This section provides the configuration workflow to prepare your environment using the NSX Distributed Security for protecting the virtual machines.
Prerequisites
You have deployed the NSX Manager and configured the valid licenses.
Configuration Workflow
Preparing your virtual environment for the NSX Distributed Security involves two main steps:
- Configure Compute Manager (vCenter)
- Prepare vCenter cluster ( ESXi hosts) for the NSX Distributed Security
1: Configure Compute Manager (vCenter)
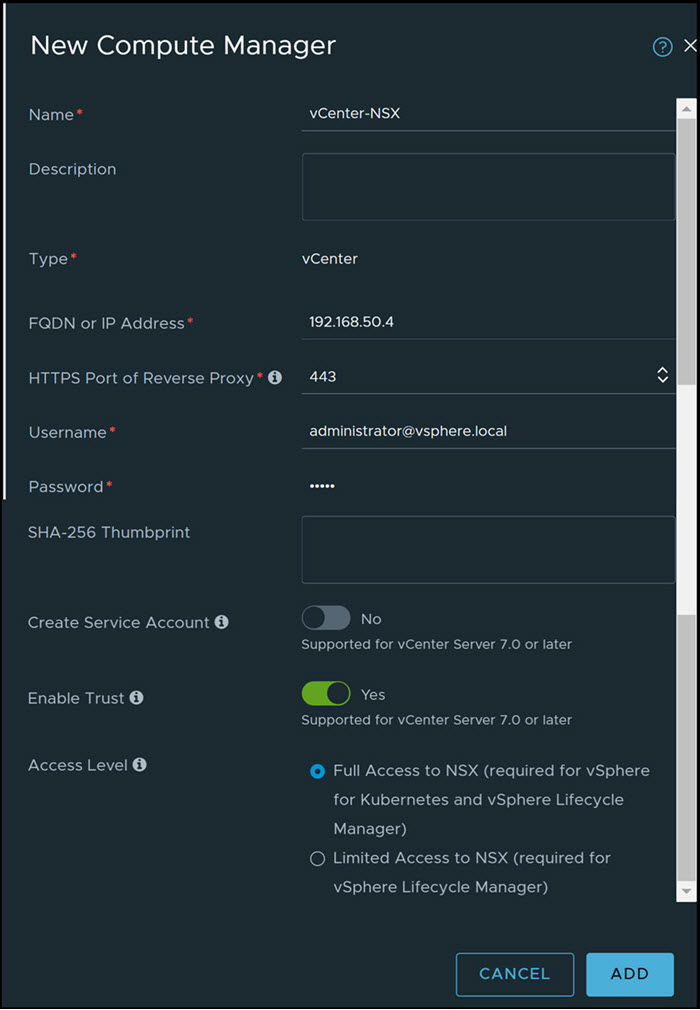
You must add vCenter Server as a compute manager on NSX-T to view all the vCenter Server host and cluster inventory. You can then leverage the available inventory to prepare ESXi hosts and clusters for NSX Security.
-
From your browser, log in to the NSX Manager appliance at https://<nsx-manager-ip-address> using the admin credentials.
- Register NSX-T with vCenter Server from the . Add the vCenter Server as a compute manager.
- Validate NSX-T registration in the vCenter Server from the page. Click Refresh and view the connection status.

After the vCenter Server registration is successful, you can view the configured vCenter Server host cluster inventory from the NSX Manager User Interface (UI). On the NSX Manager UI, go to to view the inventory.
You can configure multiple vCenter Servers from the NSX Manager UI following these same steps for each of the vCenter Server.
2: Prepare the vCenter Cluster ( ESXi Hosts) for the NSX Distributed Security
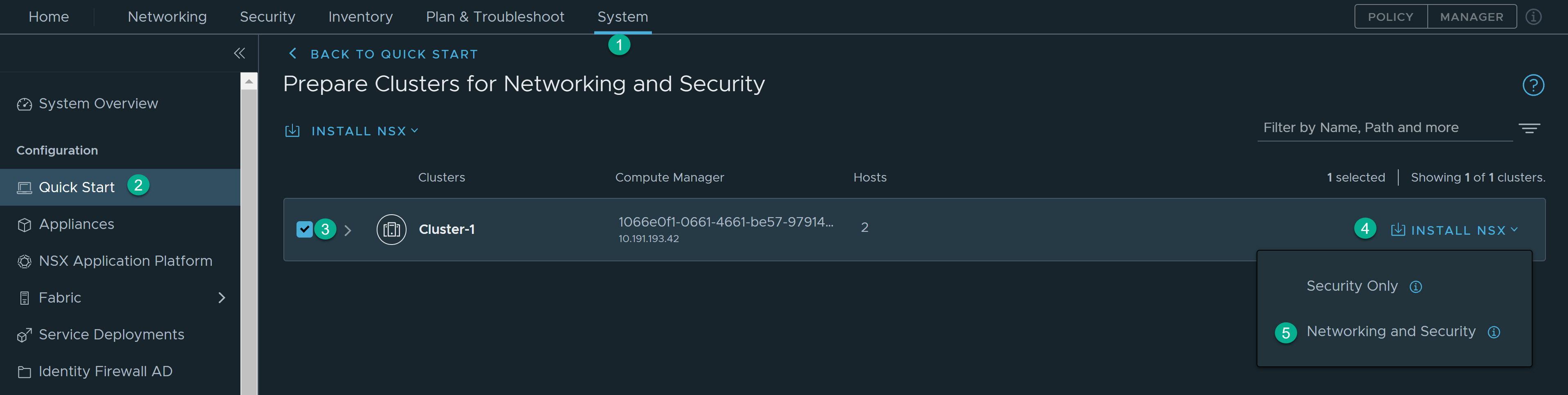
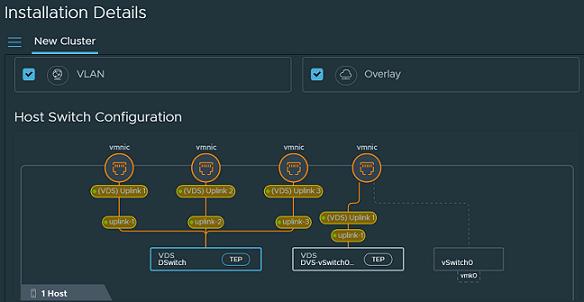
NSX Distributed Security involves preparing vCenter Server compute cluster of NSX-T. NSX-T supports two host preparation modes as follows:
- Security Only - Distributed Security for VDS port groups:
- Supports security for VMs connected to the native vCenter Distributed Virtual Port Groups (DVPG).
- Supports vSphere 6.7 and vSphere 7.0 Update1 or later.
- Does not support NSX-T networking for the workload within the NSX-T prepared vCenter Server cluster.
- Workflow is supported only using the Quick Start wizard.
- Networking and Security - Distributed Security with NSX-T Networking:
- Supports NSX-T networking and distributed security for the workload within the NSX-T prepared vCenter Server cluster.
- If VLAN connected workloads need distributed security, then you must move the workload to the NSX-T VLAN segments from DVPG.
- Workflow is supported using the Quick Start wizard or manually from the menu.
Based on your environment, select the required deployment method. The NSX-T environment can have a mix of NSX Security only prepared clusters and NSX Networking and Security prepared clusters. More details on each of the deployment modes are covered later in this section.
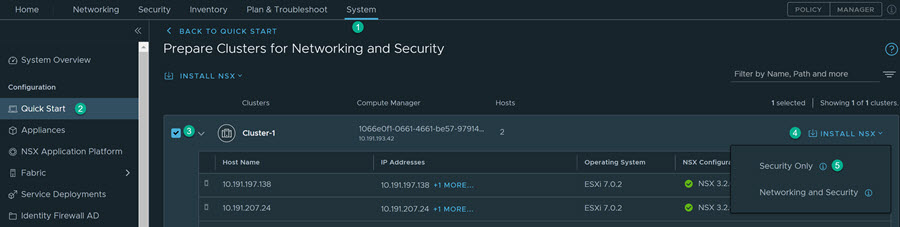
2.1: Security Only Host Preparation - Distributed Security for VDS Port Groups
After you configure the compute manager, you can prepare clusters of ESXi hosts only for distributed security. The hosts in your cluster must share VDS.
Procedure
Results
On the NSX Manager UI, go to tab to view the DVPG inventory from the vCenter Server.
On the NSX Manager UI, go to to view the virtual machine inventory from all ESXi hosts.
What to do next
You can now start configuring your policy for the workloads hosted on DVPG on the prepared vCenter Server.
2.2: Networking and Security - Distributed Security with NSX-T Networking
After you configure the compute manager, you can prepare clusters of ESXi hosts for VLAN networking and distributed security together.
Procedure
Results
On the NSX Manager UI, go to the tab to view the virtual machine inventory from all the ESXi hosts.
For more information, see NSX-T Data Center Administration Guide.
What to do next
You can now start configuring your policy for the workloads hosted on the NSX segments on the prepared vCenter Server clusters.