You can configure additional properties and create API tokens for an Enterprise Admin user.
In the Enterprise portal, go to . To configure an Admin user, click the link to a username or select the user and click .
The existing properties of the selected Admin user are displayed and if required, you can add or modify the following:
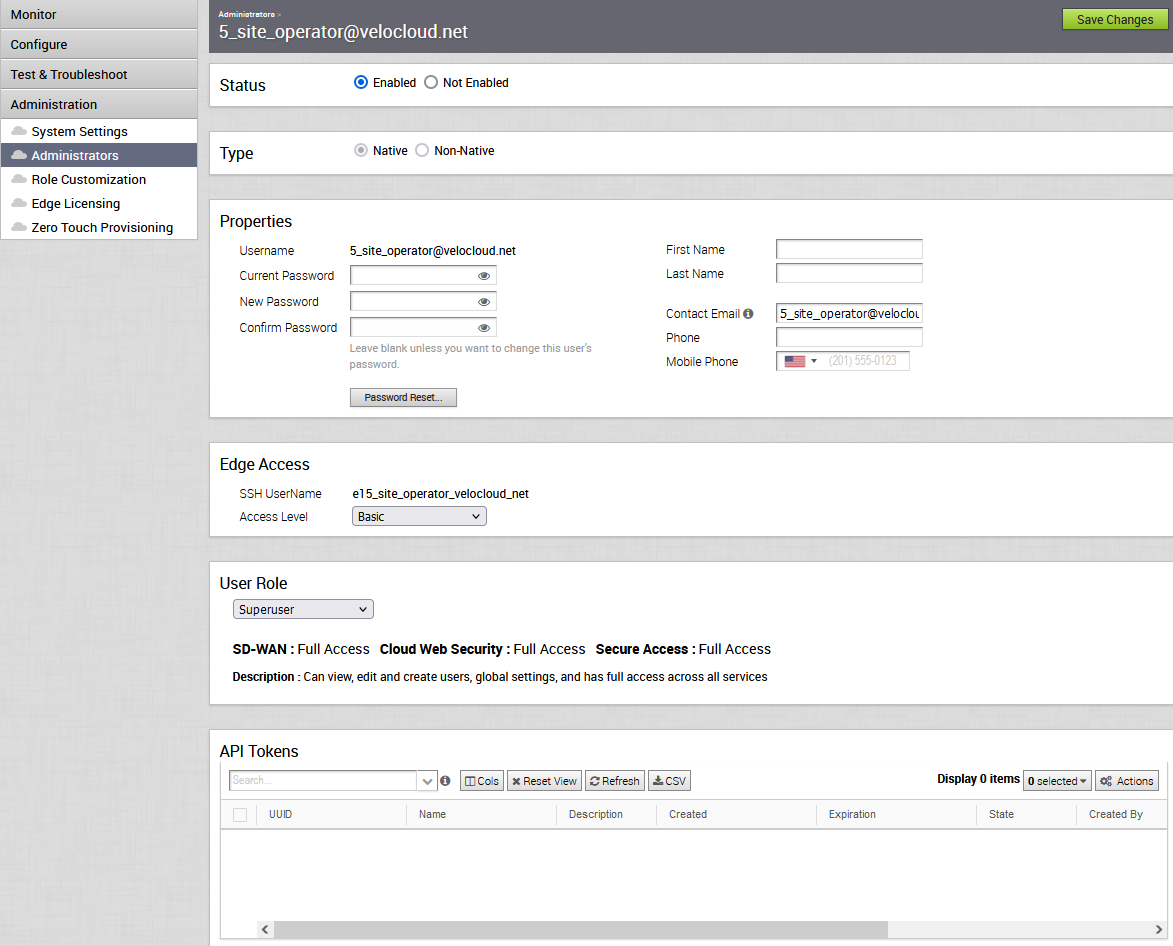
Status
By default, the status is in Enabled state. If you choose Not Enabled, the user is logged out of all the active sessions.
Type
If you have chosen the authentication mode as Native in the Configure Enterprise Authentication, then the type of the user is selected as Native. If you have chosen a different authentication mode, you can choose the type of the user. If you choose the user to be Non-Native, then you cannot reset the password or modify the user role.
Properties
- To set a new password, you must enter the current password correctly in the Current Password textbox and the password to be changed in New Password and Confirm Password textboxes.
- To reset the existing password, click Password Reset. An email is sent to the user with a link to reset the password.
Edge Access
- Basic—Allows the user to perform certain basic debug operations such as ping, tcpdump, pcap, remote diagnostics, and so on.
- Privileged—Grants the user root-level access to perform all basic debug operations along with Edge actions such as restart, deactivate, reboot, hard reset, and shutdown. In addition, the user can access linux shell.
Role
The existing type of the user role is displayed. If required, you can choose a different role for the user. The role privileges change accordingly.
API Tokens
The users can access the Orchestrator APIs using tokens instead of session-based authentication. As an Operator Super User, you can manage the API tokens for the customers. You can create multiple API tokens for a user.
For Enterprise Read Only Users and MSP Business Specialist users, token-based authentication is not enabled.
Configure API Tokens
Any user can create tokens based on the privileges they have been assigned to their user roles, except the Enterprise Read-Only users and MSP Business Specialist users.
The users can perform the following actions, based on their roles:
- Enterprise users can Create, Download, and Revoke tokens for them.
- Operator Super users can manage tokens of other Operator users and Enterprise users, if the Enterprise user has delegated user permissions to the Operator.
- Enterprise Super users can manage the tokens of all the users within that Enterprise.
- Users can download only their own tokens and cannot download other users' tokens.
- Super users can only create and revoke the tokens for other users.
Manage API Tokens
- In the API Tokens section, click , to create a new token.
- In the New API Token window, enter a Name and Description for the token, and choose the Lifetime from the drop-down menu.
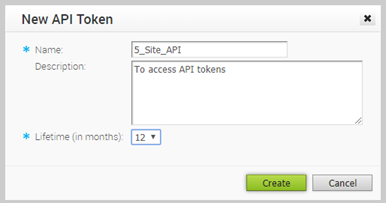
- Click Create and the new token is displayed in the API Tokens grid.
- Initially, the status of the token is displayed as Pending. To download the token, select the token, and click . The status changes to Enabled, which means that the API token can be used for API access.
- To deactivate a token, select the token and click . The status of the token is displayed as Revoked.
- When the Lifetime of the token is over, the status changes to Expired state.
Only the user who is associated with a token can download it and after downloading, the ID of the token alone is displayed. You can download a token only once.
After downloading the token, the user can send it as part of the Authorization Header of the request to access the Orchestrator API.
The following example shows a sample snippet of the code to access an API.
curl -k -H "Authorization: Token <Token>"
-X POST https://vco/portal/
-d '{ "id": 1, "jsonrpc": "2.0", "method": "enterprise/getEnterpriseUsers", "params": { "enterpriseId": 1 }}'
After modifying the settings and API Tokens, click Save Changes.