TPM-based attestation is a process to detect gateway tampering for file systems.
With the TPM-based attestation configured, VMware Pulse IoT Center triggers an alert whenever a gateway is tampered.
- Boot Attestation
- Runtime Attestation
What is Boot Attestation
Boot attestation is a secure mechanism to verify the integrity of an IoT gateway during boot time. Boot attestation enables the detection of gateway file tampering every time the gateway boots. When a tampering is detected, VMware Pulse IoT Center raises an alert.
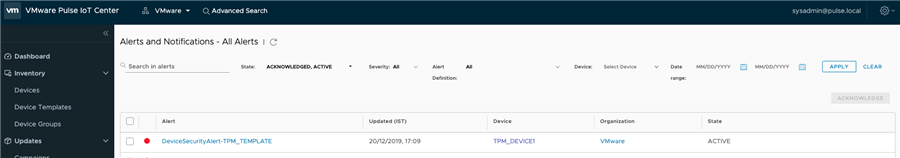
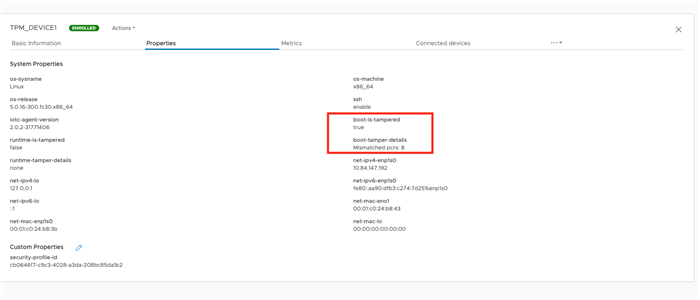
The cause of failure is updated in the gateway properties.
What is Runtime Attestation
Runtime attestation is a secure mechanism to verify the integrity of an IoT gateway during run time. The runtime attestation check occurs every 3600 seconds. When a tampering is detected, VMware Pulse IoT Center raises an alert.
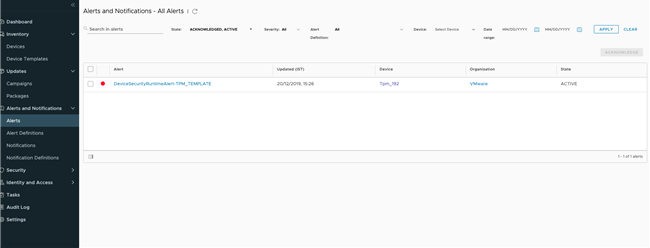
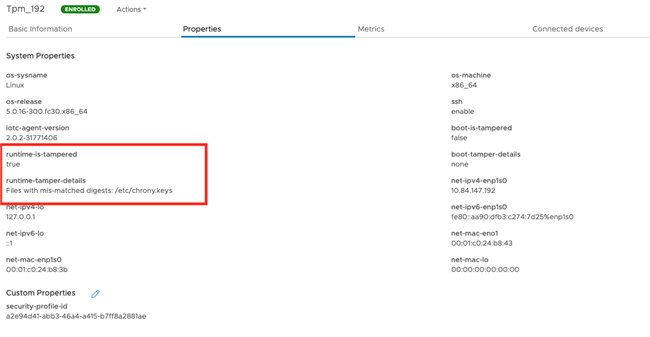
The cause of failure is updated in the device properties.
To configure the runtime attestation, you must enable Integrity Measurement Architecture (IMA) on your gateway.
What Is IMA
Integrity Measurement Architecture (IMA) is an open source trusted computing component. IMA, when anchored in a hardware Trusted Platform Module (TPM), maintains a runtime measurement list with an aggregate integrity value of the list. This ensures that the measurement cannot be tampered without it being detected. Hence, on a trusted-boot system, the IMA can be used to attest to the system's runtime integrity.