting Using the CLI.