Creating and using custom posture policies in VMware Tanzu Platform hub
As an InfoSec analyst or administrator, you want to ensure that your resources have the correct configuration and remain configured over time to meet your organization’s security requirements. You can use the posture policies in Tanzu Platform hub to define, monitor, and report if a configuration does not match the defined policy.
When you onboard accounts into Tanzu Platform hub, all posture policies are automatically activated and begin running to generate findings. A finding from a security policy indicates a misconfiguration or vulnerability in your cloud resources that should be investigated and resolved. Posture policies are useful for catching and correcting misconfigurations that were already present in your accounts before onboarding, or to identify ongoing issues in business practices that may create vulnerabilities in your accounts.
Before you begin
- Verify that you have one or more cloud accounts onboarded in Tanzu Platform hub.
- Verify user roles and permissions. You must have administrator permissions to create custom posture policies.
Create a custom Security Posture policy
Custom posture policies are useful when you have a specific security need or vulnerability that isn’t covered by a Tanzu Platform hub native posture policy. In this situation you can create a custom policy to close the gap. For example, the native AWS security policies generate a finding when an IAM password is older than 90 days, but your organization may require renewing passwords earlier than that. The following steps demonstrate how to create a policy that checks for IAM passwords older than 60 days.
- In Tanzu Platform hub, click Cloud Account Policies.
- Click View (Posture policy) > New custom policy.
-
In the General information section, enter the primary attributes for the policy using the image below as a reference.
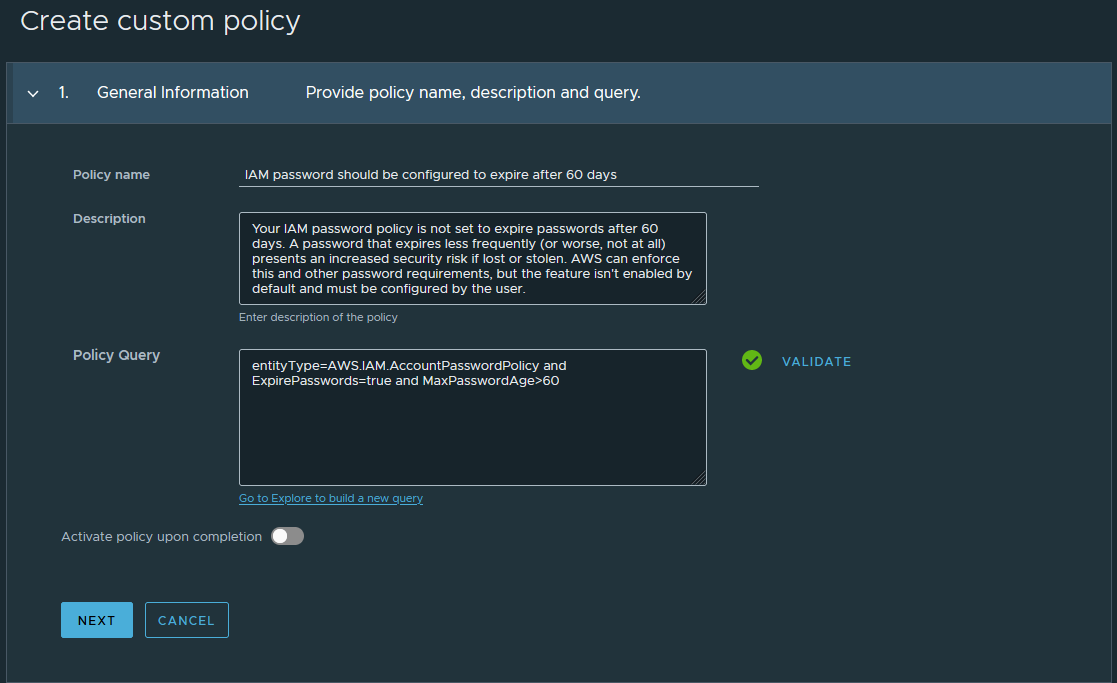
- To create the query in this example, select the 90-day version of the policy from GCloud Account Policies > Policies > View (Posture policy) and copy the string.
- Then, edit MaxPasswordAge>90 to the desired length.
- For more examples, see the How to create effective queries for your custom security policy section.
- Click Next.
-
In the Properties section, enter the metadata used to categorize and filter your policy. Refer to the image below for an example.
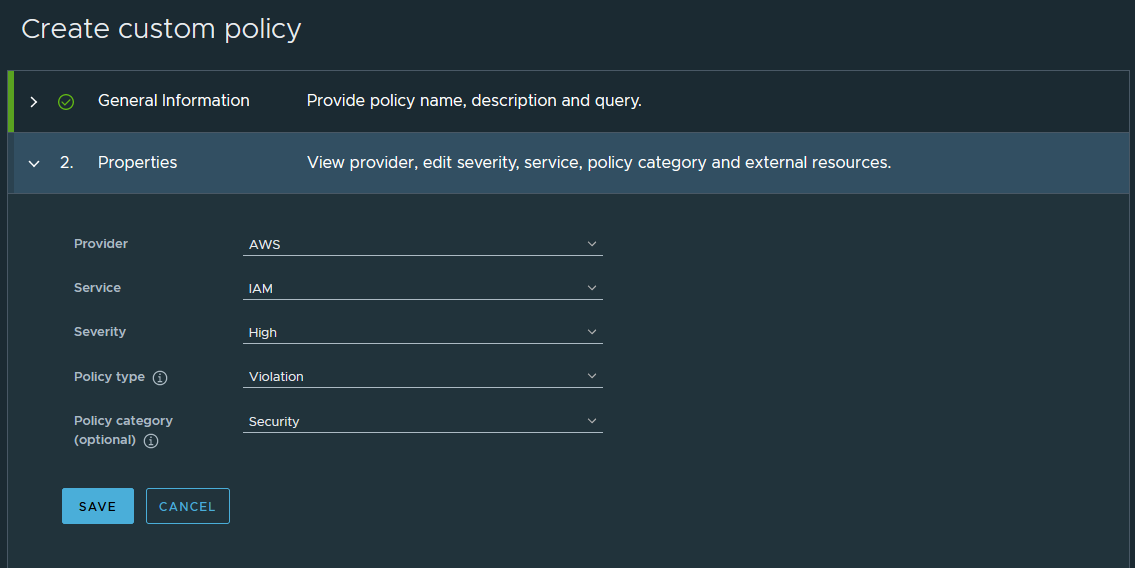
-
Click Save.
How to create effective queries for your custom security policy
Posture policies are structured as queries that represent misconfigurations and vulnerabilities in a cloud resource. Tanzu Platform hub runs these queries on your accounts and generates a finding whenever it detects a match. The key to building an effective query is to have a thorough understanding of how Simple Search Query Language works and testing the query before committing it to a custom policy.
Here are some examples of queries that can be used in custom security policies. To test a query, run it in the Explore section and see if you get any results. The amount of matched resources gives you an idea of how many findings you’d get from a custom policy using that query.
When you are running policy queries, you can save the query as a custom policy. To save the query, click Create a custom policy with this query.
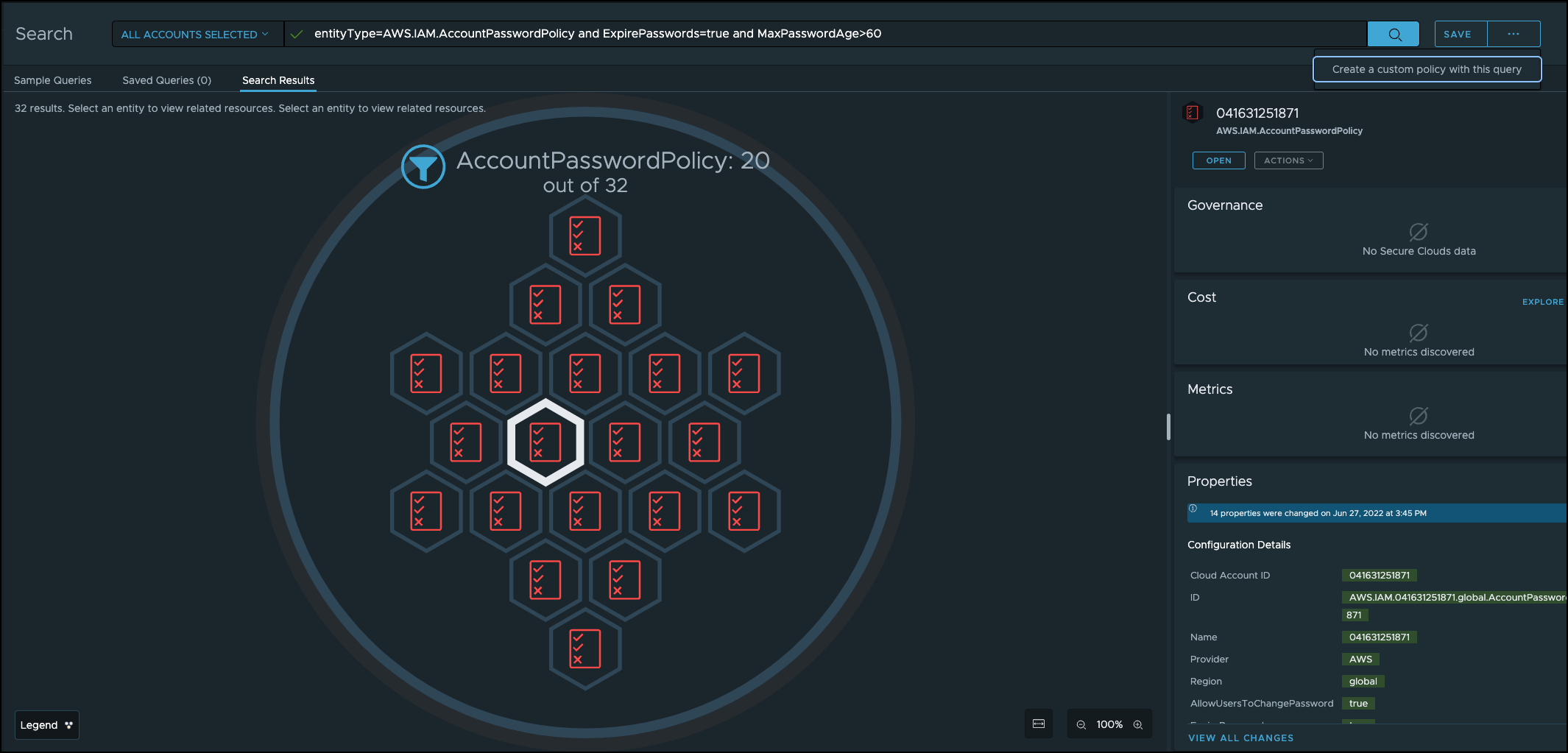
The following table includes sample policy queries that you can run.
| Policy query | Description |
|---|---|
|
Detects AWS security groups that allow public access over IPv4 on a specific port. When using, replace the
|
|
Provides the same function as the previous query, but for IPv6 traffic. |
|
Detects an active AWS EC2 instance attached to a security group that allows public access on a specific port. When using, replace the
|
|
Detects an Azure SQL database audit policy with a retention period in a defined range. Replace the
RetentionDays<120 if you want audit logs retained for 120 days or more.
|
|
Provides the same function as the previous query, but for Advanced Threat Protection logs. |
|
Detects an Azure PostgreSQL Server that retains log files for a minimum number days. The default query generates a finding on a server that retains logs for 3 days or less, but you can adjust this by removing or adding values to the list at the end of the query. For example, Value != (“6”, “7”) detects servers retaining logs for five days or less. |
Create a Spring policy
Spring policies enforce organizational standards and best practices on application code detected in your repositories.
- In Tanzu Platform hub, click Policies > Spring Policies.
- Click New policy.
-
In the General information section, enter the primary attributes for the policy using the image below as a reference.
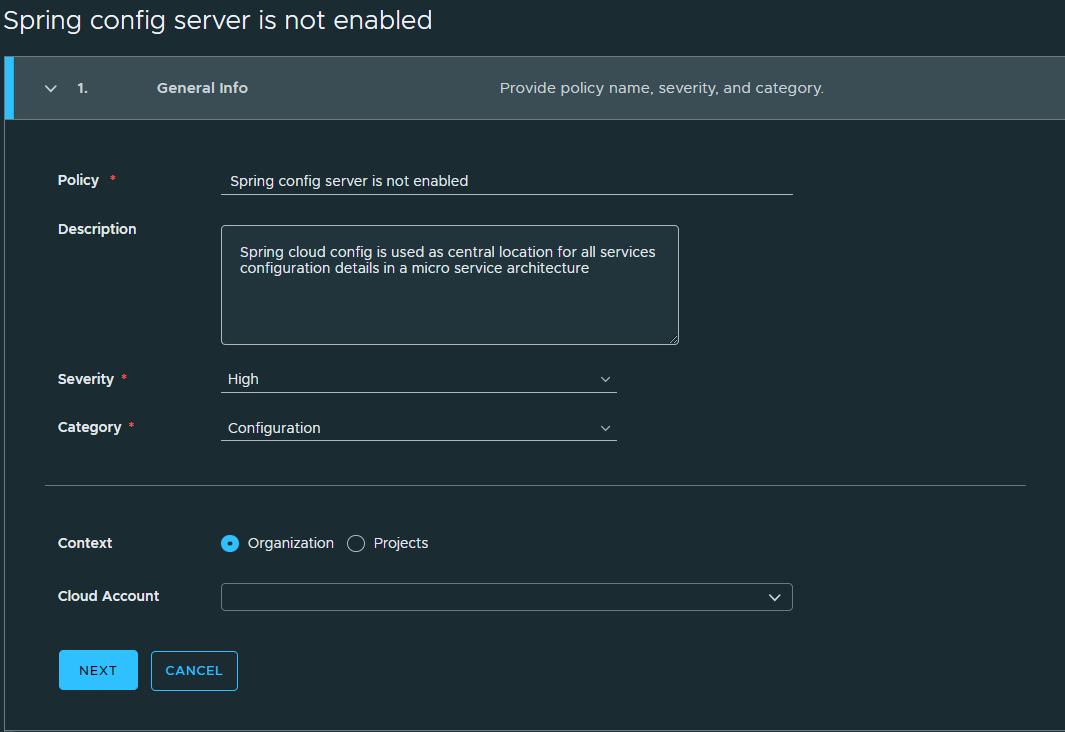
- Select whether the policy should apply at the organization or project context.
- If you choose the project context, enter the cloud accounts the policy should monitor.
- Click Next.
-
In the Rule section, enter conditions to define the criteria you want your Spring policy to evaluate using the image below as a reference.
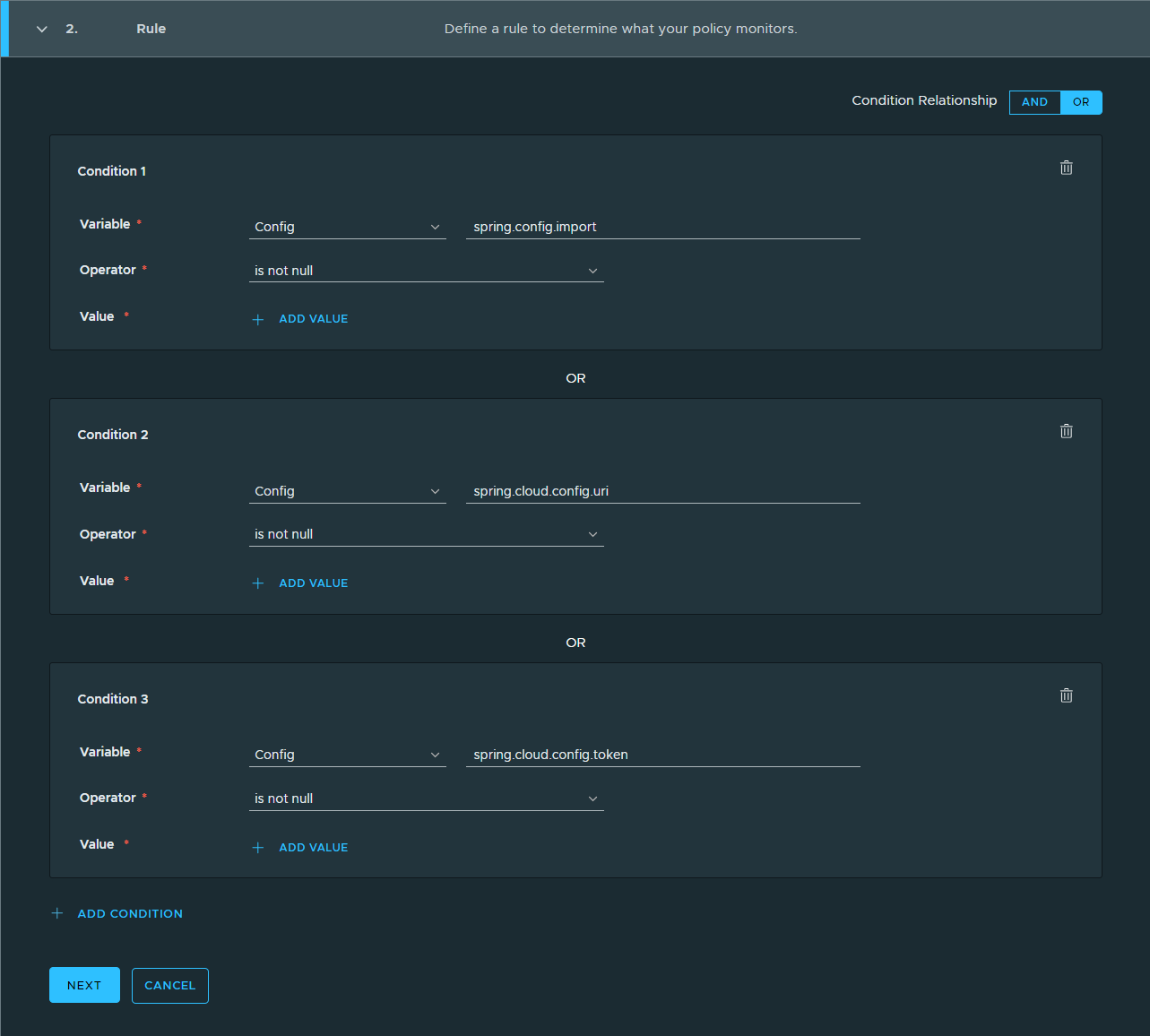
-
Click Next.
-
In the Schedule section, select the cadence at which you want the policy to scan your repositories. The policy won’t run unless you set it to Active.
-
Click Save.
Parent topic:Define and apply governance policies in VMware Tanzu Platform hub