A set of logical entities are auto-created in NSX Manager.
Log in to
NSX Manager to view the auto-created logical entities.
Important: Do not delete any of these auto-created entities except if you are manually undeploying
PCG. See
Troubleshooting PCG Undeployment for details.
System Entities
You can see the following entities under the System tab:
| Logical System Entity | How many are created? | Nomenclature | Scope |
|---|---|---|---|
| Transport Zones | Two Transport Zones are created for each Transit VPC/VNet |
|
Scope: Global |
| Edge Transport Nodes | One Edge Transport Node is created for each deployed PCG, two if deployed in high availability mode. |
|
Scope: Global |
| Edge Cluster | One Edge Cluster is created per deployed PCG, whether one or in a high availability pair. | PCG-cluster-<VPC/VNet-ID> | Scope: Global |
Inventory Entities
The following entities are available under the Inventory tab:
| Groups | Scope |
|---|---|
Two Groups named:
|
Scope: Shared across all PCGs |
| One Group created at the Transit VPC/VNet level as a parent Group for individual segments created at the Compute VPC/VNet level. cloud-<Transit VPC/VNet ID>-all-segments | Scope: shared across all Compute VPCs/VNets |
Two Groups for each Compute VPC/VNet:
|
Scope: shared across all Compute VPC/VNets |
The following Groups are created for the currently supported public cloud services:
|
Scope: Shared across all PCGs |
Note: For
PCGs deployed or linked to in the
Native Cloud Enforced Mode, all the workload VMs in the VPC/VNet become available under Virtual Machines in
NSX Manager.
Networking Entities
The following entities are created at different stages of onboarding and can be found under the Networking tab:
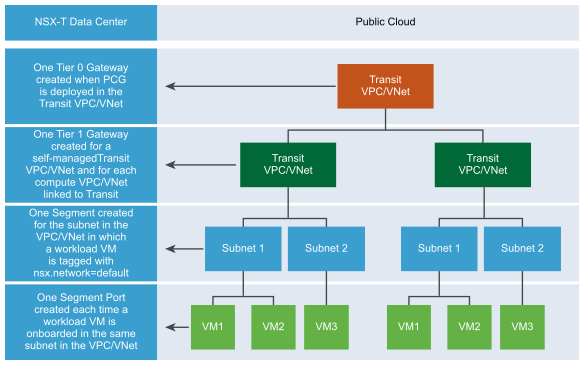
| Onboarding Task | Logical Entities Created in NSX |
|---|---|
| PCG deployed on Transit VPC/VNet |
|
| Compute VPC or VNet linked to the Transit VPC/VNet |
|
| A workload VM with the NSX agent installed on it is tagged with the "nsx.network:default" key:value in a subnet of a compute or self-managed VPC/VNet |
|
| More workload VMs are tagged in the same subnet of the Compute or self-managed VPC/VNet |
|
Forwarding Policies
The following three forwarding rules are set up for a Compute VPC/VNet, including Self-managed Transit VPC/VNet:
- Access any CIDR of the same Compute VPC over the public cloud's network (underlay)
- Route traffic pertaining to public cloud metadata services over the public cloud's network (underlay)
- Route everything not in the Compute VPC/VNet's CIDR block, or a known service, through the NSX network (overlay)
Security Entities
The following entities are available under the
Security tab:
| Logical Security Entity | How many are created? | Nomenclature | Scope |
|---|---|---|---|
| Distributed Firewall (East-West) | Two per Transit VPC/VNet:
|
|
|
| Gateway Firewall (North-South) | One per Transit VPC/VNet | cloud-<Transit VPC/VNet ID> |