When creating Edge-to-Edge IPSec tunnels, you can modify the security policy configuration settings at the Customer Configuration level.
Procedure
- In the Operator portal, navigate to Manage Customers.
- Select a customer and click Actions > Modify or click the link to the customer.
- In the Enterprise portal, click Configure > Customers. The Customer Configuration page appears.
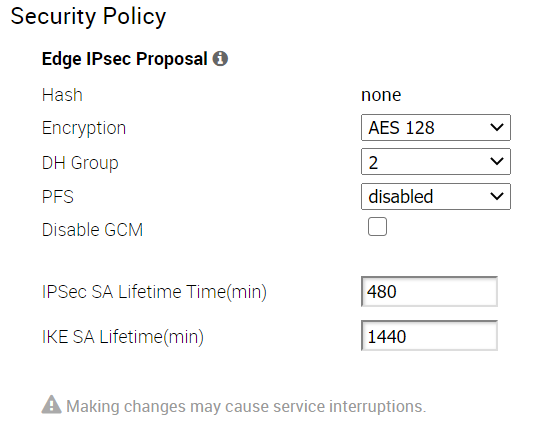
- In the Security Policy area, you can configure the following security settings:
- Hash - By default, there is no authentication algorithm configured for the VPN header. When the Galois/Counter Mode (GCM) is disabled, you can select one of the following as the authentication algorithm for the VPN header, from the drop-down list that appears:
- SHA 1
- SHA 256
- SHA 384
- SHA 512
- Encryption - AES 128-Galois/Counter Mode (GCM), AES 256-GCM, AES 128-Cipher Block Chaining (CBC) and AES 256-CBC are the encryption algorithms modes used to provide confidentiality. Select either AES 128 or AES 256 as the AES algorithms key size to encrypt data. The default encryption algorithm mode is AES 128-GCM, when the Disable GCM checkbox is not selected.
- DH Group - Select the Diffie-Hellman (DH) Group algorithm to be used when exchanging a pre-shared key. The DH Group sets the strength of the algorithm in bits. The supported DH Groups are 2, 5, 14, 15, and 16. It is recommended to use DH Group 14.
- PFS - Select the Perfect Forward Secrecy (PFS) level for additional security. The supported PFS levels are 2, 5, 14, 15, and 16. By default, PFS is disabled.
- Disable GCM - By default, AES 128-GCM is enabled. If needed, select the checkbox to disable this mode. Disabling the checkbox will enable AES 128-CBC mode.
- IPsec SA Lifetime - Time when Internet Security Protocol (IPSec) rekeying is initiated for Edges. The minimum IPsec life time is 3 minutes and maximum is 480 minutes. The default value is 480 minutes.
- IKE SA Lifetime - Time when Internet Key Exchange (IKE) rekeying is initiated for Edges. The minimum IKE life time is 10 minutes and maximum is 1440 minutes. The default value is 1440 minutes.
Note: It is not recommended to configure low life time values for IPsec (less than 10 minutes) and IKE (less than 30 minutes) as it can cause traffic interruption in some deployments due to rekeys. The low life time values are for debugging purposes only.
- Hash - By default, there is no authentication algorithm configured for the VPN header. When the Galois/Counter Mode (GCM) is disabled, you can select one of the following as the authentication algorithm for the VPN header, from the drop-down list that appears:
- After configuring the settings, click Save Changes.
Note: When you modify the security settings, the changes may cause interruptions to the current services. In addition, these settings may reduce overall throughput and increase the time required for VCMP tunnel setup, which may impact branch to branch dynamic tunnel setup times and recovery from Edge failure in a cluster.