As a VI admin working in the vSphere environment, you can use the simplified workflow to prepare ESXi clusters for NSX-T security.
Use the vSphere Client to prepare ESXi clusters for NSX-T security. On such clusters, you can enable micro-segmentation, URL filtering and distributed IDS on application workloads. These clusters are not prepared for NSX-T virtual networking.
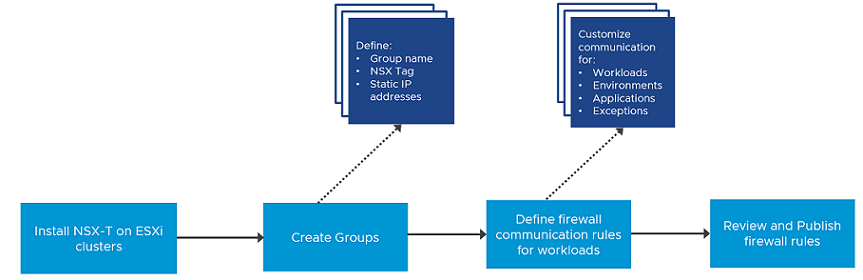
- Prepare Host Cluster.
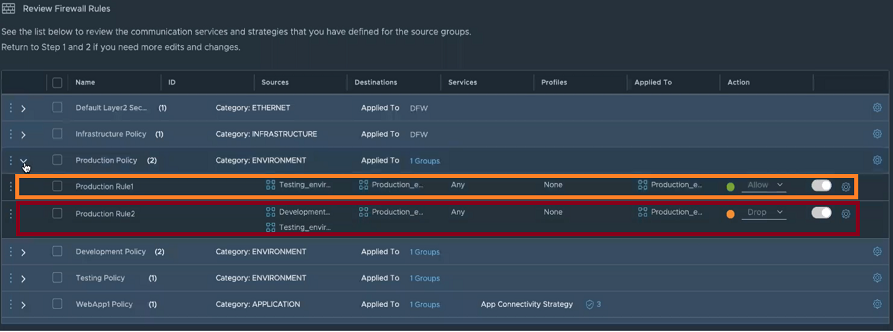
- Create Firewall Rules
- Create Groups for infrastructure services (Active Directory, DNS, and so on), environment groups (production or testing), and application groups (web, database, application).
- Define communication strategy. Some of the actions you can take are:
- Define communication between any workload and infrastrcture services.
- Define communication so that no environment can talk to each other.
- Limit communication to a specific port or protocol.
- Specifiy source workloads.
- Set up exeptions after setting up communication strategies for workloads.
- Define Action for Default Firewall Rule (to process traffic that does not match firewall rules defined in Communication section).
- Review and publish firewall rules.
Prepare Clusters for NSX-T Security
Select a host cluster to prepare it for NSX-T security.
The Getting Started section gives you the option to select between Security Only or Virtual Networking. When you choose to enable clusters only for security, the wizard asks you to define security rules and uses those rules to automatically configure NSX-T security on the distributed virtual port groups of the selected clusters.
Prerequisites
- Ensure that ESXi hosts are compatible with vCenter Server version v7.0.3 or later.
- Ensure that vCenter Server version is v7.0.3 or later.
- Configure a vSphere Distributed Switch (VDS) switch on hosts. Only VDS 6.6 or later is supported.
- On a vSphere Lifecycle Manager enabled cluster, edit the vCenter Server from the NSX Manager UI to:
- Create a service account and enable trust between NSX-T and vCenter Server. See Add a Compute Manager.
Procedure
Results
What to do next
To avoid any loss of connectiviy, add vCenter Server and NSX Manager to the DFW Exclusion list.
Add vCenter Server and NSX Manager to Distributed Firewall Exclusion List
To ensure connectivity to vCenter Server or NSX Manager VMs, add these VMs to the DFW firewall exclusion list in NSX-T.
After adding the vCenter Server and NSX Manager VMs to the DFW exclusion list, even when you configure the default firewall policy to Drop from the NSX-T plugin in vCenter Server, you will not lose connectivity to these VMs. Perform the following procedure from the NSX Manager UI.
Procedure
What to do next
Create Groups
As part of firewall creation, define infrastructure group that run selected services, such as DHCP, define environment groups, such as production, testing, or so on, comprising of selected group members and define application groups with selected group members.
Prerequisites
- Install NSX-T on the host cluster.
Procedure
Results
You created infrastructure groups, environment groups and application groups.
What to do next
After creating groups, define firewall rules that govern communication among workloads and these different groups.
Define and Publish Communication Strategies for Groups
After creating groups, define firewall rules to govern communication between groups, define exceptions and ports or protocols for communication.
Prerequisites
- Install NSX-T on the host cluster.
- Create Infrastructure groups, Environment groups, and Application groups.
Procedure
Results
The wizard ends and firewall policies you defined are applied to the groups. The NSX UI is available in vCenter Server.
What to do next
- In the NSX Manager UI, go to .
- On the Groups page, verify whether the workload groups you defined in vSphere Client are realized in NSX Manager.
- Go to page.
- On the Distributed Firewall page, verify whether the firewall rules you applied in vSphere Client are realized in NSX Manager.