Enterprises can take advantage of secure local Internet breakout by using VMware SD-WAN integrated with Zscaler. Using VMware SD-WAN, the network administrator can decide what traffic should be forwarded to Zscaler, using IPsec tunnels (with NULL encryption).
Prerequisites
- Zscaler Internet Access (ZIA)
- A working instance of ZIA (any cloud)
- Administrator login credentials
- VMware SASE Orchestrator
- Enterprise account access to VMware SASE Orchestrator
- Administrator login credentials
- One or more VMware SD-WAN Edge appliances with “Online” status in VMware SASE Orchestrator
Zscaler SD-WAN Gateway Selection and Routing Behavior
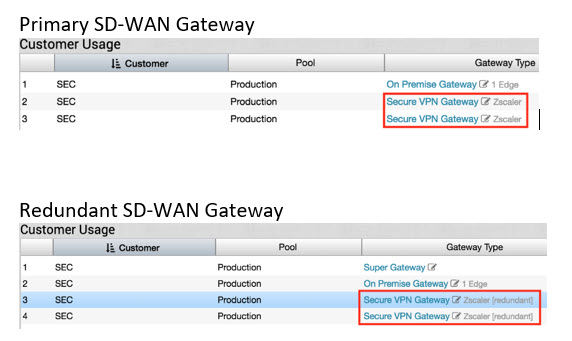
To set the Zscaler tunnel to a specific SD-WAN Gateway, you must first locate which SD-WAN Gateway has the tunnel by following the process above. From there you can click on “Secure VPN Gateway” and move/assign the tunnel to a different SD-WAN Gateway.
- Locate current tunnel location.
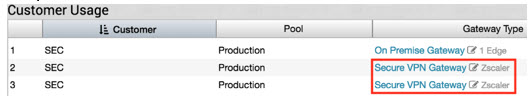
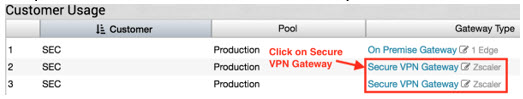
- Click on Secure VPN Gateway.
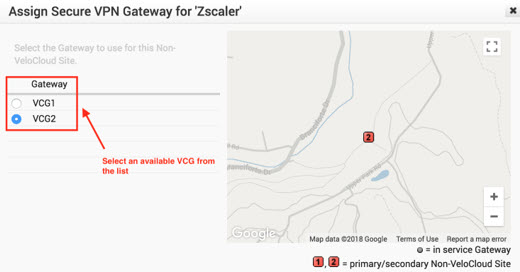
- Select a SD-WAN Gateway.
 Note: Assigning/Moving a tunnel to a different SD-WAN Gateway is service affecting. The existing tunnel connection will terminate and a new tunnel from the newly assigned SD-WAN Gateway will be established.
Note: Assigning/Moving a tunnel to a different SD-WAN Gateway is service affecting. The existing tunnel connection will terminate and a new tunnel from the newly assigned SD-WAN Gateway will be established.During the VMware SD-WAN Edge configuration/activation process, each Edge is assigned a pair of cloud SD-WAN Gateways or a set of Partner SD-WAN Gateways, in accordance with the device configuration. If the SD-WAN Gateways used by the Edge are not the same SD-WAN Gateways which contain the Zscaler tunnels, the Edge will automatically build VCMP tunnels to the SD-WAN Gateways that connect to Zscaler in addition to the SD-WAN Gateways that are selected during the activation process. This ensures the Edge has a path to reach Zscaler.
Zscaler Setup Examples
Example 1: Primary Zscaler tunnel to 1.1.1.1 with NO Redundant Velocloud Cloud VPN Selected
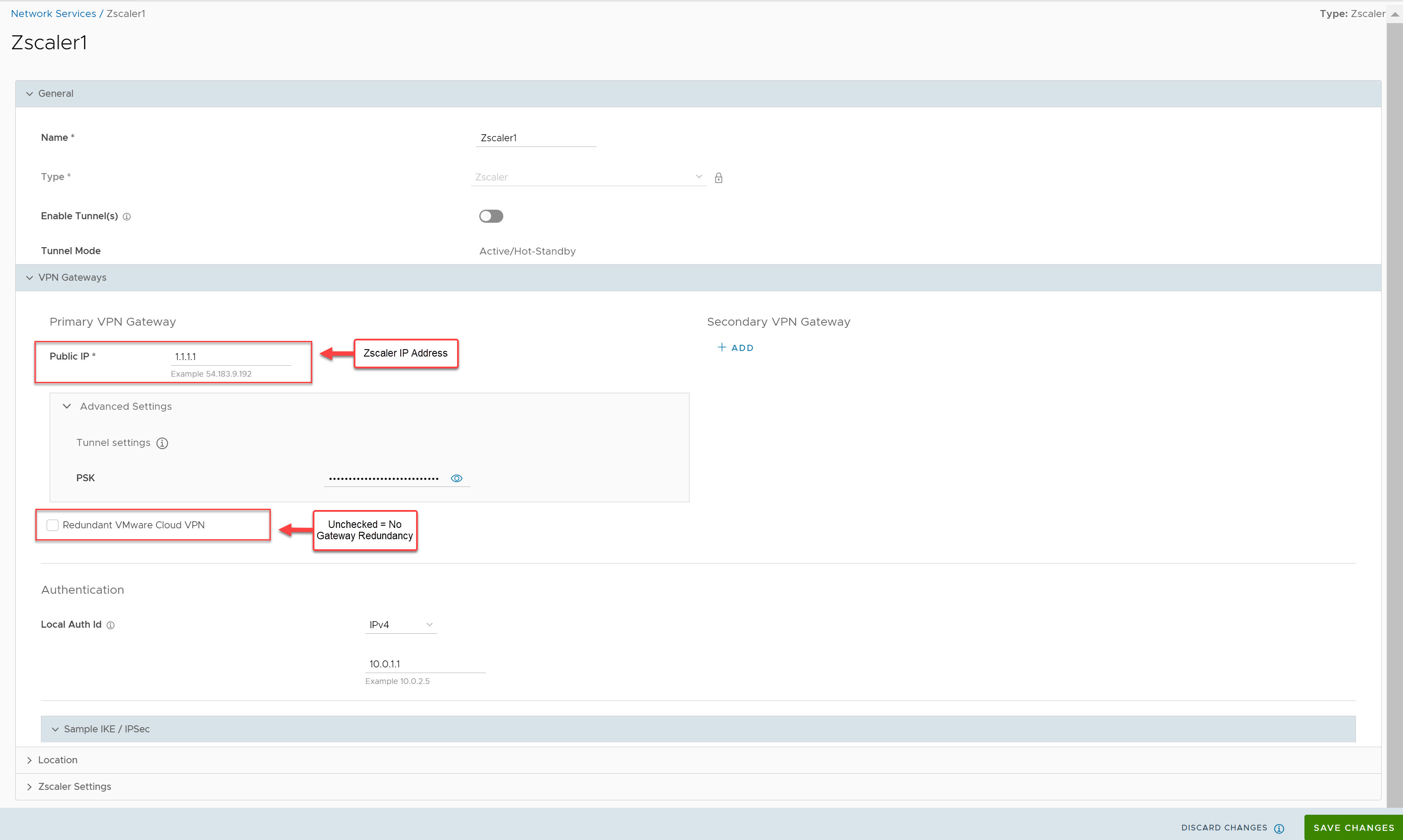
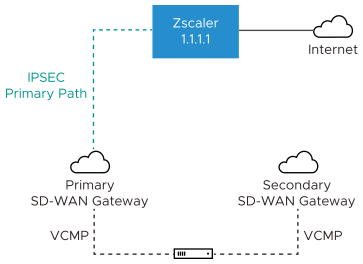
In this example, only one Zscaler VPN tunnel is created, and the Redundant Velocloud Cloud VPN checkbox is not selected. A single Gateway (Primary SD-WAN Gateway in this case) selected based on the proximity to the remote VPN Gateway (as determined via Geo-IP lookup), will create an IPsec tunnel to the Zscaler VPN endpoint. Dependent on Business Policy configuration, traffic will flow from the SD-WAN Edge, to the Primary SD-WAN Gateway and then on to Zscaler. Even though the SD-WAN Edge always has VCMP tunnels to at least two SD-WAN Gateways, there is no redundancy in this design. Since the Redundant Velocloud Cloud VPN checkbox is not selected, there will not be a backup SD-WAN Gateway tunnel to Zscaler. If either Zscaler or the primary SD-WAN Gateway fails or if the IPsec tunnel between the two goes down for any reason traffic to Zscaler will be dropped.
Example 2: Primary Zscaler tunnel to 1.1.1.1 with Redundant Velocloud Cloud VPN Selected
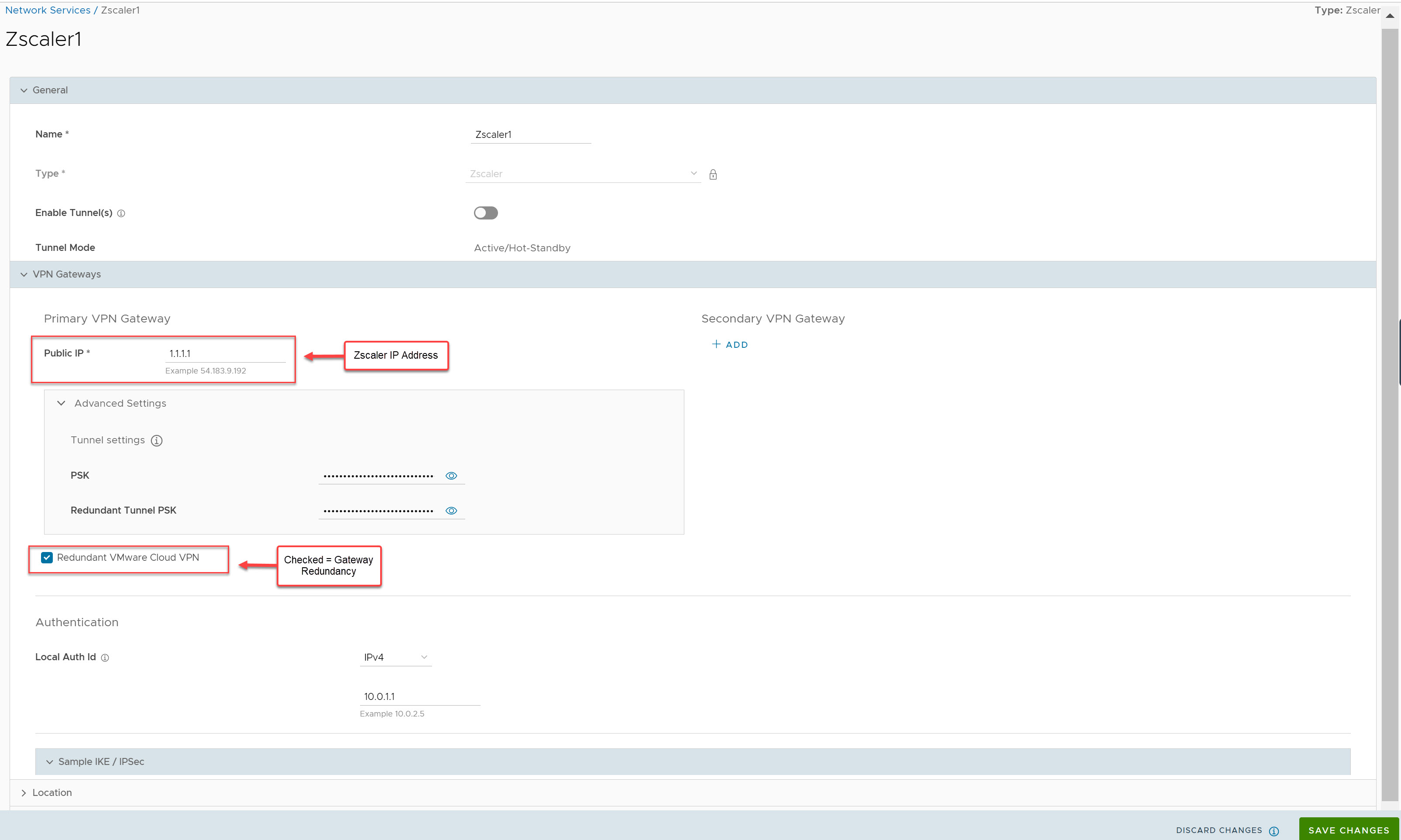
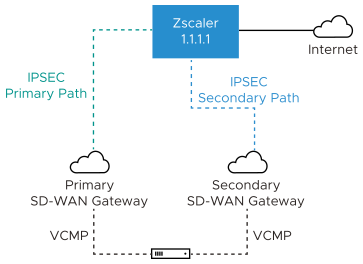
In this example, only one Zscaler VPN tunnel is created, and the Redundant Velocloud Cloud VPN checkbox is selected. Two SD-WAN Gateways selected based on the proximity to the remote VPN Gateway (as determined via Geo-IP lookup) that are the closest to the Zscaler location will build IPsec tunnels to Zscaler. Both of these tunnels are active, however all traffic to Zscaler will traverse through the Primary SD-WAN Gateway. If the Primary SD-WAN Gateway fails traffic will then shift to the Secondary SD-WAN Gateway. Since only a single Zscaler endpoint is defined if it goes down traffic to Zscaler will be dropped.
Example 3: Primary Zscaler tunnel to 1.1.1.1, Secondary Zscaler tunnel to 2.2.2.2 with NO Redundant Velocloud Cloud VPN Selected
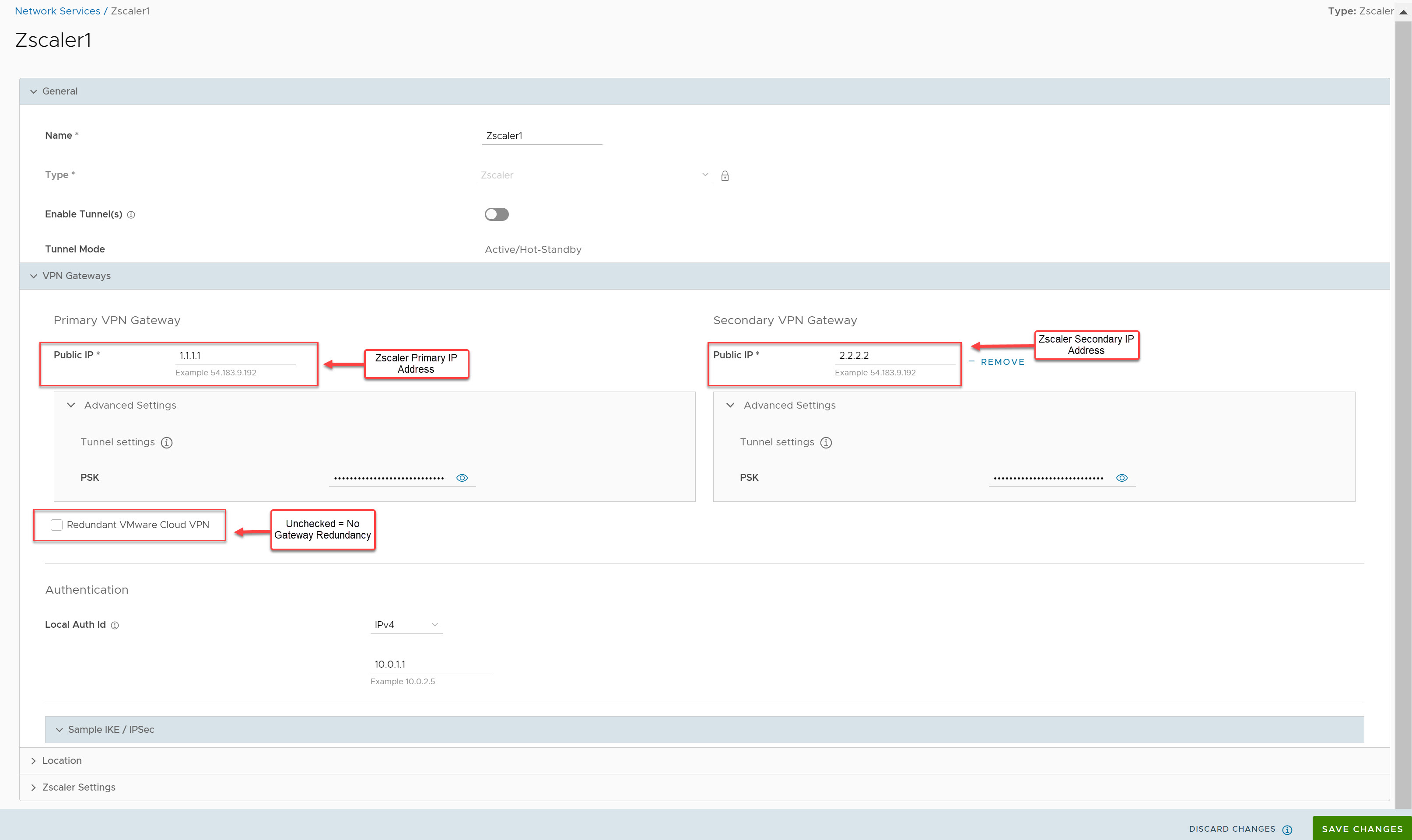
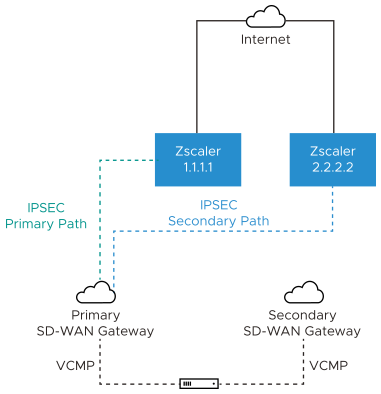
In this example, redundant IPsec tunnels to Zscaler are configured in the SASE Orchestrator by adding a secondary Zscaler IP address, however Redundant Velocloud Cloud VPN checkbox is not selected. A single SD-WAN Gateway selected based on the proximity to the remote VPN Gateway (as determined via Geo-IP lookup), will create an IPsec tunnel to both Zscaler VPN endpoints. Both of these tunnels are active, but by configuration settings the SD-WAN Gateway knows which IPsec tunnel to Zscaler is the primary path and will send traffic through that tunnel. Zscaler does not mark primary or backup IPsec tunnels. Zscaler will simply return traffic via the SD-WAN Gateway that originated the request. Should the primary Zscaler location go down, traffic from the SD-WAN Gateway will shift to the secondary Zscaler IPsec tunnel. Since the Redundant Velocloud Cloud VPN checkbox is not selected, there are no redundant SD-WAN Gateway connections to Zscaler. If the SD-WAN Gateway fails, then traffic to Zscaler will be dropped.
Example 4: Primary Zscaler tunnel to 1.1.1.1 , Secondary Zscaler tunnel to 2.2.2.2 with Redundant Velocloud VPN Selected
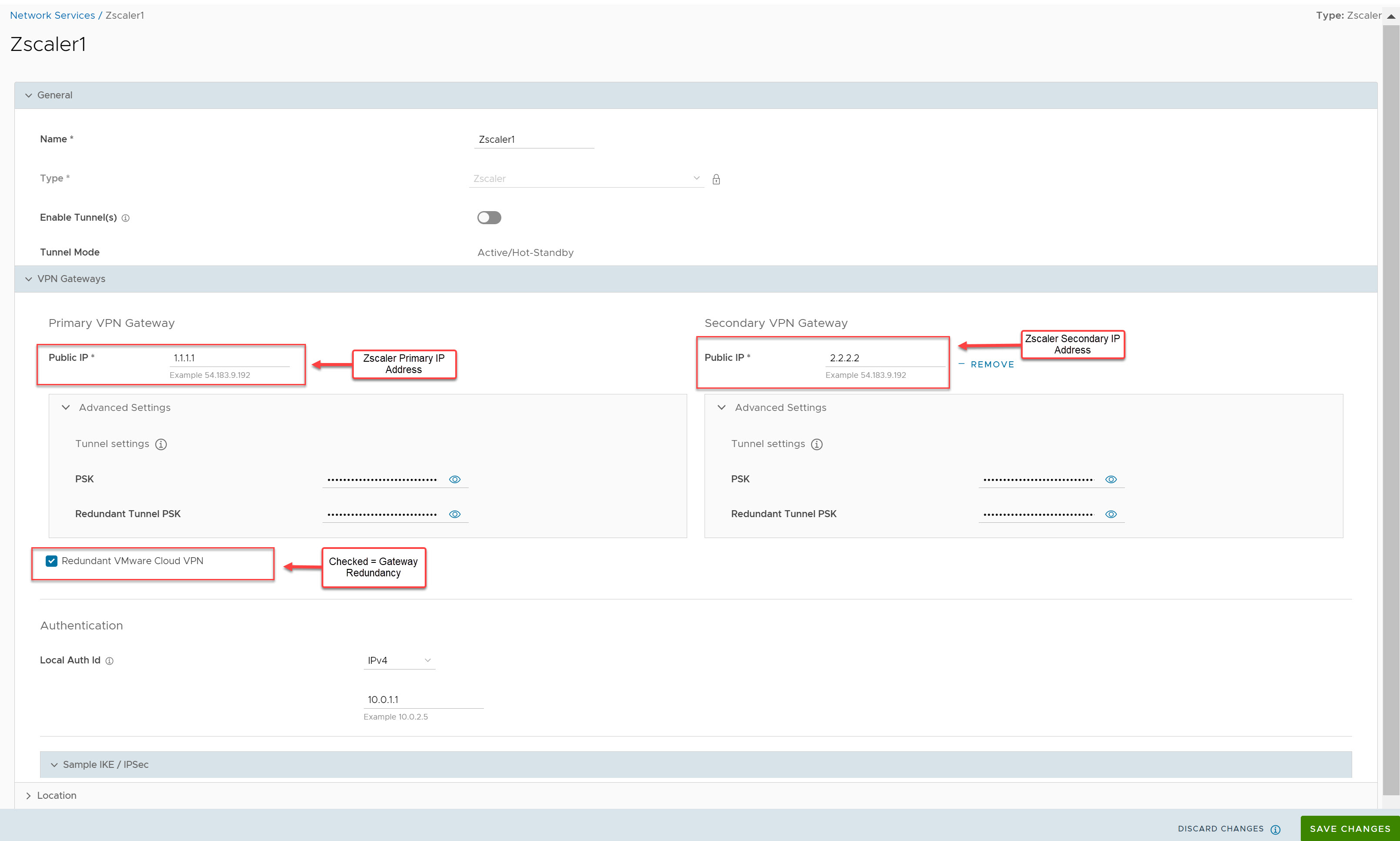
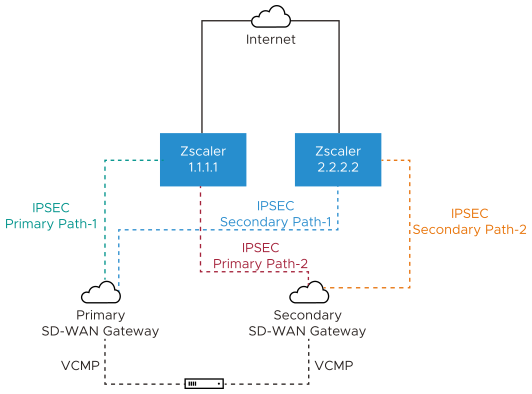
In this example, redundant IPsec tunnels to Zscaler are configured in the SASE Orchestrator by adding a secondary Zscaler IP address and Redundant Velocloud Cloud VPN checkbox is selected. Two SD-WAN Gateways selected based on the proximity to the remote VPN Gateway (as determined via Geo-IP lookup), will create IPsec tunnels to both Zscaler VPN endpoints. All of these tunnels are active, but by configuration settings the SD-WAN Gateways knows which of the two is the primary SD-WAN Gateway and which is secondary. The SD-WAN Gateways also know which of their IPsec tunnels to Zscaler is the primary path and which is the secondary path. Zscaler does not mark primary or backup IPsec tunnels. Zscaler will simply return traffic via the SD-WAN Gateway that originated the request. Should the primary Zscaler location go down, traffic from the primary SD-WAN Gateway will shift to the secondary Zscaler IPsec tunnel. Since the Redundant Velocloud Cloud VPN checkbox is selected, if the primary SD-WAN Gateway fails traffic will shift to the secondary SD-WAN Gateway. The secondary SD-WAN Gateway will utilize the primary IPsec tunnel provided that path is available. If not, it will use the secondary IPsec tunnel to reach Zscaler.
Layer 7 Health Checks
When you establish an IPsec/GRE tunnel to a given Zscaler datacenter for Zscaler Internet Access (ZIA), the tunnel is established between the SD-WAN Edge or SD-WAN Gateway, to a virtual IP (VIP) on a Zscaler load balancer for ZIA. When the end user traffic from the branch reaches the load balancer, the load balancer distributes traffic to ZIA Public Service Edges. Dead Peer Detection (DPD) and GRE keepalives can only detect the availability to the public VIP on the load balancer (since it is the tunnel destination). The public VIP is a highly available endpoint and does not reflect the availability of a given ZIA Public Service Edge. Layer 7 health checking allows you to monitor performance and availability of ZIA Edges based on HTTP probes and allows you to failover to an alternate tunnel based on the results. The SD-WAN Edge or SD-WAN Gateway sends probe requests periodically to the HTTP probe URL (in the following format) if probe is activated.
http://gateway.<zscaler_cloud>.net/vpntestThe probe URL is configurable in the SASE Orchestrator, but the probe interval and number of retries are currently not editable in the SASE Orchestrator. If the probe fails consecutively for the number of retries defined, the tunnel is marked down, and the traffic will failover to the secondary tunnel if defined. The probe failure could be either because the https response (200 OK) is not received, or the latency is greater than the defined threshold. If conditional backhaul is configured in an Edge, probe failures to both primary and secondary tunnel will trigger traffic failover to the backhaul hub configured. When the probe is UP again, traffic will fall back to the CSS tunnel. If Redundant Cloud VPN is configured for Non SD-WAN Destination (NSD) via Gateway, probe failures to both primary and secondary tunnel from primary gateway will trigger traffic failover to secondary gateway. When the probe in the primary gateway is UP again, traffic will fall back to the CSS tunnel on the primary gateway.
Zscaler and VMware SD-WAN Deployment Configurations
Describes the configuration steps for integrating Zscaler Internet Access (ZIA) and VMware SD-WAN:
- Configure Zscaler Internet Access (ZIA): Create an account, add VPN credentials, add a location.
- Create and Configure a Non SD-WAN Destination.
- Add a Non SD-WAN Destination to the Configuration Profile.
- Configure Business Priority Rules.
For more information, see https://www.zscaler.com/resources/solution-briefs/partner-vmware-sdwan-deployment-guide.pdf. This guide will provide GUI examples for configuring Zscaler Internet Access and VMware SASE Orchestrator.
Layer 7 health check Events
| Event | Displayed on Orchestrator UI as | Severity | Notification Configurable | Generated By | Generated When |
| EDGE_NVS_TUNNEL_UP | Edge Direct IPsec tunnel up | INFO | N | SASE Orchestrator | A Cloud Security Service tunnel or NSD via Edge tunnel is up. |
| EDGE_NVS_TUNNEL_DOWN | Edge Direct IPsec tunnel down | INFO | N | SASE Orchestrator | A Cloud Security Service tunnel or NSD via Edge tunnel is down. |
| VPN_DATACENTER_STATUS | VPN Tunnel state change | NOTICE | N | SD-WAN Gateway | The VPN Tunnel state is changed. |