With NSX Federation, you can deploy a tier-0 gateway that is limited to a single location, or you can stretch it across multiple locations.
- Non-stretched tier-0 gateway.
- Stretched active-active with primary and secondary locations.
- Stretched active-active with all primary locations.
- Stretched active-standby with primary and secondary locations.
Note: Active-standby tier-0 gateways are supported starting in NSX-T Data Center 3.0.1.
Non-Stretched Tier-0 Gateway
You can create a tier-0 gateway from Global Manager that spans only one location. This is similar to creating the tier-0 gateway on the Local Manager directly, but has the advantage that you can manage it from Global Manager.
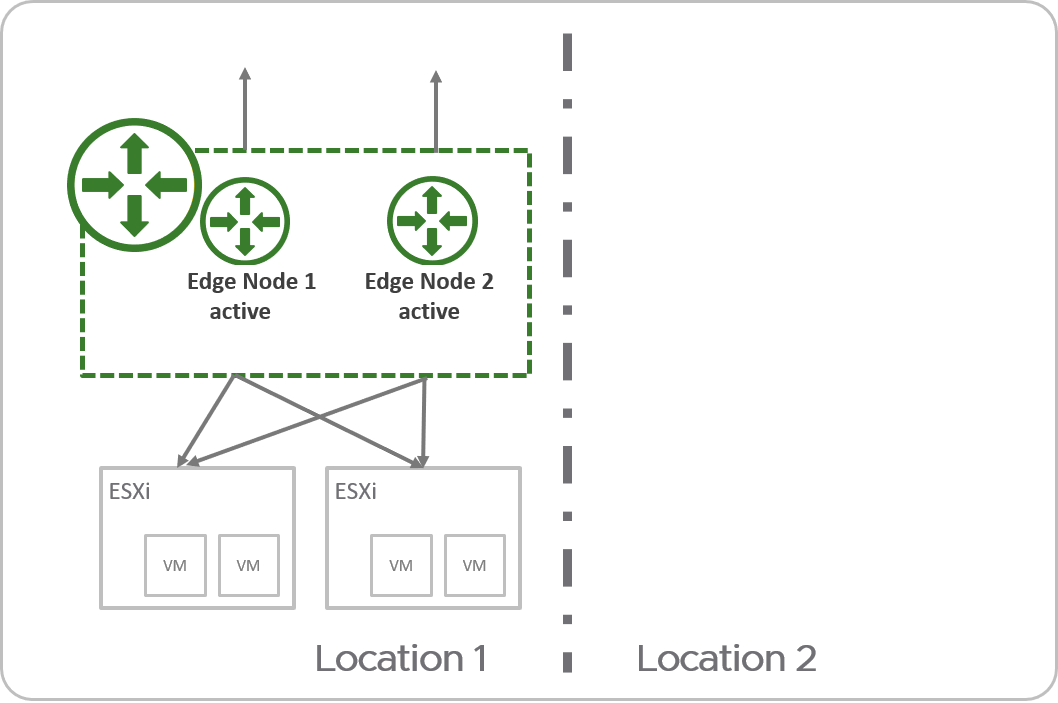
Stretched Active-Active Tier-0 Gateway with Primary and Secondary Locations
- All Edge nodes are active at the same time, therefore the tier-0 cannot run stateful services.
- All traffic enters and leaves through the Edge nodes in the primary location.
If both the tier-0 gateway and the linked tier-1 gateway have primary and secondary locations, configure the same location to be primary for both gateways to reduce cross-location traffic.
If your environment has stateful services, such as external firewall, on the physical network, you must ensure that the return traffic enters through the primary location. For example, you can add AS path prepending on the BGP peers in your secondary locations.
If you do not have stateful services on your physical network, and you choose to have asymmetric routing, you must disable Unicast Reverse Path Forwarding (uRPF) on all externally tier-0 interfaces.
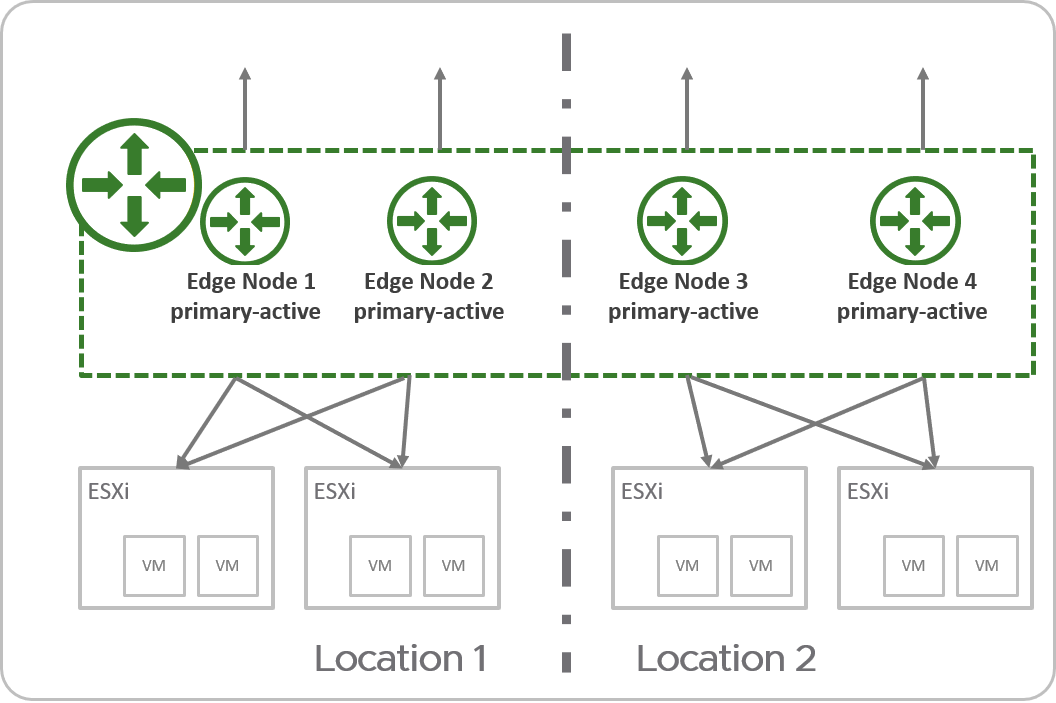
Stretched Active-Active Tier-0 Gateway with All Primary Locations
- All Edge nodes are active at the same time, therefore the tier-0 cannot run stateful services.
- All traffic enters and leaves through Edge nodes in the same location as the workloads.
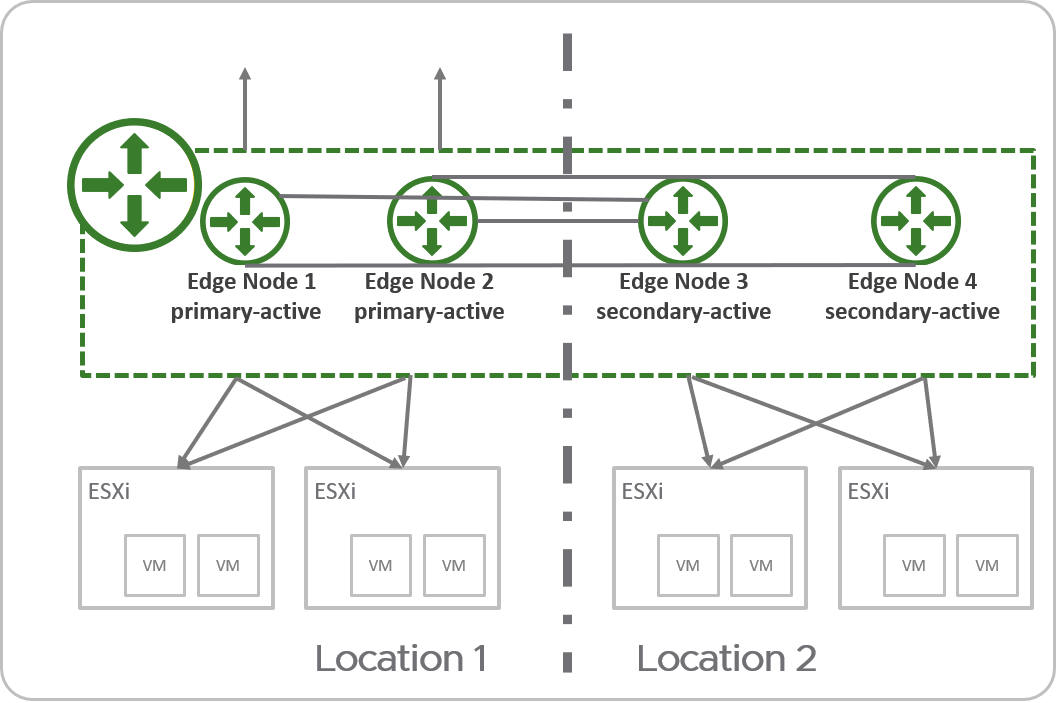
Stretched Active-Standby Tier-0 Gateway with Primary and Secondary Locations
- Only one Edge node is active at a time, therefore the tier-0 can run stateful services.
- All traffic enters and leaves through the active Edge node in the primary location.

- Network Address Translation (NAT)
- Gateway Firewall
- DNS
- DHCP