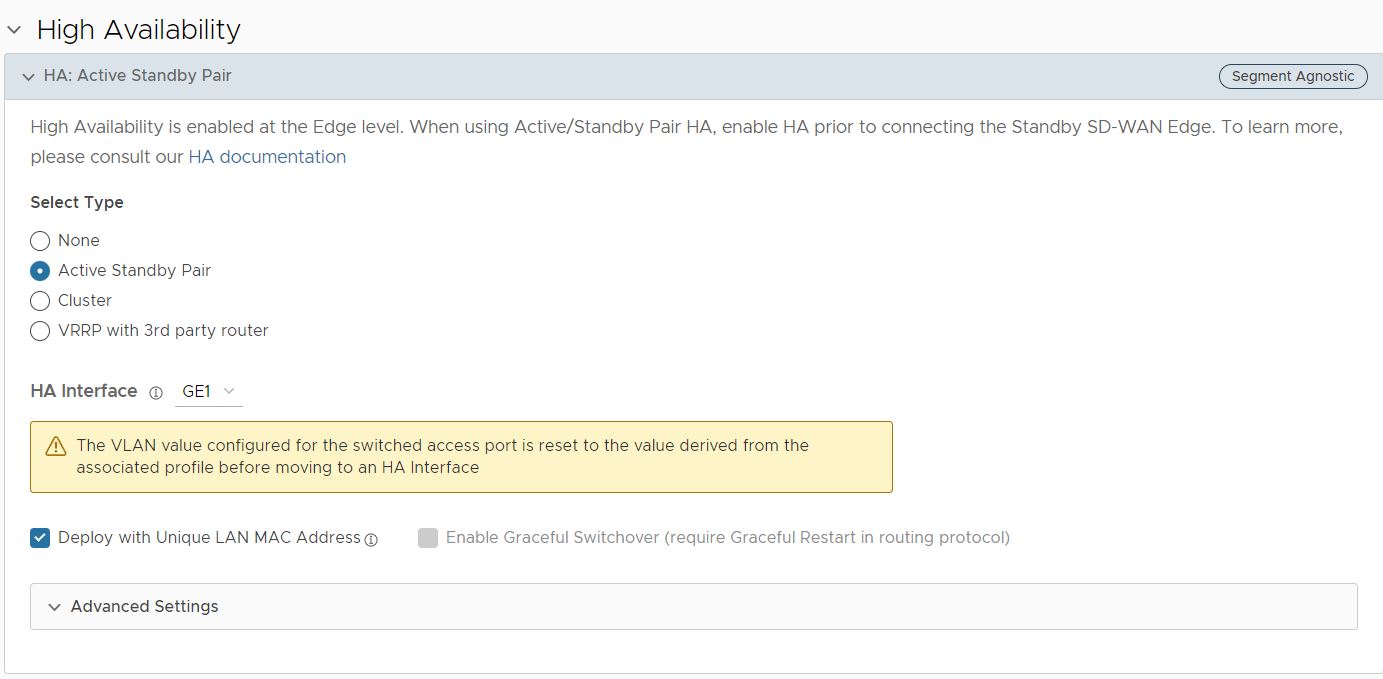
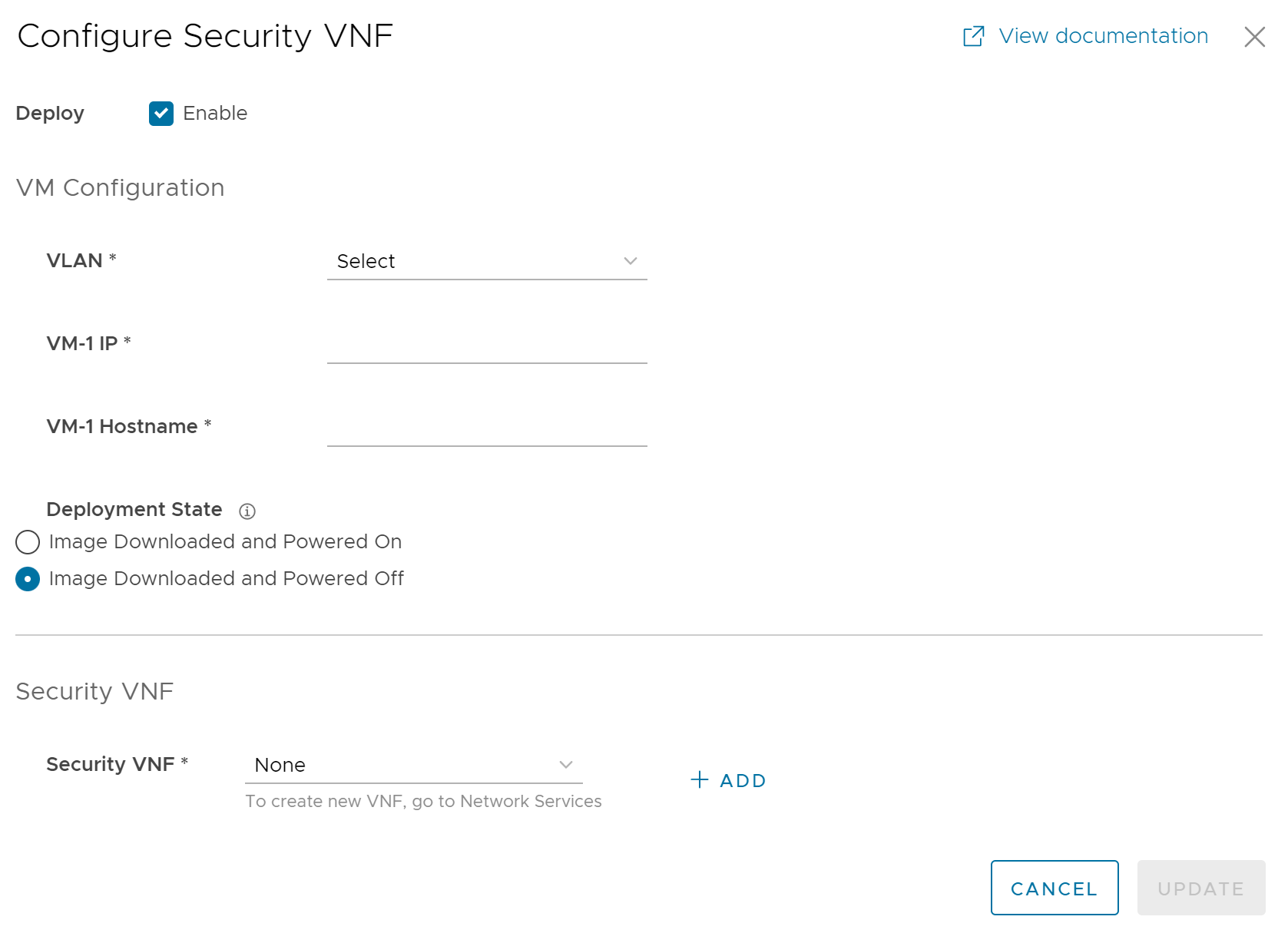
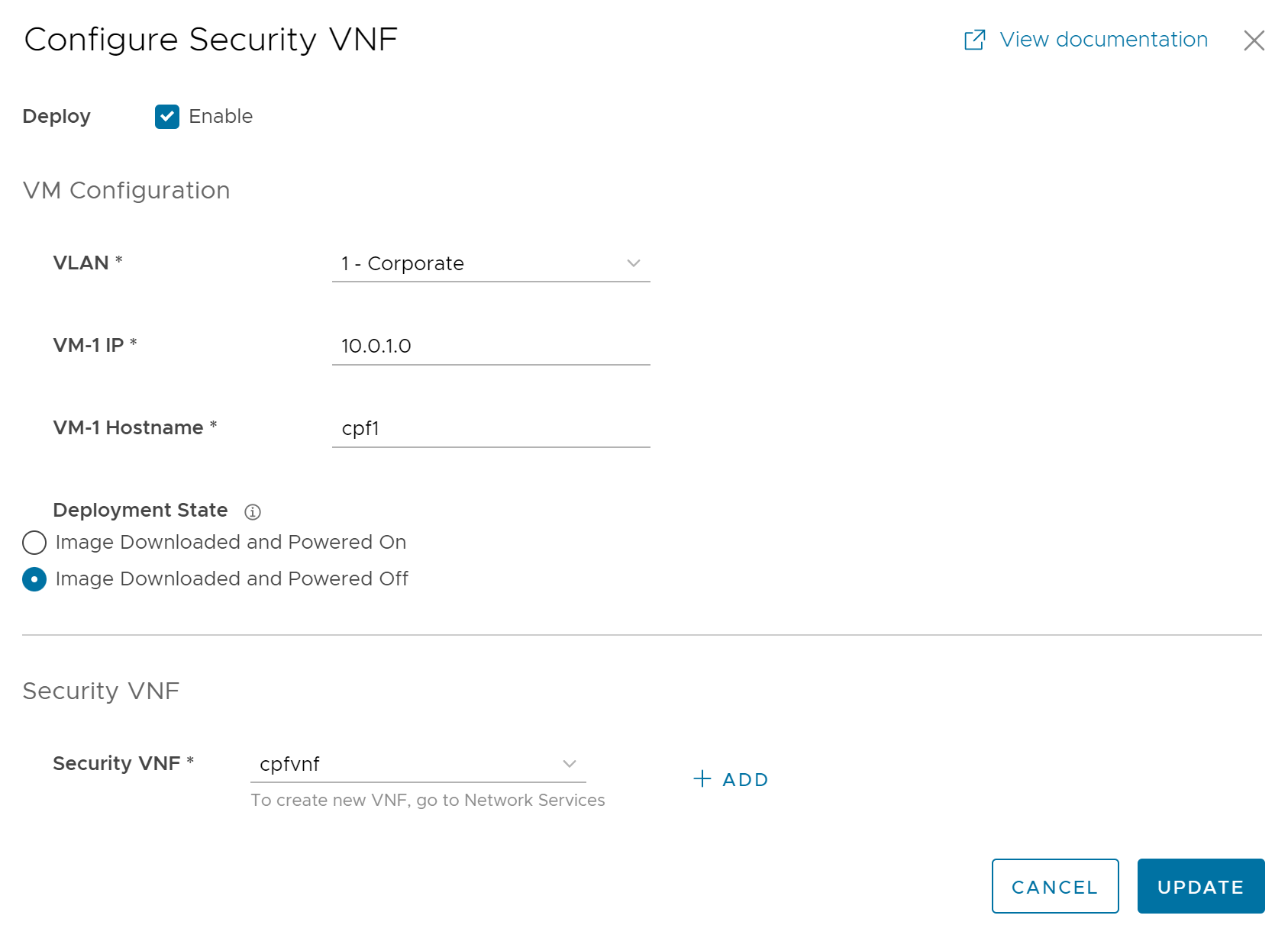
You can configure security VNF on Edges configured with High Availability to provide redundancy.
You can configure VNF with HA on Edges in the following scenarios:
- In a standalone Edge, enable HA and VNF.
- In Edges configured with HA mode, enable VNF.
The following interfaces are enabled and used between the Edge and VNF instance:
- LAN interface to VNF
- WAN interface to VNF
- Management Interface – VNF communicates with its manager
- VNF Sync Interface – Synchronizes information between VNFs deployed on Active and Standby Edges
The Edges have the HA roles as Active and Standby. The VNFs on each Edge run with Active-Active mode. The Active and Standby Edges learn the state of the VNF through SNMP. The SNMP poll is done periodically for every 1 second by the VNF daemon on the edges.
VNF is used in the Active-Active mode with user traffic forwarded to a VNF only from the associated Edge in Active mode. On the standby VM, where the Edge in the VM is standby, the VNF will have only traffic to the VNF Manager and data sync with the other VNF instance.
The following example shows configuring HA and VNF on a standalone Edge.
Prerequisites
Ensure that you have the following:
- SASE Orchestrator and activated SD-WAN Edge running software version 4.0.0 or later. For more information on the supported Edge platforms, refer to the Support Matrix in Security Virtual Network Functions.
- Configured Check Point Firewall VNF Management service. For more information, see Configure VNF Management Service.
Note: VMware supports only Check Point Firewall VNF on Edges with HA.
Procedure
Results
Wait till the Edge assumes the Active role and then connect the Standby Edge to the same interface of the Active Edge. The Standby Edge receives all the configuration details, including the VNF settings, from the Active Edge. For more information on HA configuration, see Activate High Availability.
When the VNF is down or not responding in the Active Edge, the VNF in the Standby Edge takes over the active role.
What to do next
If you want to redirect multiple traffic segments to the VNF, define mapping between Segments and service VLANs. See Define Mapping Segments with Service VLANs
You can insert the security VNF into both the VLAN as well as routed interface to redirect the traffic from the VLAN or the routed interface to the VNF. See Configure VLAN with VNF Insertion.