Detections, also referred to as detection events or events, represent the security-relevant activity that has occurred in the network as detected by NSX Network Detection and Response. Detections enable threat triage and investigation by presenting analysis of all threat events regardless of event type within the NSX environment.
When new detection data is received by the NSX Network Detection and Response system, the data is compared with existing detection events to determine if the new detection can be aggregated with an existing detection event. For details about how detections are aggregated, see Aggregation of Detections.
Detection events can be correlated together to form a campaign. If a detection event has no correlation with any other detection, it will not be included in any campaign.
View the Unified Event List
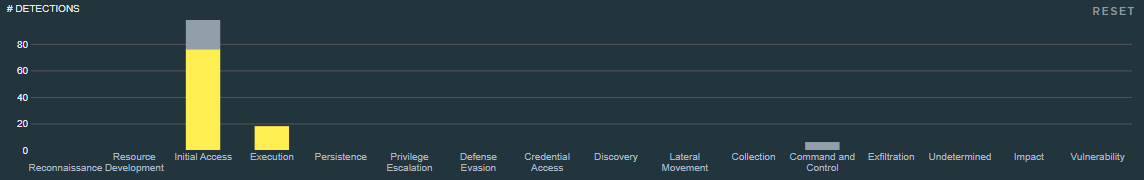
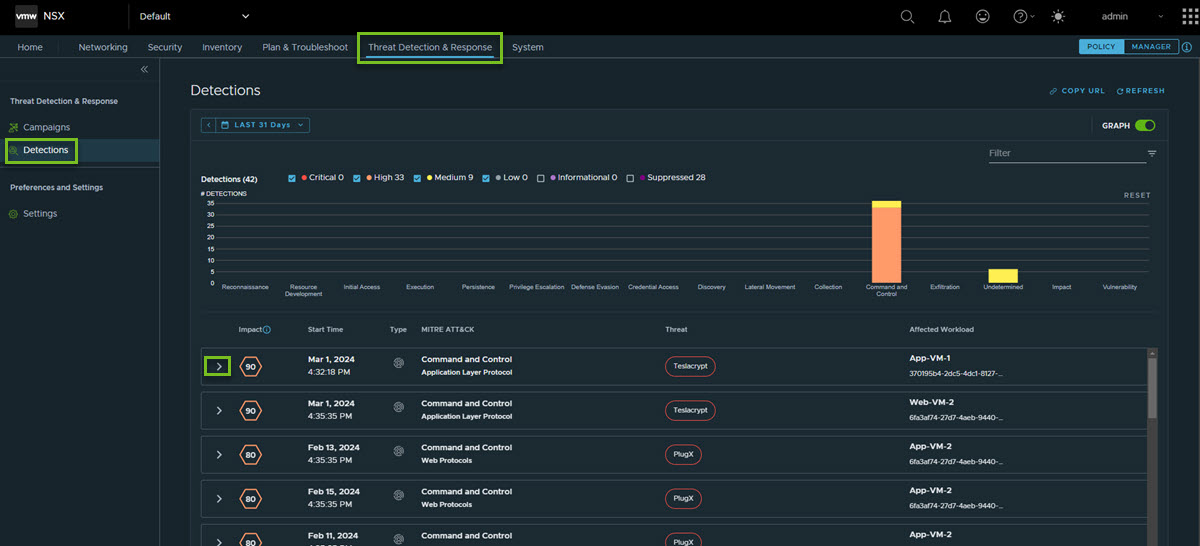
To see all the detection events generated by NSX Network Detection and Response, navigate to the page. This page provides a histogram at the top of the page and a list below the histogram. The list is referred to as the unified events list and displays all the detection events. Each row in the list represents one detection event.
- Click Copy URL at the top right of the page to copy the link address with the filters that are currently applied.
Filter the Unified Event List
| Method | Details |
|---|---|
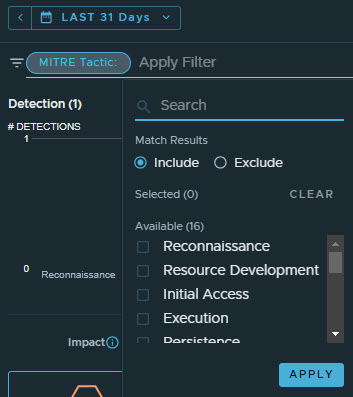
| Check boxes | Click the check boxes above the histogram to filter the unified event list based on the detection impact score of the detection. For more information about detection impact scores, see About Detection Impact Scores.
|
| Histogram | Click the histogram bars to filter the unified event list based on the MITRE ATT&CK tactic identified in the detection.
|
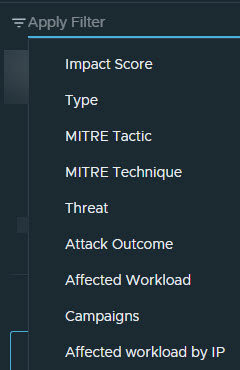
| Filter field | Click the filter field for more powerful filtering options:
|
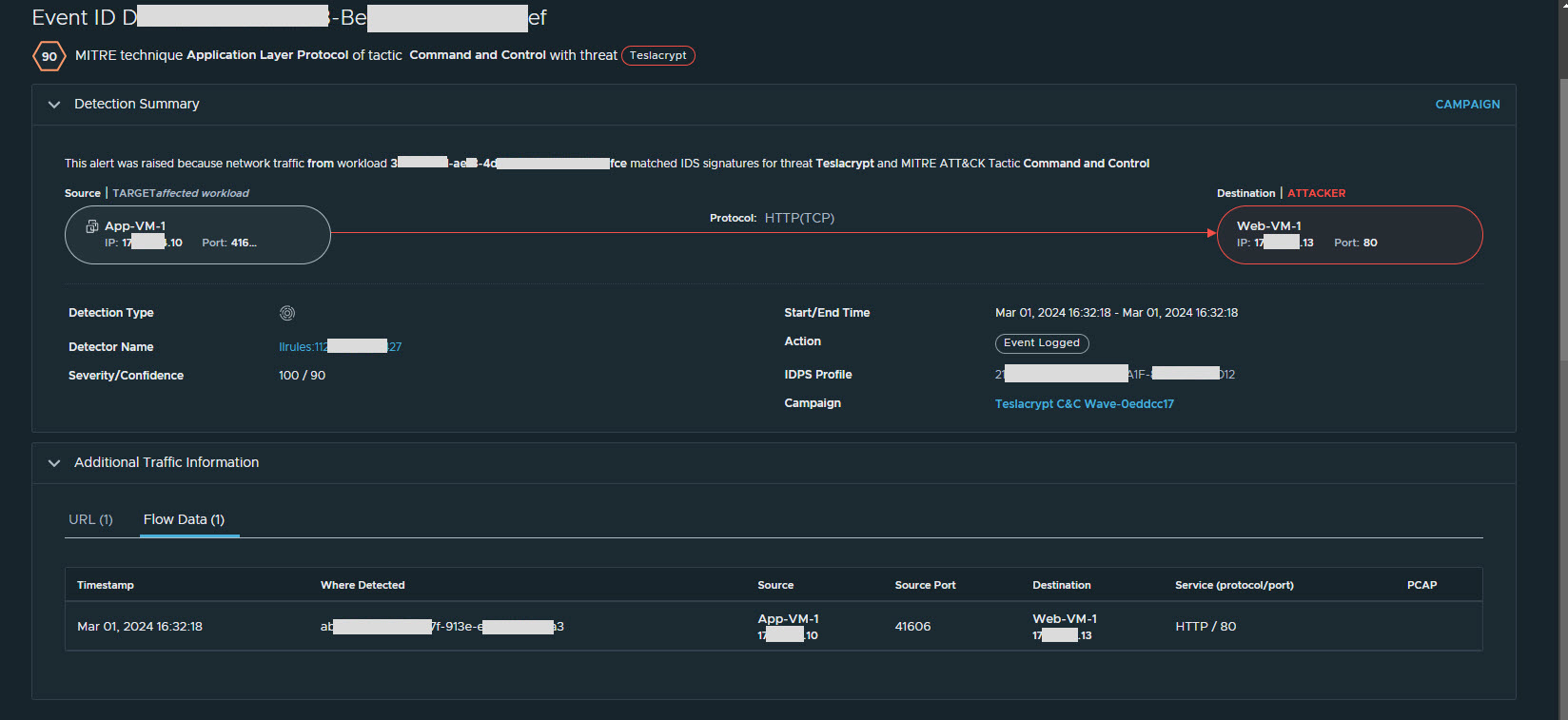
View a Detection Event Summary
Expand the detection row and click More Details to view the detection summary.
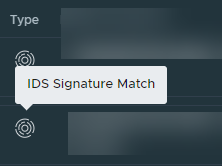
Detection Type
You can view the detection type icon in the Type column. Hover over to view the detection type.
Export and Download Packet Capture Files
Malware Behavior Overview
The Malware Behavior section provides information from the dynamic analysis that was performed on the malicious software instance that is related to the event.
Click View Reports to access detailed in-depth technical information on what the malware does, how it operates, and what kind of a risk it poses. For more information on the displayed information, see Analysis Report Details.