The Detection Impact Score in NSX Network Detection and Response is a metric that is a combination of the severity or "badness" of the threat, and confidence in the accuracy of the detection. A score ranges from 0-100, with 100 being the most dangerous detection. The impact score helps you prioritize and triage the detection. The following levels of impact are used:
| Impact Level | Impact Score |
|---|---|
| Critical | 95 to 100 |
| High | 75 to 94 |
| Medium | 50 to 74 |
| Low | 25 to 49 |
| Informational | 1 to 24 |
| Suppressed | 0 |
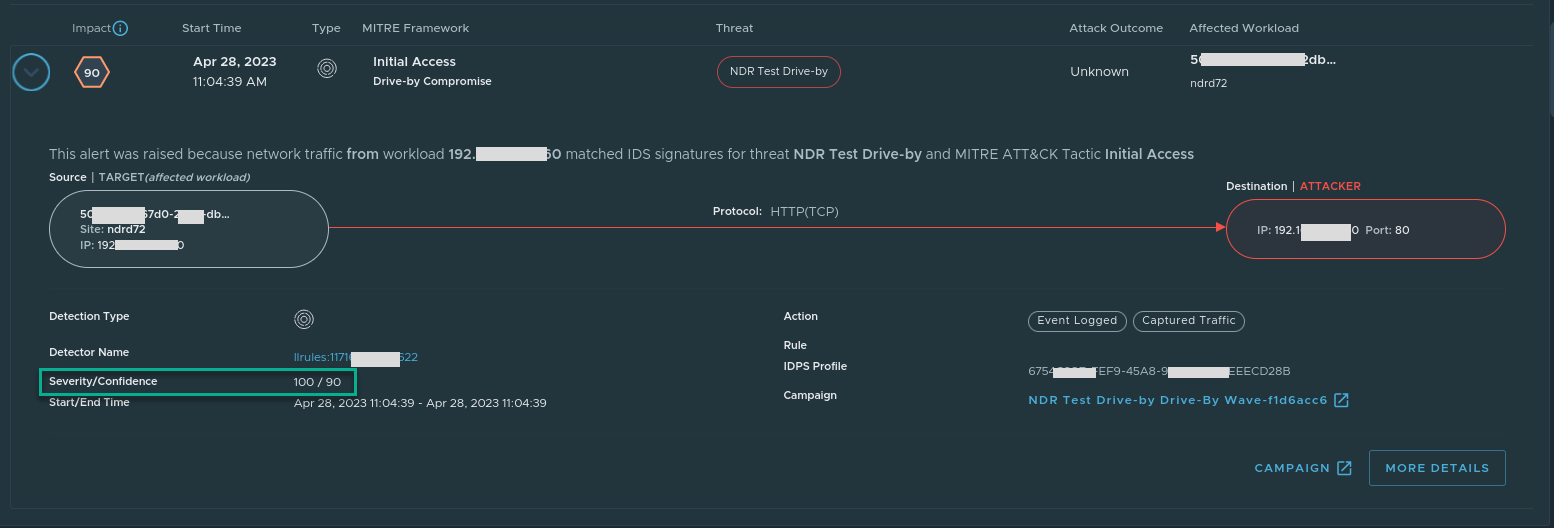
Severity
Severity is also an integer between 0 and 100. Severity indicates how bad the detection is, assuming:
- It is not a false positive
- It is not misclassified
The severity of a detection is largely determined by the threat it is detecting. In almost all cases, two detections that have the same threat will also have the same severity. Thus:
- A serious threat such as a compromised workload performing Command and Control will have a high severity value.
- A less serious threat such as a workload performing a port scan will have a low severity value.
Confidence
Confidence is also an integer between 0 and 100. Confidence indicates the level of confidence in the accuracy of a detection.
- A high accuracy detection such as one where a highly specific network signature detects known malicious behavior will have a high confidence value.
- A low accuracy detection such as one identifying potential exfiltration traffic will have a low confidence value.
The confidence of a detection is largely determined by how the threat was detected. In particular, each IDS or NTA detector has an associated confidence score that is used as a baseline for the confidence of the detection event.
On top of this baseline, the confidence may be modified by additional factors:
- Informational event promotion may increase the confidence of a detection.
- Repetition of the behavior within the detection event can lead to a small increase in confidence:
- Confidence level is increased if the activity is seen more than once.
- Confidence level is increased if the activity looks periodic (meaning the activity occurs on a regular repetitive schedule).
- NTA detectors that use anomaly detection techniques can provide different confidence values depending on how anomalous the behavior looks.
You can view Severity and Confidence on the Detection Summary page.
Informational Events
Detection events with an impact score from 1 to 24 are classified with the Informational impact level. This means that the detected activity is not essentially malicious. However, the NSX Network Detection and Response contextual scoring logic may promote some informational detections to a higher impact score, removing the Informational flag.
Suppressed Events
Suppressed events are detections with an impact score of 0. A suppressed event does not represent a threat.
There are situations where a detection may have a score of 0:
- The detection was raised by an IDS signature that is deactivated by the NSX Network Detection and Response system because it is false positive prone or not useful. This can happen if, for example, an installation has not yet updated its IDS signature bundle to the version that removes the bad signature.
Impact Calculation
The impact score of a detection event is calculated from:
- Confidence
- Severity
- Informational events
Impact is initially Confidence * Severity / 100
- For informational events, the impact score is capped at 24
- For non-informational events, the minimum impact score is 25