| VMware NSX Migration for VMware Cloud Director 1.3.2 | 21 APR 2022 Check for additions and updates to these release notes. |
What's New
The NSX Migration for VMware Cloud Director tool version 1.3.2 supports several new features:
- UTF-8 characters support: You can migrate VMware Cloud Director objects that have names and descriptions with special characters or non-Latin-based languages.
- Routed vApp Network: You can migrate vApps with a routed vApp network including vApp edge networking services.
- Disk Level Storage Policy support: You can migrate VMs with disks having different storage policies.
- Enhanced Named Disk Migration: You can migrate named/independent disks attached to powered-on VMs without powering off those VMs. Named disks with different storage policies will also be migrated.
- Edge Gateway Rate Limits: You can migrate rate limits configured on edge gateways.
- Non-Distributed Routing with NSX-T Data Center: You can now enable non-distributed routing on routed Org VDC networks (such networks are connected via service interface directly to service router of Tier-1 gateway). Non-distributed routing will be enabled on Org VDC networks routed via an internal interface in one of the following two cases.
- Explicitly via setting input parameter NonDistributedNetworks in the YAML file.
- Implicitly if DNS relay is enabled and DNS IP is the same as Default Gateway IP. This together with autoconfigured DNAT of Default Gateway IP to DNS Forwarder IP will achieve the availability of DNS services on the same IP for migrated VMs.
- Multiple Tier-0 Gateways Support: You have an option to specify individual Tier-0 Gateways for each Edge Gateway in Org VDC. It is no longer mandatory to connect all target Edge Gateways to a single Tier-0 Gateway.
- Enhanced Direct Network Migration: Force migration of direct Org VDC networks to a different external network with -v2t suffix for service network use case. You can migrate with a legacy mechanism by setting the parameter LegacyDirectNetwork in the input YAML file.
- Less restrictive validation for DNAT+IPSEC: This validation is refined to block migration only if DNAT rules are configured on networks that are participating in IPsec VPN.
- Renamed ExternalNetwork toTier0Gateways: ExternalNetwork field in the user input YAML file which specifies the NSX-T Tier-0 Gateway is renamed to Tier0Gateways to match the name in the VMware Cloud Director user interface.
- Optional Tier0Gateways and DummyExternalNetwork: These two fields in user input YAML can be skipped if edge gateways are not present on the NSX for vSphere backed Org VDC.
- Guest VLAN migration: Routed Org VDC networks and routed vApp networks can be migrated with the Guest VLAN option enabled.
Known Issues
- Rollback Fails at ‘Reset the target external network’
Step:
[vcdOperations]:[resetTargetExternalNetwork]:3911 [INFO] [VDC-demo]| Rollback:Reset the target external networkException:
Failed to reset the target external network 'external-network-name' to its initial state: [ xx-xx-xx-xx-xx] The provided list 'ipRanges.values' should have at least one item in it.Reason: During rollback, the migration tool removes the IP address/s used by the target edge gateway from the target external network. If the target external network has no spare IP in its static IP Pool apart from the ones used by target edge gateway/s, then the migration tool will not be able to remove the IPs as a minimum of one IP should be present in every subnet of an external network.
Workaround: Add additional IP(s) to the static IP pool of the target external network and run the rollback.
- Cleanup Fails at ‘Updating the source External network’
Step:
[vcdNSXMigratorCleanup]:[run]:3542 [INFO] [VDC-demo]| Updating the source External network.Exception:
Failed to update source external network ‘external-network-name' : [ xx-xx-xx-xx-xx] The provided list 'ipRanges.values' should have at least one item in it.Reason: During cleanup, the migration tool removes the IP address/s used by the source edge gateway from the source external network. If the source external network has no spare IP in its static IP Pool apart from the ones used by source edge gateway/s, then the migration tool will not be able to remove the IPs as a minimum of one IP should be present in every subnet of an external network.
Workaround: IP/s need to be cleaned manually from the static IP Pool of the source external network in case of failure.
- VM loses N-S traffic after rollback
After rollback is completed, VMs may lose N-S connectivity. VM loses N-S traffic following vMotion to an NSX for vSphere host after NSX-v to NSX-T Edge migration cutover was done.
Fixed in NSX-T 3.1.3.3 (for more details, see NSX-T Release Notes).
- After migration to NSX-T, NAT rules are not editable through VMware Cloud Director UI
After the migration is completed, the NAT rules created at target are not editable using VMware Cloud Director UI. A lock symbol can be seen while selecting NAT rules.
Workaround: Use VMware Cloud Director API to edit the NAT rules. Issue fixed in VMware Cloud Director 10.3.2.
- VMs connected to distributed Org VDC networks lose network connectivity after N-S network switchover
VMs connected to distributed Org VDC networks lose network connectivity after N-S network switchover and bridging does not work.
Workaround: Ensure that the MAC Address of the NSX-T Virtual Distributed Router is using a different MAC address than the NSX-V distributed logical router. For more details, see NSX-T documentation.
- DNAT rules will not be created on non-distributed networks belonging to a Data Center Group (NSX-T backed)
When non-distributed routing is enabled on Org VDC networks with NSX-T data center and DNS IP same as the default gateway IP on that network, then the migration tool will create two DNAT rules to handle the DNS traffic. These 2 DNAT rules will not get created if the Org VDC network is part of the Data center group.
Will be fixed in the future VMware Cloud Director version.
Workaround: Create DNAT rules manually for DNS traffic after migration.
- Migration of encrypted VMs fail
Migration of encrypted running VM fails with "A powered-on encrypted VM is not allowed to change its profile." even though the underlying VC policy is not changing.
Will be fixed in the future VMware Cloud Director version.
Workaround: Power Off the VM before migration.
- Migration of VM with disconnected NIC fails
Migration of VM fails if a network is assigned to the VM NIC, but it's in disconnected state (by unchecking the "Connected" box in VMware Cloud Director Tenant Portal).
Workaround: Set the Network value for the VM to "None".
- Migration of VM with placement policy fails
The operation failed because no suitable resource was found. Out of 1 candidate hubs: 1 hubs eliminated because: Only contains rejected VM Groups(s): [[VM+Group1], [VM+group1]] Rejected hubs: resgroup-4416 PlacementException NO_FEASIBLE_PLACEMENT_SOLUTIONWorkaround: make sure that VM groups backing the source and target placement policy are identically named.
- External connectivity not working after migration
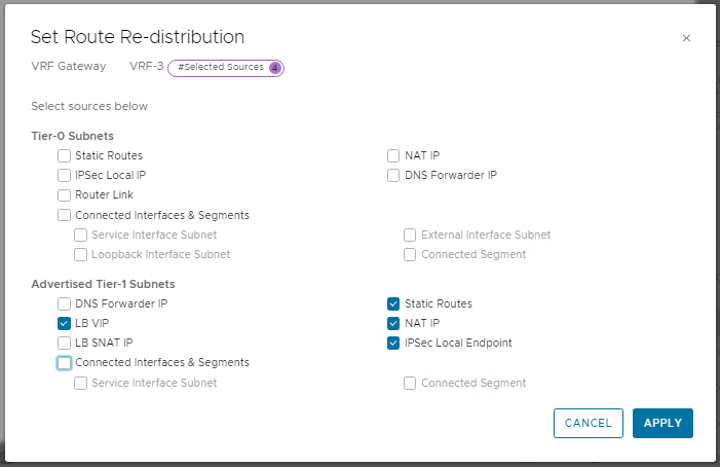
Even though the migration is successful, the Route re-distribution rules are not set on Tier-0/VRF gateway by VMware Cloud Director. The Tier-0/VRF gateway will not advertise Tier-1 gateway services upstream. Hence external connectivity will not work.
Workaround: Create Route Re-distribution set named SYSTEM-VCD-EDGE-SERVICES-REDISTRIBUTION in NSX-T, if not already present on the Tier-0/VRF gateway to which the Org VDC gateway Tier-1 is connected, then set the following Tier-1 networking services for route re-distribution if not already set.
- Advertised Tier-1 Subnets:
- Static Routes
- NAT IP
- LB VIP
- IPSec Local Endpoint
Additionally, enable the following services if static or dynamic routing is enabled on T1.
- Advertised Tier-1 Subnets:
- Connected Interfaces & Segments
- Service Interface subnet
- Connected Segment
- Connected Interfaces & Segments