| Encryption |
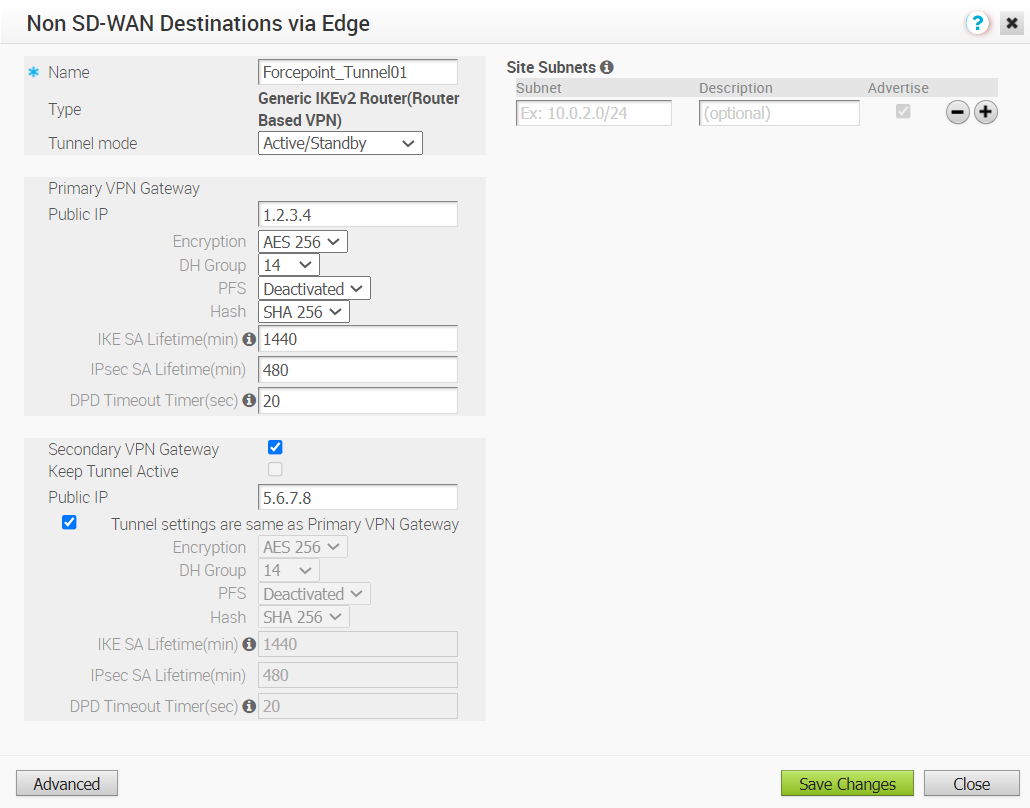
Select AES-256 as the AES algorithms key from the drop-down list, to encrypt data. |
| DH Group |
Select the Diffie-Hellman (DH) Group algorithm as 14, which would be used when exchanging the pre-shared key. The DH Group sets the strength of the algorithm in bits. |
| PFS |
Select the Perfect Forward Secrecy (PFS) level as Deactivated. |
| Hash |
Select the authentication algorithm for the VPN header as SHA 256 from the drop-down list. |
| IKE SA Lifetime(min) |
Enter the IKE SA lifetime in minutes. The rekeying should be initiated for Edges before the time expires. The range is from 10 to 1440 minutes. The default value is 1440 minutes. |
| IPsec SA Lifetime(min) |
Enter the IPsec SA lifetime in minutes. The rekeying should be initiated for Edges before the time expires. The range is from 3 to 480 minutes. The default value is 480 minutes. |
| DPD Timeout Timer(sec) |
Enter the DPD timeout value. The DPD timeout value will be added to the internal DPD timer, as described below. Wait for a response from the DPD message before considering the peer to be dead (Dead Peer Detection). Prior to the 5.1.0 release, the default value is 20 seconds. For the 5.1.0 release and later, see the list below for the default value.
- Library Name: Quicksec
- Probe Interval: Exponential (0.5 sec, 1 sec, 2 sec, 4 sec, 8 sec, 16 sec)
- Default Minimum DPD Interval: 47.5sec (Quicksec waits for 16 seconds after the last retry. Therefore, 0.5+1+2+4+8+16+16 = 47.5).
- Default Minimum DPD interval + DPD Timeout(sec): 67.5 sec
Note: Prior to the 5.1.0 release, you can deactivate DPD by configuring the DPD timeout timer to 0 seconds. However, for the 5.1.0 release and later, you cannot deactivate DPD by configuring the DPD timeout timer to 0 seconds. The DPD timeout value in seconds will get added onto the default minimum value of 47.5 seconds).
|