VMware supports third-party firewalls that can be used as VNF to pass traffic through Edges.
Choose the third-party firewall and configure the settings accordingly. You may need to configure additional settings in the third-party firewall as well. Refer to the deployment guides of the corresponding third-party firewall for the additional configurations.
For the VNF Types Check Point Firewall and Fortinet Firewall configure the VNF Image by using the System Property edge.vnf.extraImageInfos. You must be an Operator user to configure the system property. If you do not have the Operator role access, contact your Operator to configure the VNF Image.
Note: You must provide the correct checksum value in the system property. The Edge computes the checksum of the downloaded VNF image and compares the value with the one available in the system property. The Edge deploys the VNF only when both the checksum values are the same.
Procedure
- In the Enterprise portal, click .
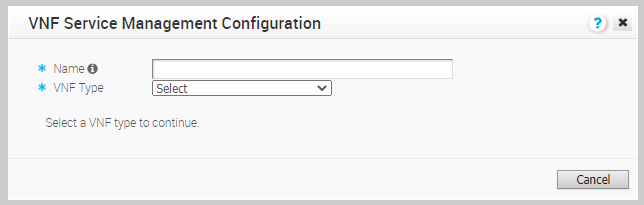
- In the Services page, scroll down to the VNFs section and click New.
- In the VNF Service Management Configuration window, enter a descriptive name for the security VNF service and select a VNF Type from the drop-down list.
- Configure the settings based on the selected VNF Type.
- For the VNF Type Palo Alto Networks Firewall, configure the following:
- Primary Panorama IP Address – Enter the primary IP address of the Panorama server.
- Secondary Panorama IP Address – Enter the secondary IP address of the Panorama server.
- Panorama Auth Key – Enter the authentication key configured on the Panorama server. VNF uses the Auth Key to login and communicate with Panorama.
- Click Save Changes.
After configuring Palo Alto Networks as VNF Type, define the VNF licenses. These licenses will be applied to one or more VNF configured Edges.
- In the Services page, scroll down to the VNF Licenses section and click New.
- In the VNF License Configuration window, configure the following:

- Name – Enter a descriptive name for the VNF license.
- VNF Type – Select the VNF type from the drop-down list. Currently, Palo Alto Networks Firewall is the only available option.
- License Server API Key – Enter the license key from your Palo Alto Networks account. The SD-WAN Orchestrator uses this key to communicate with the Palo Alto Networks license server.
- Auth Code – Enter the authorization code purchased from Palo Alto Networks.
- Click Test to validate the configuration.
- Click Save Changes.
You can apply the VNF licenses while configuring
Palo Alto Networks Firewall as a VNF Type on Edges.
Note: If you want to remove the deployment of
Palo Alto Networks Firewall configuration from a VNF type, ensure that you have deactivated the
VNF License of Palo Alto Networks before removing the configuration.
- For the VNF Type Check Point Firewall, configure the following:

- Primary Check Point Mgmt Server IP – Enter the Check Point Smart Console IP address that will connect to the Check Point Firewall.
- SIC Key for Mgmt Server Access – Enter the password used to register the VNF to the Check Point Smart Console.
- Admin Password – Enter the administrator password.
- VNF Image Location – Enter the image location from where the SD-WAN Orchestrator will download the VNF image.
- Image Version – Select a version of the Check Point VNF image from the drop-down list. The image version is derived from the system property edge.vnf.extraImageInfos.
- File Checksum Type – Specifies the method used to validate the VNF image and is automatically populated after you select an image version.
- File Checksum – Specifies the checksum used to validate the VNF image and is automatically populated after you select an image version. The checksum value is derived from the system property edge.vnf.extraImageInfos.
- Download Type – Choose the type of the image. For https, enter the username and password. For s3, enter the AccessKeyid, SecretAccessKey, and choose the Region.
- Click Save Changes.
- For the VNF Type Fortinet Firewall, configure the following:

- Fortinet Mgmt Server IP – Enter the IP address of the FortiManager to connect to the FortiGate.
- Fortimanager Serial Number – Enter the serial number of FortiManager.
- Registration Password – Enter the password used to register the VNF to the FortiManager.
- VNF Image Location – Enter the image location from where the SD-WAN Orchestrator will download the VNF image.
- Image Version – Select a version of the Fortinet VNF image from the drop-down list. The following options are available: 6.4.0, 6.2.4, 6.0.5, 6.2.0. The image version is derived from the system property edge.vnf.extraImageInfos.
- File Checksum Type – Specifies the method used to validate the VNF image and is automatically populated after you choose an image version.
- File Checksum – Specifies the checksum used to validate the VNF image and is automatically populated after you select an image version. The checksum value is derived from the system property edge.vnf.extraImageInfos.
- Download Type – Choose the type of the image. For https, enter the username and password. For s3, AccessKeyid, SecretAccessKey, and choose the Region.
- Click Save Changes.
Results
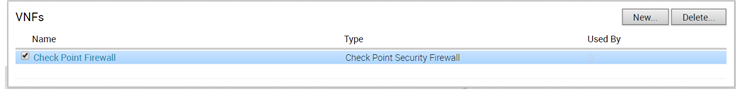
The VNFs section displays the created VNF services. The following image shows an example of VNF Type as Check Point Firewall.
What to do next
You can configure security VNF for an Edge to direct the traffic through the VNF management services. See