Network address translation (NAT) maps one IP address space to another. You can configure NAT on tier-0 and tier-1 gateways.
The following diagram shows how NAT can be configured.
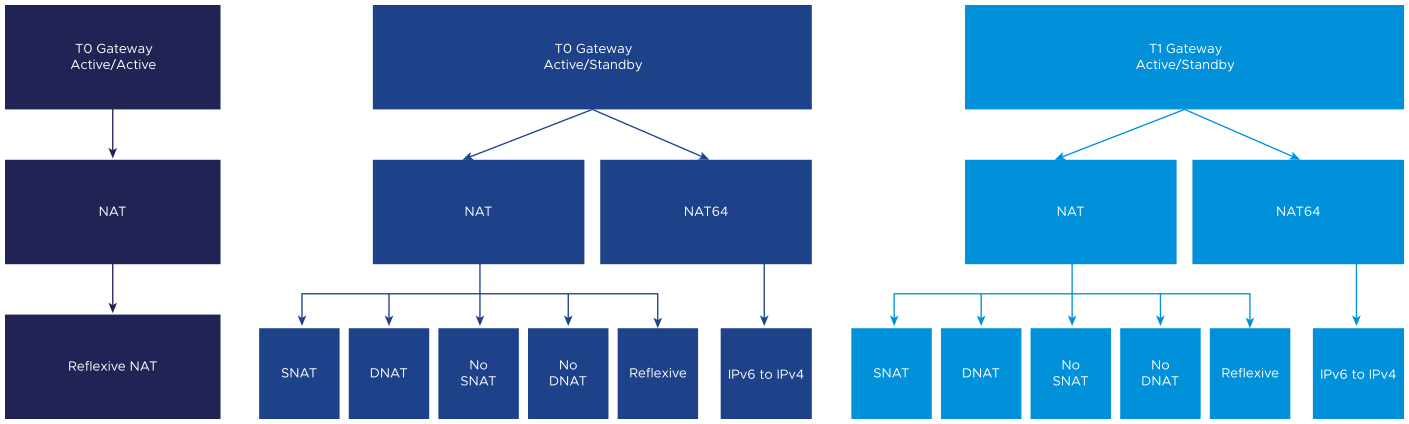
Three types of NAT are supported, in addition to NAT64.
Note: Disabling gateway firewall causes the NAT rule to drop traffic. If the gateway firewall needs to be disabled, include an Allow rule:
| Source | Destination | ACTION |
| ANY | ANY | ALLOW |
- Source NAT (SNAT) - translates a source IP address of outbound packets so that packets appear as originating from a different network. Supported on tier-0/tier-1 gateways running in active-standby mode. For one-to-one SNAT, the SNAT translated IP address is not programmed on the loopback port, and there is no forwarding entry with an SNAT translated IP as the prefix. For n-to-one SNAT, the SNAT translated IP address is programmed on the loopback port, and users will see a forwarding entry with an SNAT-translated IP address prefix. NSX SNAT is designed to be applied to traffic that egresses the NSX environment.
- Destination NAT (DNAT) - translates the destination IP address of inbound packets so that packets are delivered to a target address into another network. Supported on tier-0/tier-1 gateways running in active-standby mode. NSX DNAT is designed to be applied to traffic that ingresses the NSX environment.
- Reflexive NAT - (sometimes called stateless NAT) translates addresses passing through a routing device. Inbound packets undergo destination address rewriting, and outbound packets undergo source address rewriting. It is not keeping a session as it is stateless. Supported on tier-0 gateways running in active-active or active-standby mode, and on tier-1 gateways. Stateful NAT is not supported in active-active mode.
You can also disable SNAT or DNAT for an IP address or a range of addresses (No-SNAT/No-DNAT). If an address has multiple NAT rules, the rule with the highest priority is applied.
Note: If there is a service interface configured in a NAT rule,
translated_port will be realized on NSX Manager as
destination_port. This means that the service will be the translated port while the translated port is used to match the traffic as destination port. If there is no service configured, the port will be ignored.
If you are creating a NAT rule from a Global Manager in an NSX Federation environment, you can select site-specific IP addresses for NAT. Note the following:
- Do not click Set under Apply To if you want the default option of applying the NAT rule to all locations.
- Under Apply To, click Set and select the locations whose entities you want to apply the rule to and then select Apply NAT rule to all entities.
- Under Apply To, click Set, select a location and then select Interfaces from the Categories drop-down menu. You can select specific interfaces to which you want to apply the NAT rule.
- DNAT is not supported on a tier-1 gateway where policy-based IPSec VPN is configured.
- SNAT configured on a tier-0 gateway's external interface processes traffic from a tier-1 gateway, and from another external interface on the tier-0 gateway.
- NAT is configured on the uplinks of the tier-0/tier-1 gateways and processes traffic going through this interface. This means that tier-0 gateway NAT rules will not apply between two tier-1 gateways connected to the tier-0.
NAT Support Matrices
Configuration Fields
| Type | source-addr | dest-addr | translated-addr | translated-port | match-service |
|---|---|---|---|---|---|
| SNAT | optional | optional | must | no | optional |
| DNAT | optional | must | must | optional | optional |
| NO_SNAT | must | optional | no | no | optional |
| NO_DNAT | optional | must | no | no | optional |
| REFLEXIVE | must | no | must | no | no |
| NAT64 | optional | must | must | optional | optional |
Configuration Use Cases
| Types | 1:1 | n:n | n:m | n:1 | 1:m |
|---|---|---|---|---|---|
| SNAT | Yes | Yes | Yes | Yes | No |
| DNAT | Yes | Yes | * configurable, but not supported | Yes | * configurable, but not supported |
| NO_SNAT | - | - | - | - | - |
| NO_DNAT | - | - | - | - | - |
| REFLEXIVE | Yes | Yes | No | No | No |
| NAT64 | Yes | Yes | No | Yes | No |
NAT Traffic Flow Support on Interfaces
| Traffic Flow Support on Interfaces | DNAT | SNAT | NO_DNAT | NO_SNAT | REFLEXIVE | NAT64 |
|---|---|---|---|---|---|---|
| Uplink → Uplink | No | No | No | No | No | No |
| Uplink → Downlink | Yes | No | Yes | No | Yes | Yes |
| Uplink → Service Interface | Yes | No | Yes | No | Yes | Yes |
| Downlink → Downlink | No | No | No | No | No | No |
| Downlink → Uplink | No | Yes | NO | Yes | Yes | No |
| Downlink → Service Interface | No | No | NO | No | No | No |
| Service Interface → Service Interface | No | No | No | No | No | No |
| Service Interface → Uplink | No | Yes | No | Yes | Yes | No |
| Service Interface → Downlink | No | NO | No | No | No | No |