Projects help you to isolate networking and security configurations across tenants in a single NSX deployment.
Prerequisites
You must be assigned the Enterprise Admin role.
Procedure
What to do next
If you have turned on the Organize NSX Portgroups in vCenter folders toggle for the project, do these steps:
- Check the status of the project. When folders are created successfully in VMware vCenter, the status is a Success. This status represents the overall or consolidated status of all the folders that were created by NSX in VMware vCenter when this project was created.
If the overall status next to the toggle is displayed as Failed, check the error details to learn the reason for the failure.
Examples of failure situations:- If the VMware vCenter server is down when the folders are being realized, the folder creation can fail. NSX will not be able to communicate with VMware vCenter. In this case, the overall folder status for the project is Failed. NSX will attempt to create the folders again at predefined intervals until the status changes to Success.
- If the
cm-inventoryservice on the NSX Manager node is down, the folder creation can fail.NSX Manager uses this service to retrieve information about the VDS or hosts dynamically from VMware vCenter. When the group members of this service are down, an alarm belonging to the Clustering feature is displayed in NSX Manager.
- Log in to the vSphere Client, open the Inventory pane, and verify that the project and VDS folders are created.
For example, assume that you have added two projects named Project-1, Project-2, and Project-3 in your NSX deployment, and the Organize NSX Portgroups in vCenter folders toggle is turned on for these projects. The following screen capture shows that a root folder called NSX Managed Folders is created inside the Datacenter object. The Project folders and folders are created inside the root folder.
Each of these project folders will have folders inside them for each of their VPCs and Segments. Each VPC will then have sub-folders for each subnet. Inside Segment and Subnet folders user can find all the NSX port groups mapped to this Segment/Subnet.Note: A single NSX Segment or Subnet creates one NSX port group per VDS, all with the same name. All those port groups are regrouped under the folder regrouping the Segment or Subnet.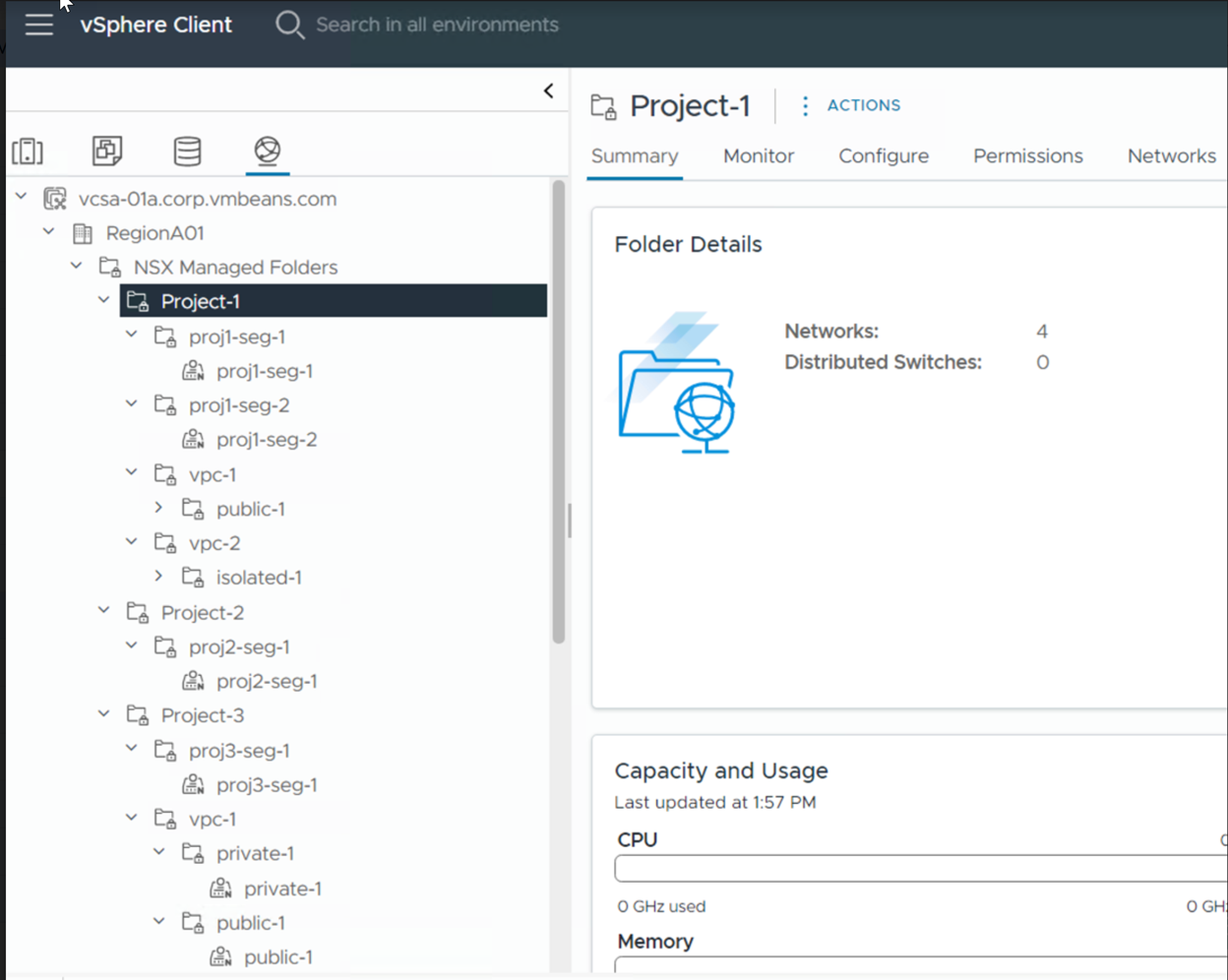
Later, when you add segments in the projects, or add NSX VPCs in the projects, or add subnets in the VPCs, they get organized inside folders in VMware vCenter.
 , and then click
, and then click