When you have assigned a profile to an Edge, the Edge automatically inherits the cloud security service (CSS) and attributes configured in the profile. You can override the settings to select a different cloud security provider or modify the attributes for each Edge.
To override the CSS configuration for a specific Edge, perform the following steps:
- In the Enterprise portal, click .
- Select an Edge you want to override CSS settings and click the icon under the Device column. The Device Settings page for the selected Edge appears.
- In the Cloud Security Service area, the CSS parameters of the associated profile are displayed. Select Enable Edge Override to select a different CSS or to modify the attributes inherited from the profile associated with the Edge. For more information on the attributes, see Configure Cloud Security Services for Profiles.
- Click Save Changes in the Edges window to save the modified settings.
Note: For CSS of type Zscaler and Generic, you must create VPN credentials. For Symantec CSS type, the VPN credentials are not needed.
Manual Zscaler CSS Provider Configuration for Edges
At the Edge level, for a selected manual Zscaler CSS provider, you can override the settings inherited from the profile and can configure additional parameters manually based on the tunneling protocol selected for tunnel establishment.
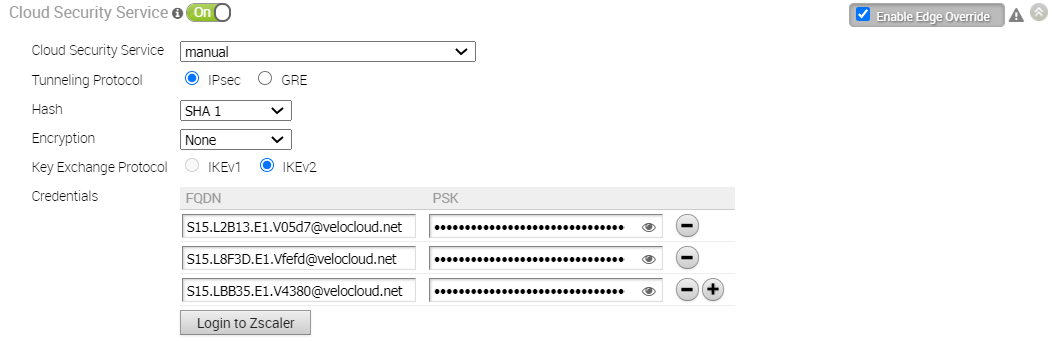
If you choose to configure a GRE tunnel manually, then you must configure GRE tunnel parameters manually for the selected WAN interface to be used as source by the GRE tunnel, by following the steps below.
- Click Add Tunnel.

- In the Add Tunnel window appears, configure the following GRE tunnel parameters, and click OK.
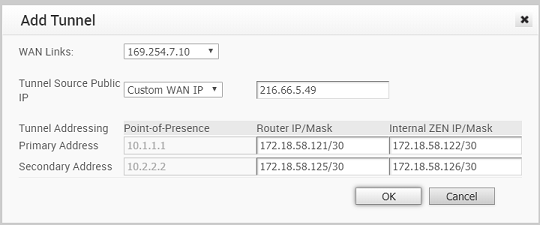
Option Description WAN Links Select the WAN interface to be used as source by the GRE tunnel. Tunnel Source Public IP Choose the IP address to be used as a public IP address by the Tunnel. You can either choose the WAN Link IP or Custom WAN IP. If you choose Custom WAN IP, enter the IP address to be used as public IP. Source public IPs must be different for each segment when Cloud Security Service (CSS) is configured on multiple segments. Primary Point-of-Presence Enter the primary Public IP address of the Zscaler Datacenter. Secondary Point-of-Presence Enter the secondary Public IP address of the Zscaler Datacenter. Primary Router IP/Mask Enter the primary IP address of Router. Secondary Router IP/Mask Enter the secondary IP address of Router. Primary ZEN IP/Mask Enter the primary IP address of Internal Zscaler Public Service Edge. Secondary ZEN IP/Mask Enter the secondary IP address of Internal Zscaler Public Service Edge. Note:- The Router IP/Mask and ZEN IP/Mask are provided by Zscaler.
- Only one Zscaler cloud and domain are supported per Enterprise.
- Only one CSS with GRE is allowed per Edge. An Edge cannot have more than one segment with Zscaler GRE automation enabled.
- Scale Limitations:
- GRE-WAN: Edge supports maximum of 4 public WAN links for a Non SD-WAN Destination (NSD) and on each link, it can have up to 2 tunnels (primary/secondary) per NSD. So, for each NSD, you can have maximum of 8 tunnels and 8 BGP connections from one Edge.
- GRE-LAN: Edge supports 1 link to Transit Gateway (TGW), and it can have up to 2 tunnels (primary/secondary) per TGW. So, for each TGW, you can have maximum of 2 tunnels and 4 BGP connections from one Edge (2 BGP sessions per tunnel).
Automated Zscaler CSS Provider Configuration for Edges
IPsec/GRE Tunnel Automation
- In the Enterprise portal, click .
- Select an Edge you want to establish automatic tunnels.
- Click the icon under the Device column. The Device Settings page for the selected Edge appears.
- In the Cloud Security Service section, select Enable Edge Override.
- From the Cloud Security Service drop-down menu, select an automated CSS provider and click Save Changes.
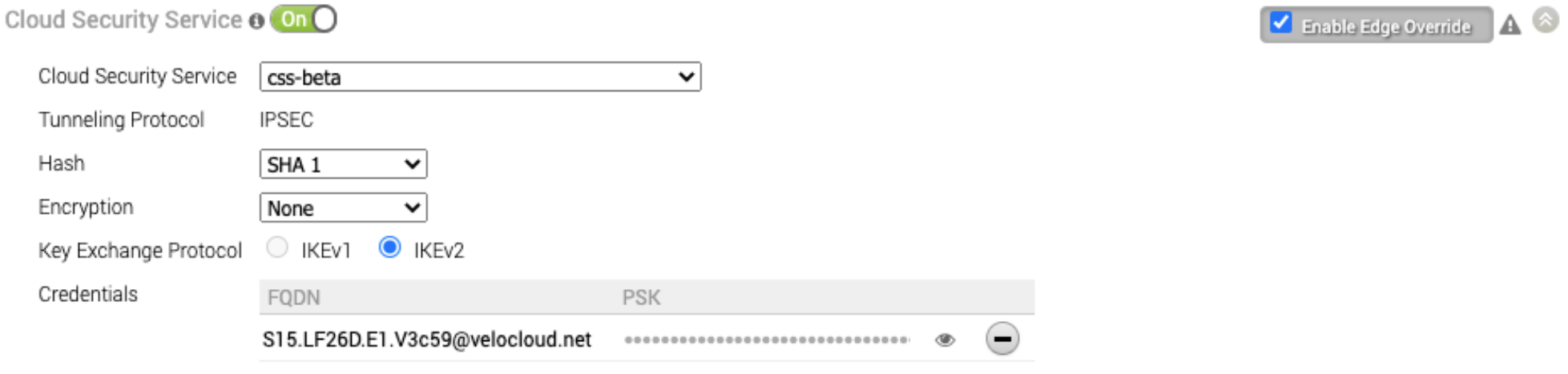
The automation will create a tunnel in the segment for each Edge's public WAN link with a valid IPv4 address. In a multi-WAN link deployment, only one of the WAN Links will be utilized for sending user data packets. The Edge choses the WAN link with the best Quality of Service (QoS) score using bandwidth, jitter, loss, and latency as criteria. Location is automatically created after a tunnel is established. You can view the details of tunnel establishment and WAN links in the Cloud Security Service section
Note: After automatic tunnel establishment, changing to another CSS provider from an Automated Zscaler service provider is not allowed on a Segment. For the selected Edge on a segment, you must explicitly deactivate Cloud Security service and then reactivate CSS if you want to change to a new CSS provider from an Automated Zscaler service provider.
Zscaler Location/Sub-Location Configuration
- you check that the tunnel is established from the selected Edge and Location is automatically created. You will not be allowed to create a Sub-location if the VPN credentials or GRE options are not set up for the Edge. Before configuring Sub-locations, ensure you understand about Sub-location and their limitations. See https://help.zscaler.com/zia/about-sub-locations.
- you select the same Cloud Subscription that you used to create the Automatic CSS.
- In the Enterprise portal, click .
- Select an Edge and click the icon under the Device column. The Device Settings page for the selected Edge appears.
- Go to the Zscaler section and turn on the toggle button.

- From the Cloud Subscription drop-down menu, select the same Cloud Subscription that you used to create the Automatic CSS. The Cloud Name associated to the selected Cloud Subscription automatically appears.
Note: Cloud Subscription must have same Cloud name and Domain name as CSS.Note: If you want to change provider for "Cloud Subscription", you must first remove the "Location" by deactivating CSS and Zscaler, and then perform the creation steps with the new provider.
In the Location table, clicking View under the Action Details column displays the actual values for the configuration fetched from Zscaler, if present. If you want to configure the Gateway options and Bandwidth controls for the Location, click the Edit button under Gateway Options. For more information, see Configure Zscaler Gateway Options and Bandwidth Control.
- To create a Sub-location, in the Sub-Locations table, click the
 icon under the Action column.
icon under the Action column.
- In the Sub-Location Name textbox, enter a unique name for the Sub-location. The Sub-location name should be unique across all segments for the Edge. The name can contain alphanumeric with a maximum word length of 32 characters.
- From the LAN Networks drop-down menu, select a VLAN configured for the Edge. The Subnet for the selected LAN network will be populated automatically.
Note: For a selected Edge, Sub-locations should not have overlapping Subnet IPs.
- Click Save Changes.
 Note: After you create at least one Sub-location in the Orchestrator, an “Other” Sub-location is automatically created in the Zscaler side, and it appears in the Orchestrator UI. You can also configure the “Other” Sub-location’s Gateway options by clicking the Edit button under Gateway Options in the Sub-Locations table. For more information, see Configure Zscaler Gateway Options and Bandwidth Control.
Note: After you create at least one Sub-location in the Orchestrator, an “Other” Sub-location is automatically created in the Zscaler side, and it appears in the Orchestrator UI. You can also configure the “Other” Sub-location’s Gateway options by clicking the Edit button under Gateway Options in the Sub-Locations table. For more information, see Configure Zscaler Gateway Options and Bandwidth Control. - After creating a Sub-location, you can update the Sub-location configurations from the same Orchestrator page. Once you click Save Changes, the Sub-location configurations on the Zscaler side will be updated automatically.
- To delete a Sub-location, click the
 icon under the Action column.
Note: When the last Sub-location is deleted from the table, the "other" Sub-location will also be deleted automatically.
icon under the Action column.
Note: When the last Sub-location is deleted from the table, the "other" Sub-location will also be deleted automatically.
Configure Zscaler Gateway Options and Bandwidth Control
To configure Gateway options and Bandwidth controls for the Location and Sub-location, click the Edit button under Gateway Options, in the respective table.

Configure the Gateway options and Bandwidth controls for the Location and Sub-location, as needed, and click Save Changes.
| Option | Description |
|---|---|
| Gateway Options for Location/Sub-Location | |
| Use XFF from Client Request | Enable this option if the location uses proxy chaining to forward traffic to the Zscaler service, and you want the service to discover the client IP address from the X-Forwarded-For (XFF) headers that your on-premises proxy server inserts in outbound HTTP requests. The XFF header identifies the client IP address, which can be leveraged by the service to identify the client’s sub-location. Using the XFF headers, the service can apply the appropriate sub-location policy to the transaction, and if Enable IP Surrogate is turned on for the location or sub-location, the appropriate user policy is applied to the transaction. When the service forwards the traffic to its destination, it will remove the original XFF header and replace it with an XFF header that contains the IP address of the client gateway (the organization’s public IP address), ensuring that an organization's internal IP addresses are never exposed to externally.
Note: This Gateway option is only configurable for Parent location.
|
| Enable Caution | If you have not enabled Authentication, you can enable this feature to display a caution notification to unauthenticated users. |
| Enable AUP | If you have not enabled Authentication, you can enable this feature to display an Acceptable Use Policy (AUP) for unauthenticated traffic and require users to accept it. If you enable this feature:
|
| Enforce Firewall Control | Select to enable the service's firewall control.
Note: Before enabling this option, user must ensure if its Zscaler account has subscription for "Firewall Basic".
|
| Enable IPS Control | If you have enabled Enforce Firewall Control, select this to enable the service's IPS controls.
Note: Before enabling this option, user must ensure if its Zscaler account has subscription for "Firewall Basic" and "Firewall Cloud IPS".
|
| Authentication | Enable to require users from the Location or Sub-location to authenticate to the service. |
| IP Surrogate | If you enabled Authentication, select this option if you want to map users to device IP addresses. |
| Idle Time for Dissociation | If you enabled IP Surrogate, specify how long after a completed transaction, the service retains the IP address-to-user mapping. You can specify the Idle Time for Dissociation in Mins (default), or Hours, or Days.
|
| Surrogate IP for Known Browsers | Enable to use the existing IP address-to-user mapping (acquired from the surrogate IP) to authenticate users sending traffic from known browsers. |
| Refresh Time for re-validation of Surrogacy | If you enabled Surrogate IP for Known Browsers, specify the length of time that the Zscaler service can use IP address-to-user mapping for authenticating users sending traffic from known browsers. After the defined period of time elapses, the service will refresh and revalidate the existing IP-to-user mapping so that it can continue to use the mapping for authenticating users on browsers. You can specify the Refresh Time for re-validation of Surrogacy in minutes (default), or hours, or days.
|
| Bandwidth Control Options for Location | |
| Bandwidth Control | Enable to enforce bandwidth controls for the location. If enabled, specify the maximum bandwidth limits for Download (Mbps) and Upload (Mbps). All sub-locations will share the bandwidth limits assigned to this location. |
| Download | If you enabled Bandwidth Control, specify the maximum bandwidth limits for Download in Mbps. The allowable range is from 0.1 through 99999. |
| Upload | If you enabled Bandwidth Control, specify the maximum bandwidth limits for Upload in Mbps. The allowable range is from 0.1 through 99999. |
Bandwidth Control Options for Sub-Location (if Bandwidth Control is enabled on Parent Location)

Note: The following bandwidth control options are configurable for sub-location only if you have bandwidth control enabled on the parent location. If the bandwidth control is not enabled on the parent location, then the bandwidth control options for sub-location are the same as location (Bandwidth Control, Download, Upload).
|
|
| Use Location Bandwidth | If you have bandwidth control enabled on the parent location, select this option to enable bandwidth control on the sub-location and use the download and upload maximum bandwidth limits as specified for the parent location. |
| Override | Select this option to enable bandwidth control on the sub-location and then specify the maximum bandwidth limits for Download (Mbps) and Upload (Mbps). This bandwidth is dedicated to the sub-location and not shared with others. |
| Disabled | Select this option to exempt the traffic from any Bandwidth Management policies. Sub-location with this option can only use up to a maximum of available shared bandwidth at any given time. |
Limitations
- In 4.5.0 release, when a Sub-location is created, Orchestrator automatically saves the "Other" Sub-location. In earlier version of Orchestrator, the Zscaler "Other" Sub-location was not saved in Orchestrator. After upgrading Orchestrator to 4.5.0 release, the "Other" Sub-location will be imported automatically only after a new normal (non-Other) Sub-location is created using automation.
- Zscaler Sub-locations cannot have overlapping IP addresses (subnet IP ranges). Attempting to edit (add, update, or delete) multiple Sub-locations with conflicting IP addresses may cause the automation to fail.
- Users cannot update the bandwidth of Location and Sub-location at the same time.
- Sub-locations support Use Location Bandwidth option for bandwidth control when its Parent Location bandwidth control is enabled. When user turns off the Location bandwidth control on a Parent Location, the Orchestrator does not check or update the Sub-location bandwidth control option proactively.