NSX VPC provides an isolated space for application owners to host applications and consume networking and security objects by using a self-service consumption model.
Prerequisites
- Project Admin
- Enterprise Admin
Procedure
Results
When an NSX VPC is created successfully, the system implicitly creates a gateway. However, this implicit gateway is exposed to the Project Admin in a read-only mode and is not visible to the NSX VPC users.
- Navigate to .
- Click the VPC Objects check box at the bottom of the Tier-1 Gateways page.
- Expand the gateway to view the configuration in a read-only mode.
The following naming convention is used for the implicit gateway:
_TIER1-VPC_Name
The lifecycle of this implicit gateway is managed by the system. When an NSX VPC is deleted, the implicit gateway is deleted automatically.
If you have enabled the Default Outbound NAT option, you can view the system-created default SNAT rule in the NSX VPC. Do these steps:
- Expand the Network Services section of the NSX VPC.
- Click the count next to NAT.
- Observe the default NAT rule with SNAT action for the private IPv4 block in the NSX VPC. This NAT rule is not editable. If the NSX VPC is assigned multiple private IPv4 blocks, one default NAT rule with SNAT action is created for each private IPv4 block.
For example:
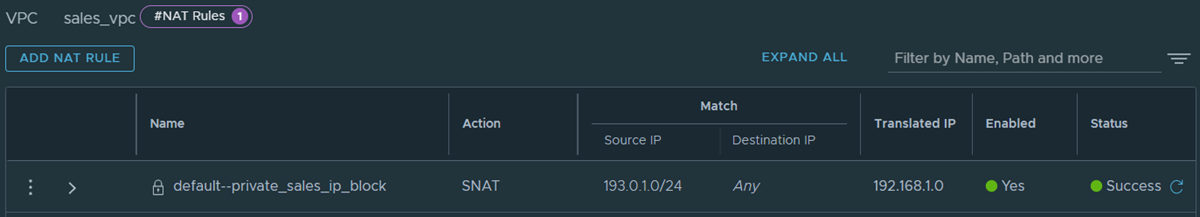
The source IP in the SNAT rule is the private IPv4 block of the NSX VPC. In this example, it is 193.0.1.0/24. The translated IP for this SNAT rule is assigned from the external IPv4 block of the NSX VPC. In this example, it is 192.168.1.0.
 , and then click
, and then click